A suspected Chinese-speaking menace actor has been attributed to a destructive marketing campaign that targets the Uzbekistan Ministry of International Affairs and South Korean buyers with a distant obtain trojan referred to as SugarGh0st RAT.
The activity, which commenced no later on than August 2023, leverages two distinct infection sequences to produce the malware, which is a custom made variant of Gh0st RAT (aka Farfli).
It will come with characteristics to “facilitate the distant administration tasks as directed by the C2 and modified communication protocol based mostly on the similarity of the command composition and the strings used in the code,” Cisco Talos scientists Ashley Shen and Chetan Raghuprasad stated.
The attacks begin with a phishing email bearing decoy paperwork, opening which activates a multi-phase method that leads to the deployment of SugarGh0st RAT.

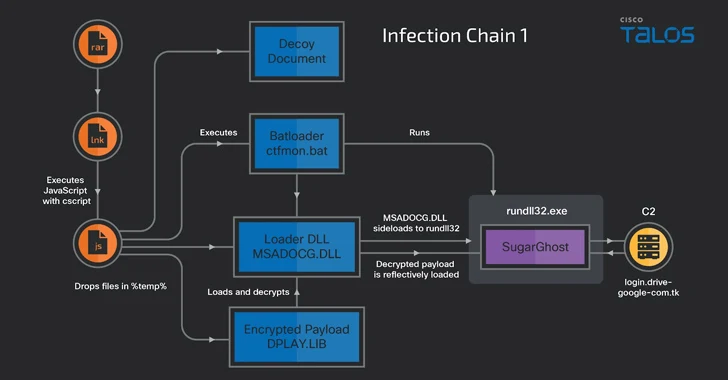
The decoy files are integrated within just a greatly obfuscated JavaScript dropper which is contained in a Windows Shortcut file embedded in the RAR archive email attachment.
“The JavaScript decodes and drops the embedded information into the %TEMP% folder, which includes a batch script, a custom made DLL loader, an encrypted SugarGh0st payload, and a decoy doc,” the scientists claimed.
The decoy doc is then displayed to the victim, whilst, in the history, the batch script runs the DLL loader, which, in turn, side-hundreds it with a copied version of a legitimate Windows executable named rundll32.exe to decrypt and launch the SugarGh0st payload.
A 2nd variant of the attack also starts with a RAR archive made up of a destructive Windows Shortcut file that masquerades as a lure, with the difference being that the JavaScript leverages DynamicWrapperX to operate shellcode that launches SugarGh0st.
SugarGh0st, a 32-bit dynamic-url library (DLL) created in C++, establishes speak to with a really hard-coded command-and-manage (C2) area, enabling it to transmit program metadata to the server, launch a reverse shell, and operate arbitrary instructions.
It can also enumerate and terminate procedures, take screenshots, accomplish file functions, and even obvious the machine’s event logs in an endeavor to protect its tracks and evade detection.
The campaign’s hyperlinks to China stem from Gh0st RAT’s Chinese origins and the point that the completely practical backdoor has been commonly adopted by Chinese danger actors in excess of the years, in element driven by the release of its resource code in 2008. A different using tobacco gun proof is the use of Chinese names in the “past modified by” area in the metadata of the decoy files.

“The Gh0st RAT malware is a mainstay in the Chinese threat actors’ arsenal and has been active considering that at minimum 2008,” the scientists reported.
“Chinese actors also have a record of focusing on Uzbekistan. The targeting of the Uzbekistan Ministry of International Affairs also aligns with the scope of Chinese intelligence exercise abroad.”
The development will come as Chinese state-sponsored groups have also more and more qualified Taiwan in the last six months, with the attackers repurposing residential routers to mask their intrusions, according to Google.
Observed this write-up appealing? Abide by us on Twitter and LinkedIn to read much more special material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Discover How Gcore Thwarted Powerful 1.1Tbps and 1.6Tbps DDoS Attacks
Discover How Gcore Thwarted Powerful 1.1Tbps and 1.6Tbps DDoS Attacks