The Internet of Matters (IoT) is transforming performance in many sectors like healthcare and logistics but has also launched new security risks, specially IoT-driven DDoS assaults. This report explores how these attacks get the job done, why they’re uniquely problematic, and how to mitigate them.
What Is IoT?
IoT (Internet of Issues) refers to on line, interconnected devices that gather and trade details. This wide classification of gadgets contains sensors, cameras, network routers, and superior equipment, and their integration into day-to-day everyday living and get the job done processes effects in an ecosystem that can automate functions, increase conclusion-generating, and boost consumer experience.
IoT: A Breeding Floor for Botnets
IoT’s immediate adoption amplifies its vulnerability, as improperly secured products become quick prey for attackers and may well turn out to be element of a botnet. Managed by attackers, botnets can scale and fast execute numerous assaults, which includes DDoS, data theft, ad fraud, cryptocurrency mining, spam and phishing, facts harvesting, and snooping—without unit owners’ expertise.
Why are IoT Botnets a Rising Concern?
Botnets are nothing at all new, but IoT botnets pose a unique menace. The range of IoT gadgets arrived at 16 billion in 2022 and is anticipated to exceed 30 billion by 2025. These equipment normally go through from infrequent updates or insecure default settings, or are only still left unattended, making them a lot less safe than traditional computers and are at risk of being hijacked with relative ease to form strong botnets.
The scale and complexity of IoT-pushed assaults are established to increase due to their expanding use. Amid these dangers, dispersed denial-of-company (DDoS) attacks stand out as specifically challenging to mitigate. The distributed mother nature of IoT equipment renders them great platforms for these attacks, building it hard to establish and block malicious website traffic and thus compounding the challenges of DDoS mitigation.
Anatomy of IoT-Driven botnet DDoS Attacks
Let us discuss how IoT DDoS assaults transpire and how new IoT units be a part of the ranks of bots.
How Are IoT DDoS Assaults Introduced?
There are many crucial entities included in a DDoS botnet attack:
- The attacker is the particular person who controls the botnet. They are also recognized as the bot herder or botmaster.
- A command-and-regulate (C&C) server is a computer system controlled by the attacker and applied to converse with the infected gadgets. The C&C orchestrates the botnet’s actions, sending out world wide instructions for jobs like initiating an attack or scanning a new device for vulnerabilities.
- A botnet is a network of devices that have been infected with malware and are managed by a solitary attacker.
- The victim or concentrate on is the emphasis of a unique botnet-driven attack.
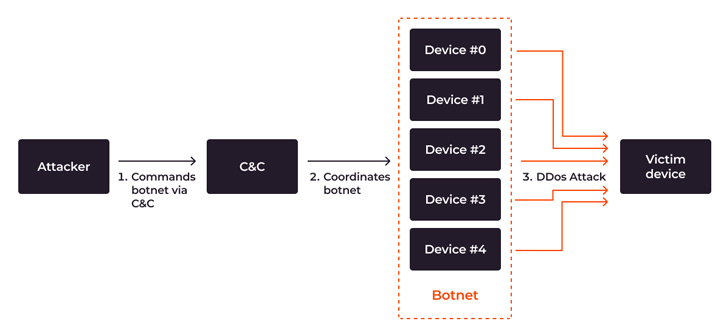 DDoS botnet assault stream from attacker’s command to DDoS attack
DDoS botnet assault stream from attacker’s command to DDoS attack
The attack process is fairly simple:
When the botnet floods the focus on with extreme requests, assistance failures come about which jeopardize the availability of the specific procedure and even set the integrity of the whole infrastructure at risk. When aimed versus essential infrastructures this sort of as healthcare or transportation, the hazards go over and above fiscal and reputational damage to endangering people’s lives.
Incorporating IoT Equipment into Botnets
IoT equipment that are unpatched, unattended, or misconfigured, or are currently less than botnet DDoS attack, are at risk of getting included into a botnet. To extend the botnet, an attacker hacks new IoT equipment. This process entails two entities: the botnet itself and the loader server, a specific server that infects other devices.
