Tax-having to pay people in Mexico and Chile have been qualified by a Mexico-primarily based cybercrime group that goes by the title Fenix to breach qualified networks and steal worthwhile knowledge.
A critical hallmark of the procedure involves cloning official portals of the Servicio de Administración Tributaria (SAT) in Mexico and the Servicio de Impuestos Internos (SII) in Chile and redirecting likely victims to individuals web pages.
“These faux web-sites prompt consumers to obtain a intended security tool, professing it will increase their portal navigation protection,” Metabase Q security scientists Gerardo Corona and Julio Vidal mentioned in a the latest evaluation.
“However, unbeknownst to the victims, this down load actually installs the first phase of malware, in the long run enabling the theft of delicate information and facts such as credentials.”
The target of Fenix, according to the Latin America-concentrated cybersecurity firm, is to act as an preliminary entry broker and get a foothold into different corporations in the region, and sell the access to ransomware affiliate marketers for further more monetization.
Proof collected so much points to the danger actor orchestrating phishing campaigns coinciding with government things to do all through the year considering the fact that at least the fourth quarter of 2022.
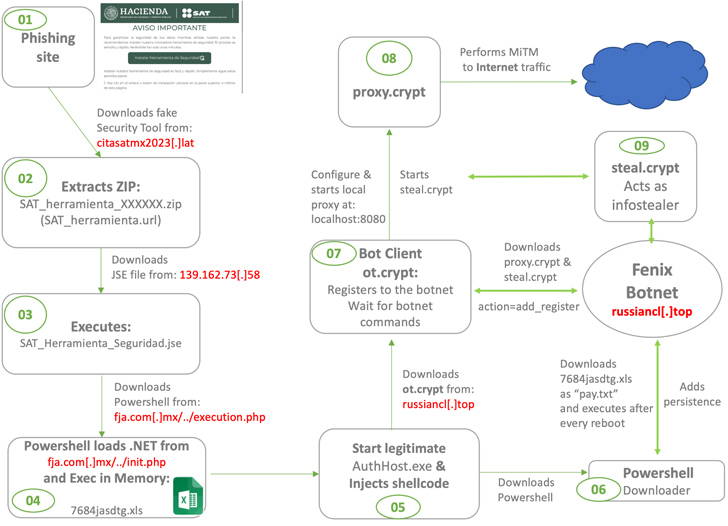
The mechanics of the marketing campaign proceeds hence: Site visitors landing on the impersonated websites are urged to download application that supposedly safeguards their info whilst browsing the portal. Alternatively, users are lured by means of phishing web sites set up to download reputable apps like AnyDesk.
“[Fenix] compromises weak web-sites utilizing vulnerable WordPress engines and also creates new domains to start phishing strategies,” the scientists mentioned, incorporating the team “results in typosquatting domains similar to regarded applications like AnyDesk, WhatsApp, and so forth.”
Approaching WEBINARShield Versus Insider Threats: Learn SaaS Security Posture Administration
Worried about insider threats? We have bought you covered! Be a part of this webinar to examine practical procedures and the tricks of proactive security with SaaS Security Posture Administration.
Be a part of Now
But in reality, the ZIP file made up of the purported software package is used as a springboard to activate an an infection sequence that sales opportunities to the execution of an obfuscated PowerShell script, which, in flip, masses and runs a .NET binary, after which the concept “Ahora se encuentra protegido” (which means “Now you are guarded” in Spanish) is displayed to maintain up the ruse.
The .NET executable subsequently paves the way for creating persistence on the compromised host and deploying a botnet malware that is able of jogging instructions been given from a remote server, loading a stealer module that exfiltrates credentials saved in web browsers and crypto wallets, and in the long run deleting by itself.
“We are looking at new malicious teams getting established in LATAM to present first accessibility to ransomware gangs,” the researchers concluded. “These area actors are not beginner and will increase their technical skills and as a result extra tricky to monitor, detect and eradicate, it is vital to foresee their steps.”
Observed this article fascinating? Follow us on Twitter and LinkedIn to read much more distinctive written content we submit.
Some parts of this article are sourced from:
thehackernews.com


 New AI Tool ‘FraudGPT’ Emerges, Tailored for Sophisticated Attacks
New AI Tool ‘FraudGPT’ Emerges, Tailored for Sophisticated Attacks