Phishing strategies offering malware households these as DarkGate and PikaBot are adhering to the exact practices earlier used in attacks leveraging the now-defunct QakBot trojan.
“These involve hijacked email threads as the preliminary an infection, URLs with special patterns that limit user access, and an an infection chain nearly identical to what we have observed with QakBot delivery,” Cofense claimed in a report shared with The Hacker News.
“The malware people utilized also adhere to suit to what we would be expecting QakBot affiliates to use.”

QakBot, also called QBot and Pinkslipbot, was shut down as aspect of a coordinated regulation enforcement exertion codenamed Operation Duck Hunt before this August.
The use of DarkGate and PikaBot in these campaigns is not astonishing as they can both of those act as conduits to supply further payloads to compromised hosts, creating them equally an appealing option for cybercriminals.
PikaBot’s parallels to QakBot were being previously highlighted by Zscaler in its examination of the malware in Might 2023, noting similarities in the “distribution techniques, campaigns, and malware behaviors.”
DarkGate, for its portion, incorporates highly developed techniques to evade detection by antivirus devices, alongside capabilities to log keystrokes, execute PowerShell, and put into practice a reverse shell that allows its operators to commandeer an infected host remotely.
“The connection is bidirectional, this means the attackers can send out commands and obtain responses in real-time, enabling them to navigate the victim’s system, exfiltrate knowledge, or perform other destructive actions,” Sekoia explained in a new technological report of the malware.

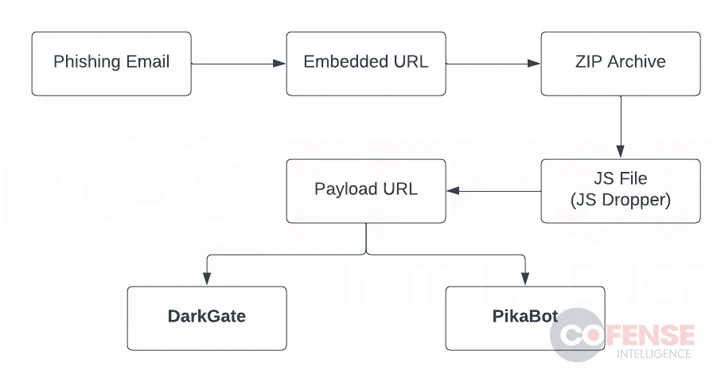
Cofense’s assessment of the large-volume phishing marketing campaign displays that it targets a broad assortment of sectors, with the attack chains propagating a booby-trapped URL pointing to a ZIP archive in hijacked email threads.
The ZIP archive contains a JavaScript dropper that, in flip, contacts a 2nd URL to down load and run possibly the DarkGate or PikaBot malware.
A noteworthy variant of the assaults has been observed getting advantage of Excel include-in (XLL) files in lieu of JavaScript droppers to provide the closing payloads.
“A profitable DarkGate or PikaBot an infection could guide to the delivery of advanced crypto mining computer software, reconnaissance tools, ransomware, or any other destructive file the risk actors wish to set up on a victim’s machine,” Cofense explained.
Uncovered this short article appealing? Follow us on Twitter and LinkedIn to read far more unique material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Why Defenders Should Embrace a Hacker Mindset
Why Defenders Should Embrace a Hacker Mindset