An innovative persistent threat (APT) actor recognised as Dragon Breath has been observed including new layers of complexity to its attacks by adopting a novel DLL side-loading system.
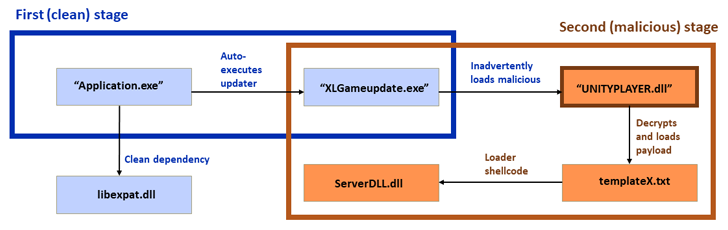
“The attack is primarily based on a classic side-loading attack, consisting of a clean software, a malicious loader, and an encrypted payload, with a variety of modifications created to these parts around time,” Sophos researcher Gabor Szappanos mentioned.
“The most recent strategies insert a twist in which a 1st-phase clear application ‘side’-hundreds a 2nd clean up software and automobile-executes it. The second clean up software side-loads the destructive loader DLL. After that, the destructive loader DLL executes the final payload.”
Procedure Dragon Breath, also tracked beneath the names APT-Q-27 and Golden Eye, was 1st documented by QiAnXin in 2020, detailing a watering hole marketing campaign developed to trick users into downloading a trojanized Windows installer for Telegram.

A subsequent campaign in-depth by the Chinese cybersecurity firm in May perhaps 2022 highlighted the ongoing use of Telegram installers as a entice to deploy added payloads these kinds of as gh0st RAT.
Dragon Breath is also claimed to be element of a larger entity identified as Miuuti Team, with the adversary characterised as a “Chinese-speaking” entity focusing on the on the net gaming and gambling industries, joining the likes of other Chinese action clusters like Dragon Castling, Dragon Dance, and Earth Berberoka.
The double-dip DLL aspect-loading approach, per Sophos, has been leveraged in attacks focusing on buyers in the Philippines, Japan, Taiwan, Singapore, Hong Kong, and China. These tried intrusions were being ultimately unsuccessful.
The original vector is a faux web page hosting an installer for Telegram that, when opened, creates a desktop shortcut that’s created to load malicious components guiding the scenes upon start, although also displaying to the victim the Telegram application consumer interface.
What is actually much more, the adversary is believed to have created many versions of the scheme in which tampered installers for other applications, these kinds of as LetsVPN and WhatsApp, are used to initiate the attack chain.
Upcoming WEBINARLearn to Stop Ransomware with Actual-Time Defense
Join our webinar and discover how to stop ransomware attacks in their tracks with authentic-time MFA and support account protection.
Conserve My Seat!
The up coming stage includes the use of a 2nd clean application as an intermediate to stay clear of detection and load the ultimate payload by way of a malicious DLL.
The payload features as a backdoor able of downloading and executing documents, clearing celebration logs, extracting and location clipboard written content, jogging arbitrary commands, and stealing cryptocurrency from the MetaMask wallet extension for Google Chrome.
“DLL sideloading, very first identified in Windows goods in 2010 but commonplace throughout several platforms, continues to be an successful and attractive tactic for threat actors,” Szappanos claimed.
“This double-thoroughly clean-application strategy utilized by the Dragon Breath group, targeting a user sector (on line gambling) that has customarily been considerably less scrutinized by security scientists, represents the continued vitality of this solution.”
Discovered this post intriguing? Comply with us on Twitter and LinkedIn to read through more distinctive information we post.
Some parts of this article are sourced from:
thehackernews.com


 New Vulnerability in Popular WordPress Plugin Exposes Over 2 Million Sites to Cyberattacks
New Vulnerability in Popular WordPress Plugin Exposes Over 2 Million Sites to Cyberattacks