Menace actors are leveraging bogus Fb career commercials as a entice to trick possible targets into putting in a new Windows-primarily based stealer malware codenamed Ov3r_Stealer.
“This malware is made to steal credentials and crypto wallets and send these to a Telegram channel that the danger actor displays,” Trustwave SpiderLabs mentioned in a report shared with The Hacker Information.
Ov3r_Stealer is able of siphoning IP address-dependent site, components information, passwords, cookies, credit card information and facts, vehicle-fills, browser extensions, crypto wallets, Microsoft Place of work documents, and a listing of antivirus merchandise set up on the compromised host.
Although the precise end objective of the marketing campaign is unfamiliar, it’s probably that the stolen information and facts is made available for sale to other menace actors. Yet another likelihood is that Ov3r_Stealer could be up-to-date around time to act as a QakBot-like loader for supplemental payloads, including ransomware.

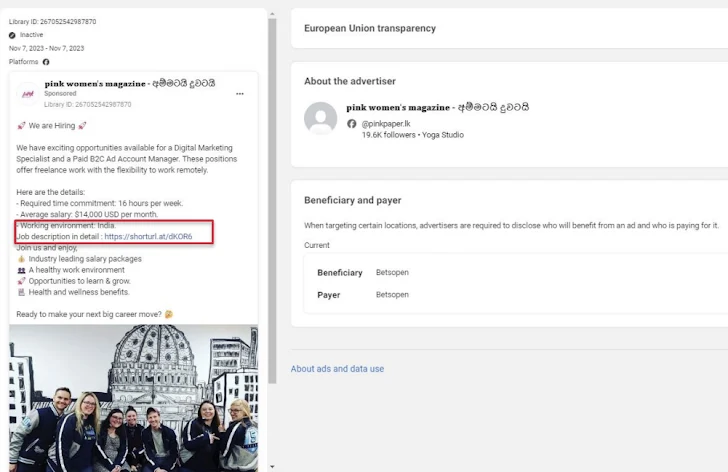
The starting off position of the attack is a weaponized PDF file that purports to be a file hosted on OneDrive, urging customers to simply click on an “Obtain Document” button embedded into it.
Trustwave mentioned it determined the PDF file becoming shared on a fake Facebook account impersonating Amazon CEO Andy Jassy as effectively as through Fb adverts for electronic marketing work.
People who end up clicking on the button are served an internet shortcut (.URL) file that masquerades as a DocuSign document hosted on Discord’s material shipping network (CDN). The shortcut file then acts as a conduit to deliver a control panel item (.CPL) file, which is then executed employing the Windows Manage Panel procedure binary (“management.exe”).
The execution of the CPL file qualified prospects to the retrieval of a PowerShell loader (“Knowledge1.txt”) from a GitHub repository to ultimately start Ov3r_Stealer.
It is really well worth noting at this phase that a near-similar an infection chain was recently disclosed by Craze Micro as acquiring place to use by menace actors to fall an additional stealer known as Phemedrone Stealer by exploiting the Microsoft Windows Defender SmartScreen bypass flaw (CVE-2023-36025, CVSS rating: 8.8).
The similarities increase to the GitHub repository applied (nateeintanan2527) and the fact that Ov3r_Stealer shares code-level overlaps with Phemedrone.
“This malware has just lately been documented, and it might be that Phemedrone was re-purposed and renamed to Ov3r_Stealer,” Trustwave stated. “The major variation concerning the two is that Phemedrone is written in C#.”

The results come as Hudson Rock discovered that risk actors are marketing their access to law enforcement ask for portals of major organizations like Binance, Google, Meta, and TikTok by exploiting credentials attained from infostealer infections.
They also stick to the emergence of a class of infections referred to as CrackedCantil that take leverage cracked application as an initial obtain vector to drop loaders like PrivateLoader and SmokeLoader, when subsequently act as a shipping mechanism for data stealers, crypto miners, proxy botnets, and ransomware.
Identified this post intriguing? Abide by us on Twitter and LinkedIn to study a lot more exceptional articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Experts Detail New Flaws in Azure HDInsight Spark, Kafka, and Hadoop Services
Experts Detail New Flaws in Azure HDInsight Spark, Kafka, and Hadoop Services