Corporations in Italy are the target of a new phishing marketing campaign that leverages a new strain of malware named WikiLoader with an final aim to set up a banking trojan, stealer, and spy ware known as Ursnif (aka Gozi).
“It is a refined downloader with the goal of setting up a next malware payload,” Proofpoint explained in a specialized report. “The malware takes advantage of several mechanisms to evade detection and was very likely produced as a malware that can be rented out to find cybercriminal menace actors.”
WikiLoader is so named because of to the malware generating a ask for to Wikipedia and checking that the response has the string “The Free of charge.”
The organization security company reported it 1st detected the malware in the wild on December 27, 2022, in relationship with an intrusion set mounted by a threat actor it tracks as TA544, which is also known as Bamboo Spider and Zeus Panda.
The campaigns are centered all over the use of e-mails containing either Microsoft Excel, Microsoft OneNote, or PDF attachments that act as a entice to deploy the downloader, which is subsequently made use of to install Ursnif.
In a indicator that WikiLoader is shared among several cybercrime teams, the risk actor dubbed TA551 (aka Shathak) has also been observed using the malware as of late March 2023.
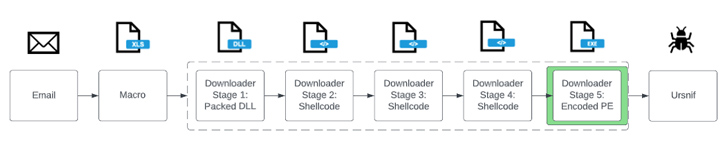
Current TA544 strategies detected in mid-July 2023 have used accounting themes to propagate PDF attachments with URLs that, when clicked, lead to the shipping and delivery of a ZIP archive file, which, in flip, packs a JavaScript file developed to down load and execute WikiLoader.
WikiLoader is intensely obfuscated and will come with evasive maneuvers to bypass endpoint security software and steer clear of detonation in automatic evaluation environments. It really is also engineered to retrieve and operate a shellcode payload hosted on Discord, which is ultimately utilized to launch Ursnif.
Impending WEBINARShield From Insider Threats: Master SaaS Security Posture Management
Nervous about insider threats? We have bought you protected! Join this webinar to take a look at simple tactics and the secrets of proactive security with SaaS Security Posture Administration.
Be part of Now
“It is at this time less than active progress, and its authors show up to make common changes to test and keep on being undetected and fly underneath the radar,” Selena Larson, senior threat intelligence analyst at Proofpoint, said in a assertion.
“It is possible much more legal menace actors will use this, especially these acknowledged as preliminary entry brokers (IABs) that carry out standard activity that prospects to ransomware. Defenders must be aware of this new malware and activities concerned in payload shipping and delivery, and just take ways to guard their corporations in opposition to exploitation.”
Found this post appealing? Adhere to us on Twitter and LinkedIn to examine additional special content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 A ferroelectric transistor that stores and computes at scale
A ferroelectric transistor that stores and computes at scale