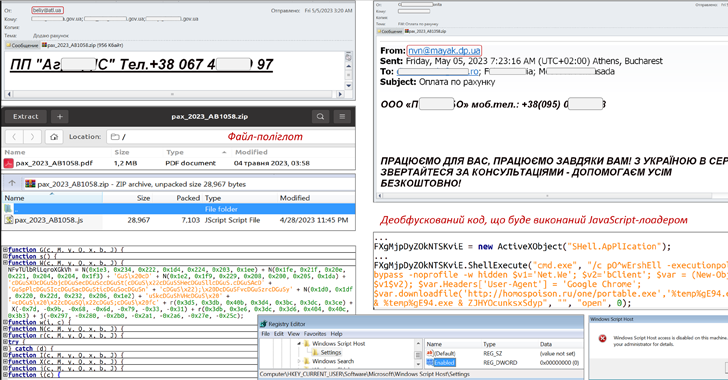
An ongoing phishing marketing campaign with bill-themed lures is becoming made use of to distribute the SmokeLoader malware in the kind of a polyglot file, according to the Pc Crisis Response Workforce of Ukraine (CERT-UA).
The e-mail, per the agency, are despatched making use of compromised accounts and appear with a ZIP archive that, in actuality, is a polyglot file containing a decoy doc and a JavaScript file.
The JavaScript code is then made use of to launch an executable that paves for the execution of the SmokeLoader malware. SmokeLoader, to start with detected in 2011, is a loader whose main objective is to down load or load a stealthier or additional effective malware on to infected techniques.
CERT-UA attributed the exercise to a menace actor it phone calls UAC-0006 and characterised it as a economically motivated operation carried out with the goal of stealing credentials and building unauthorized fund transfers.

In a similar advisory, Ukraine’s cybersecurity authority also unveiled details of harmful attacks orchestrated by a team identified as UAC-0165 from general public sector organizations.
The attack, which targeted an unnamed condition organization, entailed the use of a new batch script-dependent wiper malware named RoarBAT that performs a recursive search for information with a precise listing of extensions and irrevocably deletes them applying the reputable WinRAR utility.
This, in transform, was accomplished by archiving the identified files utilizing the “-df” command-line selection and subsequently purging the produced archives. The batch script was executed by implies of a scheduled endeavor.
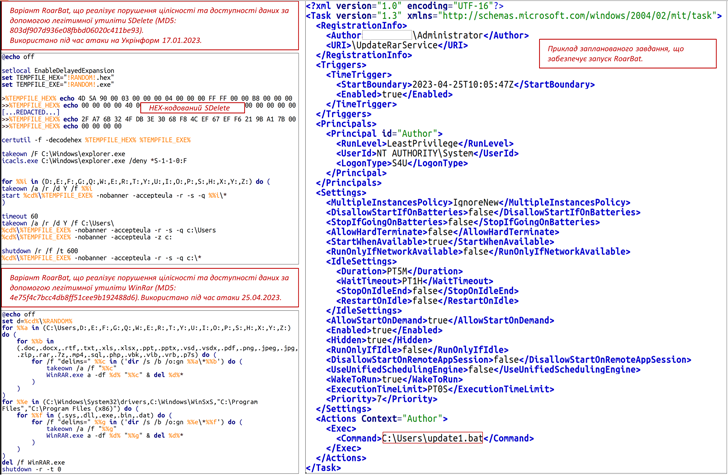
Simultaneously, Linux units were being compromised utilizing a bash script that leveraged the dd utility to overwrite files with zero bytes, efficiently staying away from detection by security software package.
“It was found that the operability of electronic desktops (server devices, automated person workplaces, data storage systems) was impaired as a result of the damaging impression carried out with the use of proper software package,” CERT-UA mentioned.
“Obtain to the ICS goal of the attack is allegedly received by connecting to a VPN employing compromised authentication data. The thriving implementation of the attack was facilitated by the lack of multi-factor authentication when generating remote connections to VPN.”
Upcoming WEBINARLearn to Stop Ransomware with Authentic-Time Defense
Sign up for our webinar and find out how to end ransomware attacks in their tracks with true-time MFA and service account safety.
Save My Seat!
The agency further more attributed UAC-0165 with moderate self-assurance to the notorious Sandworm team (aka FROZENBARENTS, Seashell Blizzard, or Voodoo Bear), which has a historical past of unleashing wiper assaults due to the fact the begin of the Russo-Ukrainian war final year.
The connection to Sandworm stems from important overlaps with a further harmful attack that hit the Ukrainian condition information agency Ukrinform in January 2023, which was tied to the adversarial collective.
The alerts appear a 7 days just after CERT-UA cautioned of phishing assaults carried out by the Russian condition-sponsored team APT28 targeting authorities entities in the state with phony Window update notifications.
Found this report exciting? Abide by us on Twitter and LinkedIn to browse much more distinctive information we post.
Some parts of this article are sourced from:
thehackernews.com

 Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry