The most recent Gcore Radar report and its aftermath have highlighted a spectacular raise in DDoS assaults across a number of industries. At the commencing of 2023, the regular energy of assaults achieved 800 Gbps, but now, even a peak as large as 1.5+ Tbps is unsurprising. To consider and break by Gcore’s defenses, perpetrators designed two makes an attempt with two unique procedures. Examine on to learn what happened and understand how the security provider stopped the attackers in their tracks without the need of impacting close users’ experiences.
A Effective DDoS Assaults
In November 2023, just one of Gcore’s clients from the gaming business was specific by two huge DDoS assaults, peaking at 1.1 and 1.6 Tbps respectively. The attackers deployed various procedures in an unsuccessful attempt to compromise Gcore’s protecting mechanisms.
Attack #1: 1.1 Tbps UDP-dependent DDoS
In the to start with cyber assault, the attackers despatched a barrage of UDP website traffic to a target server, peaking at 1.1 Tbps. Two techniques have been used:
- By utilizing random UDP source ports, they hoped to evade standard filtering mechanisms.
- The attackers concealed their legitimate identity by forging resource IP addresses.
This was a vintage flood (or volumetric) attack, whereby the attackers hoped to take in all obtainable bandwidth of or to a facts centre or network, overpowering the goal servers with traffic and creating them unavailable to legitimate consumers.
The graph below reveals customer’s traffic in the course of the attack. The peak of 1.1 Tbps displays an intense but small-lived endeavor to flood the network with info. The green line (“full.general.enter”) exhibits all inbound visitors. The other coloured lines on the graph signify the network’s responses, such as actions to filter and drop malicious traffic, as the method manages the deluge of info.
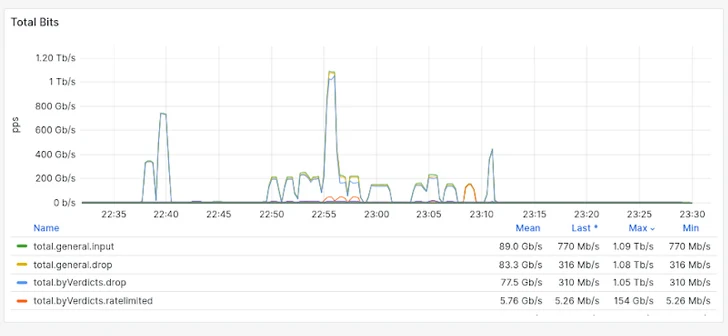 The attack comprised a quick but extreme peak of 1.1 Tbps all-around 22:55
The attack comprised a quick but extreme peak of 1.1 Tbps all-around 22:55
Attack #2: 1.6 Tbps TCP-based DDoS
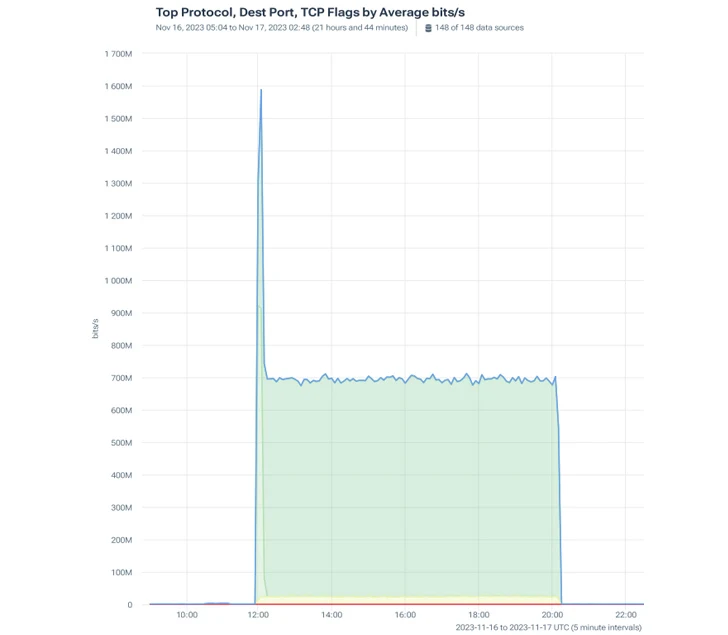 The attack’s constant targeted traffic volume was 700 Mbps and at the onset peaked at 1600 Mbps
The attack’s constant targeted traffic volume was 700 Mbps and at the onset peaked at 1600 Mbps
This time, the attackers attempted to exploit TCP protocol with a blend of SYN flood, PSH, and ACK website traffic.
In a SYN flood attack, a number of SYN packets are sent to the focus on server without the need of ACK packets. This suggests the server generates a half-open link for each and every SYN packet. If productive, the server will finally run out of means and quit accepting connections.
The PSH, ACK stage of the attack speedily sends facts to the target program. The ACK flag indicators that the server obtained the previous packet. This pushes the process to manage knowledge instantly, losing sources. A SYN flood assault using PSH, ACK packets is more challenging to defend in opposition to than a SYN flood, considering that the PSH flag leads to the server to course of action the packet contents immediately, consuming extra means.
As right before, the goal was to overload the customer’s servers and make their services inaccessible to licensed users. This SYN flood experienced a peak volume of 685.77 Mbps and the PSH, ACK experienced a magnitude of 906.73 Mbps.
Gcore’s Defensive Strategies
Gcore’s DDoS Security successfully neutralized each assaults when preserving normal service for the customer’s finish end users. The basic strategy of fending off DDoS security threats incorporates many approaches, this sort of as Gcore’s front-line defenses:
- Dynamic website traffic shaping: Dynamically adjusted traffic fees correctly mitigate the affect of the attack even though ensuring the continuity of critical expert services. In order to prioritize legitimate website traffic whilst slowing unsafe transmissions, adaptive thresholds and charge restrictions are utilised.
- Anomaly detection and quarantine: Versions based mostly on machine finding out review conduct to determine anomalies. When an anomaly occurs, automated quarantine mechanisms redirect faulty visitors to isolated segments for added evaluation.
- Normal expression filters: To block destructive payloads devoid of disrupting respectable targeted visitors, frequent expression-primarily based filter guidelines are carried out. Their constant high-quality-tuning ensures optimum protection without the need of false positives.
- Collaborative threat intelligence: Gcore actively engages in the trade of danger intelligence with sector peers. Collective insights and real-time danger feeds guideline Gcore’s security procedures, letting a speedy response to creating attack vectors.
By employing these strategies, Gcore was capable to successfully mitigate the influence of DDoS attacks and shield their customer’s platform from disruption, negating likely reputational and economic losses.
Conclusion
DDoS attacks of 1.5+ Tbps quantity pose an raising risk across industries, with attackers using imaginative methods to try and bypass safety products and services. In excess of the program of 2023, Gcore has registered increases in the two typical and most attack volumes, and these two linked attacks show that craze.
In the attacks covered in the posting, Gcore was ready to stop any damage by a combination of dynamic site visitors shaping, anomaly detection, normal expression filters, and collaborative danger intelligence. Check out DDoS Safety solutions to safe your network towards ever-evolving DDoS threats.
Uncovered this article exciting? Comply with us on Twitter and LinkedIn to go through far more exclusive information we publish.
Some parts of this article are sourced from:
thehackernews.com


 WhatsApp’s New Secret Code Feature Lets Users Protect Private Chats with Password
WhatsApp’s New Secret Code Feature Lets Users Protect Private Chats with Password