SaaS purposes are the backbone of modern day corporations, constituting a staggering 70% of total software program utilization. Purposes like Box, Google Office, and Microsoft 365 are integral to daily functions. This widespread adoption has reworked them into likely breeding grounds for cyber threats. Each SaaS software presents one of a kind security problems, and the landscape frequently evolves as vendors enrich their security characteristics. Also, the dynamic character of user governance, such as onboarding, deprovisioning, and purpose adjustments, more complicates the security equation.
With wonderful advantage comes good responsibility, as securing these SaaS apps has grow to be a leading precedence for Chief Information Security Officers (CISOs) and IT groups around the world.
Successfully securing SaaS applications demands a sensitive balance among sturdy security actions and enabling people to carry out their jobs proficiently. To navigate this advanced terrain, this write-up excerpts a action-by-action manual to build a sturdy SaaS security strategy – from preparing to execution and performance measurement.
Map Your Apps and Security Necessities
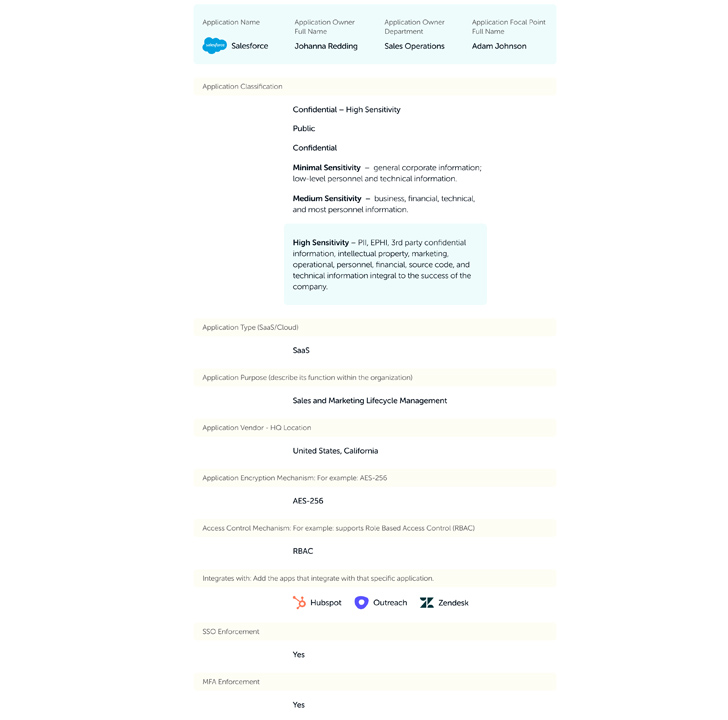
In advance of embarking on a SaaS security journey, it really is imperative to understand your organization’s distinct landscape and security needs. While apps like Salesforce and Microsoft 365 may well comprise more critical info, even lesser, niche apps applied by several teams can shop sensitive facts that will have to be secured.
Contemplate the regulatory and compliance needs relevant to your business. Industries these kinds of as finance adhere to SOX, when healthcare companies will have to comply with HIPAA. Knowing your regulatory ecosystem is critical for shaping your security approach.
Additionally, prioritize user entry and knowledge privateness. Utilizing the principle of the very least privilege (POLP) guarantees people have entry only to the knowledge necessary for their roles, minimizing the risk of details breaches and unauthorized entry. If your apps deal with individually identifiable information (PII), make certain your security plan aligns with privacy guidelines.
In this article is some essential data you should really accumulate for each individual application:
To read through the full Kickstarting Your SaaS Security Method guide, simply click in this article.
Map Your Existing Security Ecosystem and How You Plan to Combine SaaS Security Applications and Procedures
To be most successful, your SaaS security program have to combine tightly into the existing infrastructure. It must join with the organization’s Identification Provider (IdP) for productive consumer governance and your one indication-on (SSO) service provider to make it a lot more tough for unauthorized consumers to obtain the SaaS stack. These integrations boost the security of your programs and make it less difficult for security specialists to do their job.
It’s also important to combine your SaaS security tools with present SOC, SIEM, and SOAR tools. The SOC workforce can examine alerts and rapidly make a willpower as to the mitigation required. Meanwhile, SIEM can manage gatherings while SOAR can orchestrate remediations, deprovision people, and automate numerous of the mitigations essential to safe the SaaS stack.
Establish Stakeholders and Outline Responsibilities
SaaS security is a collaborative work involving various stakeholders. Business units handle SaaS applications with a concentration on efficiency, even though the security team’s precedence is facts safety. Bridging the hole concerning these teams and deciphering the exclusive language of each SaaS application’s configurations is hard.
Powerful SaaS security demands collaboration and compromise in between these events to mitigate dangers without having hindering productiveness.
Outline Shorter-Expression and Extended-Phrase Targets
Producing a thriving SaaS security system demands clear targets and crucial effectiveness indicators (KPIs) to measure development. Commence with a pilot plan concentrated on critical purposes managed by different departments. Build a timeline for the pilot, typically about three months, and set realistic improvement goals.
A posture rating, calculated on a scale of -100%, can help gauge security performance. Purpose to manage a rating over 80% at the conclusion of a 3-thirty day period pilot plan and goal a prolonged-phrase rating of 90-100%.
Raise Your Preliminary Security Posture
Start by securing superior-risk, low-touch objects in collaboration with application homeowners. Near interaction is vital to comprehension the influence of security improvements on workflows and processes. Deal with large-risk security checks impacting a smaller quantity of personnel to start with. Make the most of Security Posture Administration remedies to manual remediation endeavours centered on software, security domain, or severity.
Some businesses select to improve posture one particular application at a time. Others make improvements to posture by domain throughout various applications, while even now other folks pick out to remediate issues by severity irrespective of the application. Whichever model you choose, it is crucial to establish a approach to assistance you go systematically by your apps.
Timetable Ongoing Check out-In Conferences to Keep and Retain Improving Your Posture
Repeated conferences with stakeholders involved in remediation are important, specially during the pilot period. As the posture stabilizes, regulate the frequency of these meetings to assure sustained security.
Continue on onboarding and checking added apps to increase the security posture of your whole SaaS stack.
Undertake a Rigorous Identity & Entry Governance Plan
Embrace the basic principle of least privilege (POLP) to prohibit user access to necessary tools and facts. Deprovision customers who no extended call for entry to decrease hazards involved with lively accounts. Routinely observe external people, specially all those with admin rights, to safeguard application facts.
By adhering to these principles and next a structured technique, corporations can set up a strong SaaS security software. Bear in mind, SaaS security is an ongoing approach, and ongoing adaptation and enhancement are critical to remaining forward of evolving threats in the digital landscape.
Study how to streamline and automate securing your SaaS stack.
Uncovered this article attention-grabbing? Abide by us on Twitter and LinkedIn to read more exclusive articles we post.
Some parts of this article are sourced from:
thehackernews.com


 Chinese Redfly Group Compromised a Nation’s Critical Grid in 6-Month ShadowPad Campaign
Chinese Redfly Group Compromised a Nation’s Critical Grid in 6-Month ShadowPad Campaign