Microsoft Term files exploiting recognised distant code execution flaws are being employed as phishing lures to fall malware called LokiBot on compromised units.
“LokiBot, also recognized as Loki PWS, has been a well-recognised information and facts-stealing Trojan energetic because 2015,” Fortinet FortiGuard Labs researcher Cara Lin said. “It primarily targets Windows methods and aims to acquire delicate information from contaminated machines.”
The cybersecurity corporation, which spotted the campaign in Might 2023, reported the assaults just take benefit of CVE-2021-40444 and CVE-2022-30190 (aka Follina) to attain code execution.
The Term file that weaponizes CVE-2021-40444 includes an external GoFile link embedded within just an XML file that prospects to the down load of an HTML file, which exploits Follina to obtain a subsequent-phase payload, an injector module published in Visual Fundamental that decrypts and launches LokiBot.
The injector also attributes evasion strategies to test for the presence of debuggers and figure out if it can be running in a virtualized surroundings.
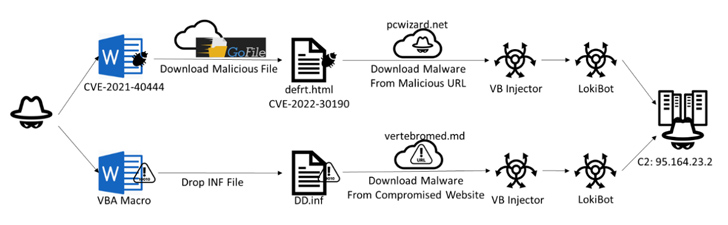
An alternate chain found towards the stop of May possibly starts with a Term document incorporating a VBA script that executes a macro straight away upon opening the document making use of the “Car_Open up” and “Document_Open up” features.
The macro script subsequently functions as a conduit to provide an interim payload from a distant server, which also functions as an injector to load LokiBot and join to a command-and-management (C2) server.
Approaching WEBINARShield From Insider Threats: Grasp SaaS Security Posture Management
Fearful about insider threats? We have received you included! Be part of this webinar to examine sensible tactics and the tricks of proactive security with SaaS Security Posture Administration.
Be a part of These days
LokiBot, not to be puzzled with an Android banking trojan of the identical name, comes with abilities to log keystrokes, seize screenshots, acquire login credential data from web browsers, and siphon details from a wide range of cryptocurrency wallets.
“LokiBot is a extended-standing and popular malware active for quite a few a long time,” Lin said. “Its functionalities have matured over time, generating it quick for cybercriminals to use it to steal delicate details from victims. The attackers powering LokiBot frequently update their original entry procedures, enabling their malware marketing campaign to come across much more effective approaches to spread and infect systems.”
Located this report exciting? Follow us on Twitter and LinkedIn to study far more special written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 CERT-UA Uncovers Gamaredon’s Rapid Data Exfiltration Tactics Following Initial Compromise
CERT-UA Uncovers Gamaredon’s Rapid Data Exfiltration Tactics Following Initial Compromise