A country-state actor with back links to China is suspected of being powering a sequence of attacks versus industrial corporations in Jap Europe that took area previous year to siphon info stored on air-gapped methods.
Cybersecurity firm Kaspersky attributed the intrusions with medium to superior self confidence to a hacking crew called APT31, which is also tracked underneath the monikers Bronze Vinewood, Judgement Panda and Violet Hurricane (formerly Zirconium), citing commonalities in the strategies observed.
The assaults entailed the use of far more than 15 unique implants and their variants, broken down into three broad groups dependent on their potential to create persistent remote entry, acquire delicate information and facts, and transmit the collected information to actor-managed infrastructure.
“A person of the implant types appeared to be a complex modular malware, aimed at profiling removable drives and contaminating them with a worm to exfiltrate info from isolated, or air-gapped, networks of industrial organizations in Eastern Europe,” Kaspersky reported.
“The other sort of implant is built for thieving info from a regional laptop or computer and sending it to Dropbox with the enable of the future-phase implants.”
One particular established of backdoors consists of numerous variations of a malware loved ones identified as FourteenHi that have been place to use considering that at least mid-March 2021 and which occur with a wide spectrum of capabilities to add and obtain arbitrary documents, operate instructions, start a reverse shell, and erase their possess presence from the compromised hosts.

A second initially-stage backdoor utilised for remote obtain and initial data gathering is MeatBall, which possesses capabilities to listing functioning processes, enumerate related equipment, complete file functions, seize screenshots, and self-update by itself.
Also discovered is a third variety of initially-phase implant that will make use of Yandex Cloud for command-and-management, mirroring equivalent conclusions from Optimistic Systems in August 2022 detailing APT31 assaults targeting Russian media and electrical power providers.
“The tendency to abuse cloud solutions (e.g., Dropbox, Yandex, Google, etc.) is not new, but it proceeds to broaden, for the reason that it is hard to restrict / mitigate in instances when an organization’s company procedures rely on employing these types of services,” Kaspersky researchers stated.
“Threat actors maintain generating it more difficult to detect and review threats by hiding payloads in encrypted variety in different binary info documents and by hiding malicious code in the memory of genuine programs by means of DLL hijacking and a chain of memory injections.”
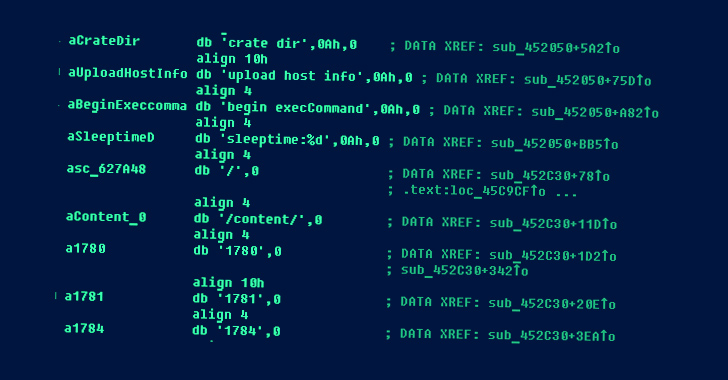
APT31 has also been noticed employing focused implants for gathering regional documents as well as exfiltrating details from air-gapped devices by infecting removable drives.
The latter malware pressure is made up of at the very least three modules, with just about every component accountable for different tasks, these as profiling and dealing with detachable drives, recording keystrokes and screenshots, and planting 2nd-action malware on newly linked drives.
“The menace actor’s deliberate initiatives to obfuscate their actions by means of encrypted payloads, memory injections, and DLL hijacking [underscore] the sophistication of their tactics,” Kirill Kruglov, senior security researcher at Kaspersky ICS CERT, reported.

“Even though exfiltrating details from air-gapped networks is a recurrent tactic adopted by quite a few APTs and targeted cyberespionage strategies, this time it has been created and implemented uniquely by the actor.”
Though the aforementioned attack chains are expressly engineered for the Windows environment, there is proof that APT31 has set its sights on Linux techniques as nicely.
Before this month, the AhnLab Security Emergency Response Heart (ASEC) uncovered attacks probably carried out by the adversary towards South Korean businesses with the target of infecting the devices with a backdoor called Rekoobe.
“Rekoobe is a backdoor that can receive commands from a [command-and-control] server to perform a variety of options these as downloading destructive data files, thieving inner documents from a procedure, and executing reverse shell,” ASEC explained.
“Although it might surface straightforward in structure, it employs encryption to evade network packet detection and can accomplish a wide range of malicious behaviors via instructions from the threat actor.”
Found this report exciting? Comply with us on Twitter and LinkedIn to go through much more special material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Cybercriminals Renting WikiLoader to Target Italian Organizations with Banking Trojan
Cybercriminals Renting WikiLoader to Target Italian Organizations with Banking Trojan