Validate security repeatedly across your comprehensive stack with Pen Screening as a Provider.
In present-day modern day security functions centre (SOC), it is really a battle among the defenders and the cybercriminals. The two are applying applications and skills – having said that, the cybercriminals have the element of shock on their aspect, and a host of techniques, tactics, and processes (TTPs) that have developed. These external risk actors have now been even more emboldened in the period of AI with open-supply instruments like ChatGPT.
With the prospective of an attack primary to a breach inside minutes, CISOs now are hunting to get ready all devices and assets for cyber resilience and rapid response when essential.
With tools and abilities to validate security continually – which includes penetration tests as a support – DevSecOps groups can remediate critical vulnerabilities rapid owing to the easy obtain to tactical help to the teams that need to have it the most. This gives the SOC and DevOps teams tools to that eliminate untrue positives, validate findings, and streamline remediation and incident reaction. This effective financial investment presents a sport-position advantage that provides back again time to the SOC by cutting down occasions, incidents, and breaches that involve the SOC to detect and react.
The Need to have to Continually Validate Security Now
Constantly validating an organization’s security is foundational in a cybersecurity program to satisfy various compliance requirements, industry restrictions, and federal mandates. Corporations need to offer proof with validated artifacts and accredited, unbiased penetration screening reports that their programs and total environments continually meet the needs the corporation has set for governance, risk, and compliance.
On top of that, the rewards of steady validation mixed with penetration testing can be a power multiplier for audit-readiness, incident preparedness, and fortified defenses.
As security leaders seek out new remedies to increase security outcomes and reduce breaches, they are wanting at the testing facet to enhance compliance whilst validating security. With this Cyber Security Validation in place, anything will work together as a total-stack alternative. This new alternative provides an exit system from legacy pentesting solutions for a much more advanced risk management solution that accelerates results for present-day fashionable SOC.
The Challenge with Regular Penetration Screening
Legacy penetration testing methods are even now working with manual testing approaches despite the availability of modern-day technology, like AI and automation.
Moreover, conventional penetration tests has historically remaining DevOps in the dark. Whilst integrating DevOps remediation inside of the lifecycle of the precise penetration exam just will make fantastic company sense – the option is ignored when doing the job with legacy companies. This tactic results in persistent delays, elevated expenditures, and earnings reduction – all the whilst security hazards and compliance vulnerabilities that had been found throughout the penetration exam are still left unnecessarily uncovered. The apparent missed option is very clear – in particular when security leaders can pursue a greater way.
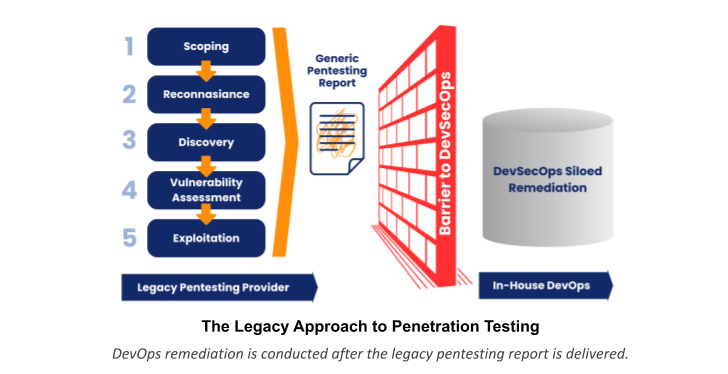
When a penetration tester discovers a critical vulnerability – shouldn’t DevOps be alerted proper absent? Security leaders have earned a improved option from their penetration tests investments.
What is Pen Screening as a Service (PTaaS)?
1 of the most exciting innovative ways these days for security and technology leaders currently is the augmented capabilities readily available by means of a capable Pentesting as a Services (PTaaS) system and services supplier.
PTaaS is a contemporary approach to delivering penetration screening providers. It utilizes a combination of manual human-led pentesting, AI, and automation tools and procedures that speed up pentesting with no fake positives. This answer is getting momentum, as it aids mitigate the cybersecurity techniques hole staying confronted by security leaders at a worldwide degree. PTaaS aids technology and security leaders tap into a treasure trove of abilities to improve their pen tests investments. With knowledgeable, qualified penetration testers obtainable on-desire, PTaaS shoppers can tap into the talent they want to perform a penetration check at any time – without having the additional cost of hiring highly-priced security practitioners.
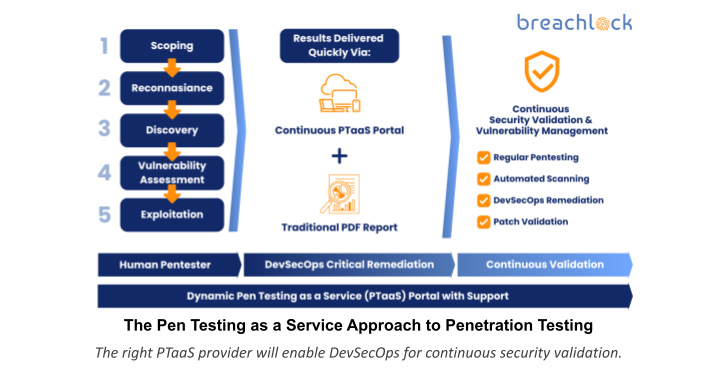
How PTaaS Operates to Validate Security Continuously
Somewhat than a linear strategy exactly where a legacy pen examination is shipped and the in-house DevOps crew requires on the proposed remediations after the pen test concludes, PTaaS integrates DevOps remediation into the lifecycle of just about every penetration exam. This enables a DevSecOps testing technique to taking care of cybersecurity risk – the preferred solution by CISOs to improve security maturity and cyber resilience.
