A new vulnerability disclosed in GitHub could have uncovered hundreds of repositories at risk of repojacking assaults, new results clearly show.
The flaw “could permit an attacker to exploit a race condition within just GitHub’s repository generation and username renaming operations,” Checkmarx security researcher Elad Rapoport claimed in a specialized report shared with The Hacker News.
“Successful exploitation of this vulnerability impacts the open-supply neighborhood by enabling the hijacking of above 4,000 code deals in languages this kind of as Go, PHP, and Swift, as effectively as GitHub steps.”
Pursuing dependable disclosure on March 1, 2023, the Microsoft-owned code hosting platform has addressed the issue as of September 1, 2023.

Repojacking, small for repository hijacking, is a technique where by a threat actor is able to bypass a security system identified as common repository namespace retirement and finally handle of a repository.
What the security evaluate does is stop other users from generating a repository with the same name as a repository with more than 100 clones at the time its consumer account is renamed. In other words and phrases, the mixture of the username and the repository title is regarded as “retired.”
Ought to this safeguard be trivially circumvented, it could empower danger actors to make new accounts with the exact username and upload destructive repositories, most likely main to computer software supply chain attacks.
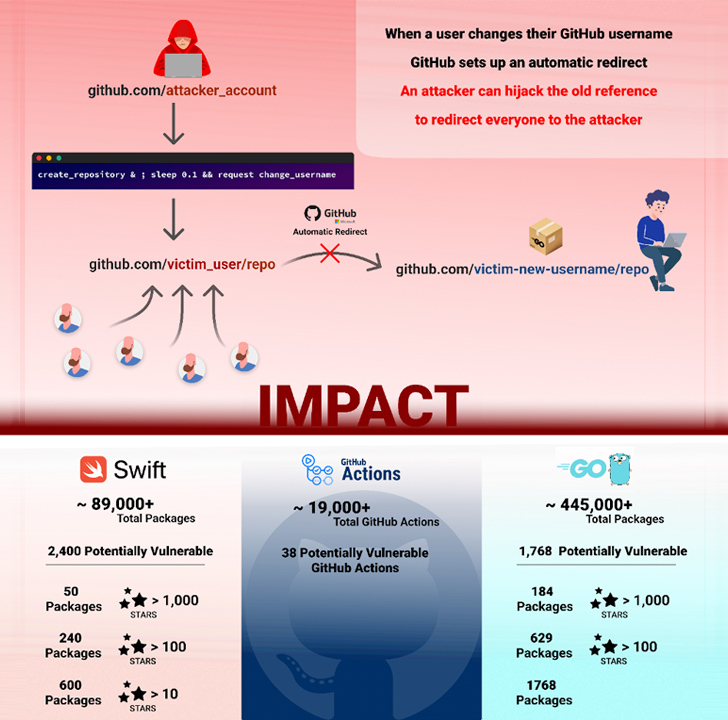
The new approach outlined by Checkmarx can take benefit of a opportunity race condition between the creation of a repository and the renaming of a username to achieve repojacking. Specially, it entails the adhering to ways –
The previous move is achieved utilizing an API request for repository development and a renamed request interception for the username adjust. The growth will come approximately nine months just after GitHub patched a comparable bypass flaw that could open up the door to repojacking attacks.
“The discovery of this novel vulnerability in GitHub’s repository creation and username renaming functions underlines the persistent pitfalls linked with the ‘popular repository namespace retirement’ system,” Rapoport reported.
Uncovered this report intriguing? Abide by us on Twitter and LinkedIn to browse much more special information we publish.
Some parts of this article are sourced from:
thehackernews.com


 7 Steps to Kickstart Your SaaS Security Program
7 Steps to Kickstart Your SaaS Security Program