In temporary, the approach goes like this: The botnet hacks the system and gains entry, and then the loader server installs malware on it. The attacker then gains long-lasting accessibility to the device and attaches it to the botnet. Here are the levels of infecting IoT devices and connecting them to a botnet primarily based the Mirai case:
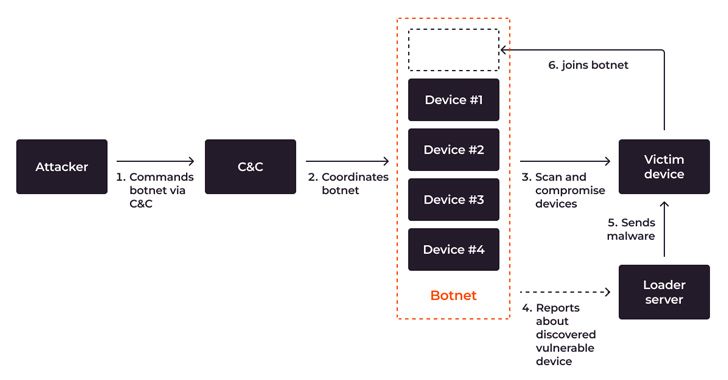 Process move, demonstrating scanning, compromising, infecting and joining a new system to a botnet
Process move, demonstrating scanning, compromising, infecting and joining a new system to a botnet
Highly developed botnets can self-propagate, compromising far more products autonomously, bringing additional and far more gadgets into the botnet, growing the botnet’s dimension and amplifying the scale of future assaults.
How Risky Is the Present-day IoT DDoS Risk?
IoT-pushed DDoS assaults enhanced by 300% in the 1st 50 % of 2023 by itself, producing an estimated world wide money loss of $2.5 billion. In 2023, 90% of advanced, multi-vector DDoS assaults were being based on botnets. The trend exhibits no symptoms of slowing down: the range of IoT products engaged in botnet-driven DDoS assaults rose from all around 200,000 a year in the past to roughly 1 million devices, though there are two times as lots of vulnerabilities being targeted by botnet malware.
General, DDoS attack ability is on the increase. In accordance to Gcore’s Radar 2023, the prime electrical power of a singular DDoS attack arrived at a staggering 800 Gbps in the to start with 50 percent of 2023. Just two years earlier, it peaked at 300 Gbps. While most assaults strike 1–2 Tbps speeds, the most powerful can attain 100 Tbps.
Alarming Projections for 2023–2024
We are witnessing a sizeable increase in unique DDoS attack vectors, these kinds of as UDP reflection and HTTP request flooding, mainly concentrating on the technology and monetary industries. Sectors greatly reliant on on-line companies and real-time details processing are the most eye-catching targets, facing rapid monetary losses and prolonged-phrase reputational harm.
IoT’s advancement, although driving innovation, also delivers alarming long run traits in cybersecurity: it fuels innovation but also raises significant cybersecurity concerns. With an predicted 18% progress in IoT units to 14.4 billion in 2023, and a projected raise to 27 billion by 2025, experts anticipate a corresponding surge in botnet assaults. With both equally IoT and DDoS on the increase, IoT DDoS are posed to turn into an progressively substantial threat in the fast foreseeable future.
Defensive Measures: Techniques and Best Practices
The increase of more subtle and potent assaults tends to make fast notice to security critical. This is how a variety of stakeholders can lead to a a lot more protected digital ecosystem:
1. Secure your IoT from currently being infected.
- Educate on safe IoT practices: Really encourage house and company buyers to change default passwords, update firmware, and adhere to best procedures to stop equipment from remaining compromised. Quite a few firms, like SANS Institute, offer education on IoT security and penetration screening.
- Collaborate and danger share: Initiatives like the Cyber Menace Alliance and the Joint Cyber Defense Collaborative unite governments, tech organizations, and cybersecurity corporations to rapidly detect and neutralize emerging threats, strengthening collective world-wide defenses.
- On a regular basis update devices: Ensure IoT products are up-to-date with the most current firmware and patches to protect against regarded vulnerabilities from becoming exploited.
2. Secure versus IoT-pushed botnet DDoS attacks.
- Carry out multi-layer security protocols: Deploy a thorough security system, from firewalls and intrusion detection techniques to web application security solutions.
- Devote in Specialized DDoS Security Methods: Companies like Gcore have made solutions explicitly built to beat even enormous, IoT-driven DDoS assaults. These DDoS defense remedies have been pivotal in minimizing risks by leveraging actual-time analytics.
Conclusion
The challenge of defending towards IoT-pushed DDoS attacks is an ongoing battle. By understanding present-day methods, investing in specialised technologies like Gcore’s DDoS security, and fostering a culture of vigilance and collaboration, you can significantly reduce organizational dangers and help pave the way for a much more secure electronic landscape in the confront of escalating threats.
Identified this article appealing? Observe us on Twitter and LinkedIn to read a lot more exclusive material we submit.
Some parts of this article are sourced from:
thehackernews.com


 NodeStealer Malware Now Targets Facebook Business Accounts on Multiple Browsers
NodeStealer Malware Now Targets Facebook Business Accounts on Multiple Browsers