In addition, the right PTaaS service provider will offer you continual vulnerability management positive aspects very long just after the pen take a look at has concluded within the client portal hosted by way of a cloud system that involves patch retesting and automatic vulnerability scanning. These added benefits facilitate group collaboration with the PTaaS provider as they handle the PTaaS applications inside the system that provide constant security validation.
PTaaS Rewards Discussed
As corporations proceed to rely on technology for everyday security functions, it is essential to have a extensive knowing of potential security vulnerabilities. Pen Tests as a Support (PTaaS) presents CISOs the abilities they have to have to perform continuous pen screening to uncover weaknesses in networks, apps, and cloud systems from a qualified third bash that offers constant security testing, vulnerability scanning, and insights on critical hazards.
Speedy Benefits of PTaaS
The largest gain that CISOs can be expecting from picking out the proper PTaaS investment is looking at security results improved throughout groups as they get unbiased penetration tests executed by in-house, qualified human authorities applying business-conventional methodologies, cutting edge technology, and an highly developed cloud pentesting system to deal with each PTaaS engagement.
The PTaaS product provides further speedy benefits, which includes the next positive aspects:
- Agility
- Much more expense-productive than conventional in-house penetration tests
- Faster scheduling, testing effectiveness, and report execution
- API integrates with DevOps ticketing management programs
- Precision
- Protected cloud system provides visibility of exam benefits
- Certified penetration testers conduct total-stack penetration exams
- AI and automation strengthen security screening efficiency
- Human testers validate automatic effects and security discoveries
- Guaranteed Zero wrong positives
- Diminished Complete Price of Possession (TCO)
- Increases security results and compliance-readiness affordably
- Take away duplicative vulnerability scanning and screening technologies in the security tech stack
- Replace common pentesting companies with PTaaS constant security testing abilities, options, and rewards
- Scalability
- Get rid of the DevOps silo of remediation
- Real-time communications are bundled with customer access to penetration testers
- Get pen checks on-demand and when needed
Prolonged Time period Advantages of PTaaS
Above time, when PTaaS is integrated into a detailed security tactic, security leaders can greatly advance an organization’s defenses versus cyber threats and fortify overall cyber resilience.
The extensive-time period benefits of PTaaS shipping in your group are sizeable, like the rewards as follows:
- Value Discounts
- Outsource the conclude-to-conclusion features of the pentesting system, together with avoiding potential scope creep
- Continuous Security Validation
- Maintain Security and DevOps teams stay on top rated of security and compliance and enables them to promptly reply to new vulnerabilities
- Visibility into the Adversary’s Standpoint
- Get an exact report of what adversaries can see uncovered in the client’s units with an goal and impartial point of view
- In-House Staff Extension
- Tap into experience and methods lacking in-house
- Improved Security Results
- Recognize dangers, exposures, and weaknesses to remediate now and validate with retesting more than time
- Governance, Risk, and Compliance Pentesting Administration
- Enforce compliance requirements for critical restrictions by conducting schedule PCI-DSS pentesting, HIPAA Pentesting and GDPR Tests
- Integrated DevSecOps Remediation
- Improve remediation occasions with DevSecOps remediation built-in during all phases of the pen examination, such as early discovery
- Complete-Stack Visibility Across Programs
- See vulnerabilities by risk and criticality throughout entire-stack techniques, such as apps, gadgets, and networks
- Enhanced Group Workflows
- Improve the pace of security groups and other departments in just the business with integrations for workflow ticketing
- Capacity to Start off the Next Pentest Speedy
- Start out the upcoming penetration examination immediately, and reduce backlogs that are holding back revenue-making initiatives
The Appropriate PTaaS Solution for Continuous Security Validation
Like some other newer offensive security classes, PTaaS has generated a ton of interest promptly – initial with CISOs, and now, far more just lately with product proprietors and other developers with a stake in the DevSecOps system. By natural means, this has attracted a host of new solutions including to the legacy alternatives readily available – building the closing variety of your chosen PTaaS company extra sophisticated.
Contrary to late entrants to the PTaaS marketplace, 3rd bash security provider companies, like BreachLock, are foremost the Pen Tests as a Company group. With an ground breaking continual security validation option and in-house security experts and penetration testers, BreachLock is a proven PTaaS supplier that is rapid, trustworthy, and very affordable. BreachLock provides CIOs and CISOs piece of brain with a new way to meet up with their security validation, pentesting, and compliance demands in fifty percent the time for fifty percent the cost of standard methods. Interested in mastering more? Book a discovery simply call with BreachLock to see how their award-winning, analyst acknowledged PTaaS remedy can work for you right now.
Located this posting fascinating? Stick to us on Twitter and LinkedIn to go through far more distinctive content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 U.K. Electoral Commission Breach Exposes Voter Data of 40 Million Britons
U.K. Electoral Commission Breach Exposes Voter Data of 40 Million Britons