A severity flaw impacting industrial cellular routers from Milesight may possibly have been actively exploited in genuine-planet attacks, new conclusions from VulnCheck reveal.
Tracked as CVE-2023-43261 (CVSS score: 7.5), the vulnerability has been explained as a case of information disclosure that has an effect on UR5X, UR32L, UR32, UR35, and UR41 routers ahead of version 35.3..7 that could allow attackers to obtain logs these as httpd.log as nicely as other delicate qualifications.
As a end result, this could permit distant and unauthenticated attackers to acquire unauthorized accessibility to the web interface, thereby creating it feasible to configure VPN servers and even drop firewall protections.
“This vulnerability turns into even much more critical as some routers allow for the sending and obtaining of SMS messages,” security researcher Bipin Jitiya, who found the issue, mentioned before this thirty day period. “An attacker could exploit this functionality for fraudulent routines, perhaps causing money harm to the router owner.”

Now, in accordance to VulnCheck’s Jacob Baines, there is evidence that the flaw may have been exploited on a compact-scale in the wild.
“We observed 5.61.39[.]232 trying to log into 6 methods on October 2, 2023,” Baines explained. “The influenced systems’ IP addresses geolocate to France, Lithuania, and Norway. They do not show up to be associated, and all use different non-default qualifications.”
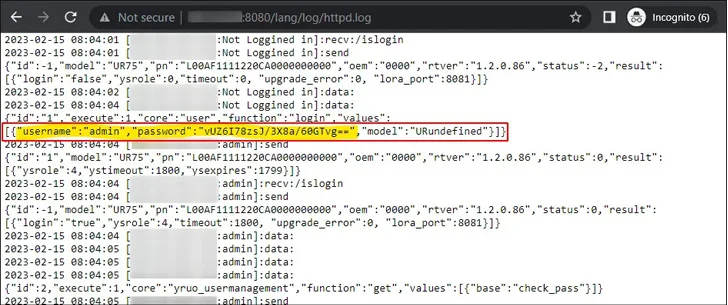
On four of the six devices, the threat actor is reported to have efficiently authenticated on the first endeavor. On the fifth program, the login was productive the 2nd time, and on the sixth, the authentication resulted in failure.
The credentials made use of to pull off the attack were extracted from the httpd.log, alluding to the weaponization of CVE-2023-43261. There is no proof of any even more malicious steps, whilst it seems that the not known actor checked the options and position webpages.
According to VulnCheck, although there are somewhere around 5,500 internet-uncovered Milesight routers, only about 5% are jogging vulnerable firmware versions, and consequently prone to the flaw.
“If you have a Milesight Industrial Mobile Router, it is almost certainly sensible to assume all the qualifications on the program have been compromised and to simply just create new types, and be certain no interfaces are reachable by using the internet,” Baines reported.
Six Flaws Learned in Titan MFT and Titan SFTP Servers

The disclosure arrives as Quick7 comprehensive various security flaws in South River Technologies’ Titan MFT and Titan SFTP servers that, if exploited, could allow distant superuser entry to impacted hosts.

The record of vulnerabilities is as follows –
- CVE-2023-45685 – Authenticated Remote Code Execution by way of “Zip Slip”
- CVE-2023-45686 – Authenticated Remote Code Execution via WebDAV Route Traversal
- CVE-2023-45687 – Session Fixation on Remote Administration Server
- CVE-2023-45688 – Information and facts Disclosure by way of Route Traversal on FTP
- CVE-2023-45689 – Details Disclosure by using Route Traversal in Admin Interface
- CVE-2023-45690 – Data Leak by means of Environment-Readable Database + Logs
“Productive exploitation of several of these issues grants an attacker distant code execution as the root or Technique person,” the enterprise mentioned. “On the other hand, all issues are submit-authentication and involve non-default configurations and are as a result not likely to see extensive scale exploitation.”
Observed this posting intriguing? Abide by us on Twitter and LinkedIn to read a lot more unique content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 CERT-UA Reports: 11 Ukrainian Telecom Providers Hit by Cyberattacks
CERT-UA Reports: 11 Ukrainian Telecom Providers Hit by Cyberattacks