The Russia-linked threat actor identified as Gamaredon has been noticed conducting knowledge exfiltration routines in just an hour of the first compromise.
“As a vector of principal compromise, for the most section, e-mails and messages in messengers (Telegram, WhatsApp, Signal) are employed, in most conditions, applying formerly compromised accounts,” the Personal computer Crisis Reaction Group of Ukraine (CERT-UA) reported in an investigation of the group printed last 7 days.
Gamaredon, also known as Aqua Blizzard, Armageddon, Shuckworm, or UAC-0010, is a point out-sponsored actor with ties to the SBU Primary Place of work in the Autonomous Republic of Crimea, which was annexed by Russia in 2014. The team is approximated to have infected countless numbers of authorities computer systems.
It is also 1 of the a lot of Russian hacking crews that have preserved an active existence given that the get started of the Russo-Ukrainian war in February 2022, leveraging phishing campaigns to provide PowerShell backdoors these kinds of as GammaSteel to perform reconnaissance and execute further commands.
The messages ordinarily come bearing an archive made up of an HTM or HTA file that, when opened, activates the attack sequence.
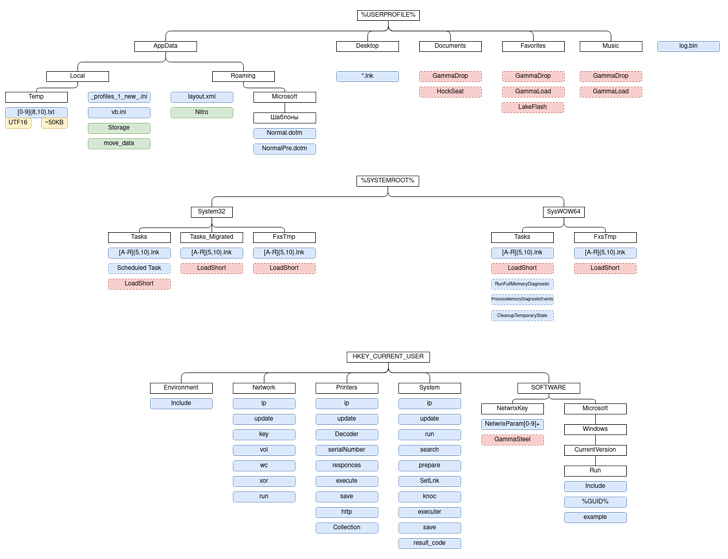
According to CERT-UA, GammaSteel is employed to exfiltrate documents matching a specific set of extensions – .doc, .docx, .xls, .xlsx, .rtf, .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z, and .mdb – in just a time interval of 30 to 50 minutes.
The group has also been observed constantly evolving its methods, building use of USB an infection tactics for propagation. A host running in a compromised point out for a 7 days could have anywhere between 80 to 120 destructive files, the company mentioned.
Forthcoming WEBINARShield From Insider Threats: Learn SaaS Security Posture Administration
Anxious about insider threats? We have bought you included! Be part of this webinar to examine functional methods and the strategies of proactive security with SaaS Security Posture Administration.
Be a part of These days
Also sizeable is the menace actor’s use of AnyDesk software for interactive distant obtain, PowerShell scripts for session hijacking to bypass two-element authentication (2FA), and Telegram and Telegraph for fetching the command-and-control (C2) server data.
“Attackers acquire individual actions to assure fault tolerance of their network infrastructure and stay away from detection at the network stage,” CERT-UA said. “During the day, the IP addresses of intermediate handle nodes can transform from 3 to 6 or additional periods, which, between other things, signifies the ideal automation of the method.”
Identified this post intriguing? Follow us on Twitter and LinkedIn to read much more exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com

 WormGPT: New AI Tool Allows Cybercriminals to Launch Sophisticated Cyber Attacks
WormGPT: New AI Tool Allows Cybercriminals to Launch Sophisticated Cyber Attacks