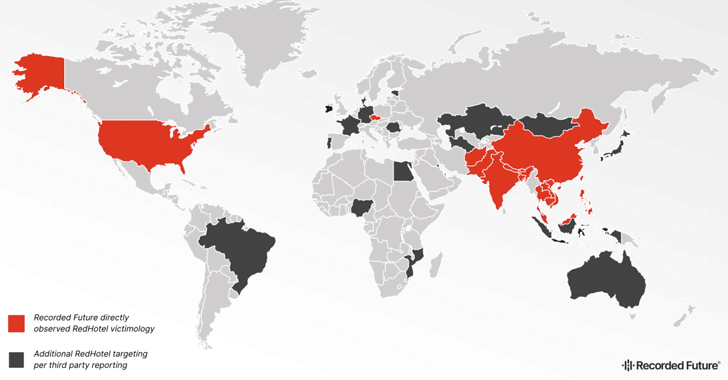
Hackers related with China’s Ministry of Point out Security (MSS) have been linked to attacks in 17 distinct nations in Asia, Europe, and North The united states from 2021 to 2023.
Cybersecurity firm Recorded Foreseeable future attributed the intrusion set to a nation-point out team it tracks below the identify RedHotel (beforehand Danger Exercise Group-22 or TAG-222), which overlaps with a cluster of activity broadly monitored as Aquatic Panda, Bronze University, Charcoal Typhoon, Earth Lusca, and Purple Scylla (or Red Dev 10).
Energetic considering that 2019, some of the popular sectors qualified by the prolific actor encompass academia, aerospace, government, media, telecommunications, and exploration. A the vast majority of the victims for the duration of the time period had been authorities businesses.
“RedHotel has a dual mission of intelligence accumulating and economic espionage,” the cybersecurity corporation reported, contacting out its persistence, operational intensity, and world get to. “It targets equally authorities entities for regular intelligence and organizations included in COVID-19 investigation and technology R&D.”

Pattern Micro, in early January 2022, explained the adversary as a “highly-qualified and hazardous menace actor generally enthusiastic by cyberespionage and money attain.”
The team has since been linked to exploitation of Log4Shell flaws as well as assaults aimed at telecommunications, academia, study and enhancement, and governing administration corporations in Nepal, the Philippines, Taiwan, and Hong Kong to deploy backdoors for long-time period obtain.
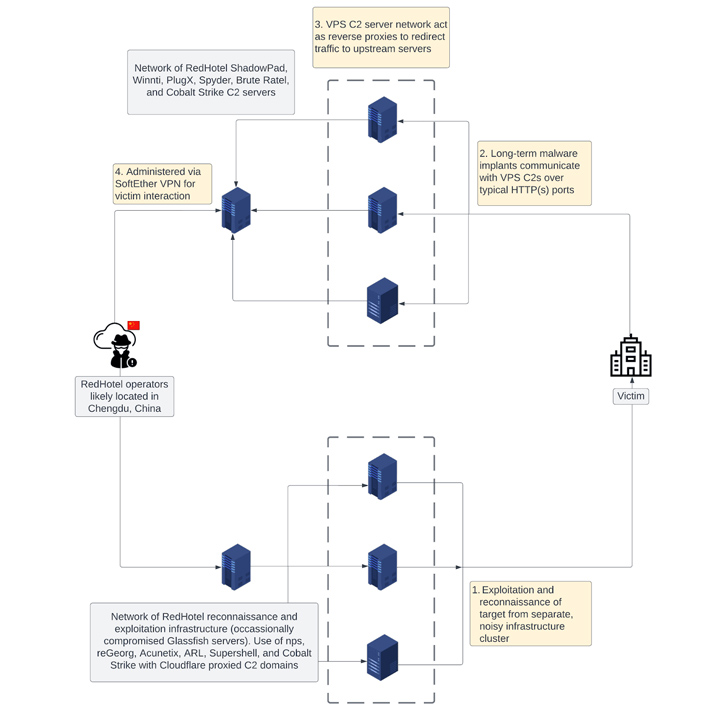
Attack chains mounted by RedHotel have weaponized public-experiencing purposes for initial accessibility, adopted by employing a mixture of offensive security applications like Cobalt Strike and Brute Ratel C4 (BRc4) and bespoke malware people these types of as FunnySwitch, ShadowPad, Spyder, and Winnti.
A noteworthy part of the actor’s modus operandi is the use of a multi-tiered infrastructure, each focusing on original reconnaissance and very long-term network obtain by way of command-and-regulate servers. It predominantly makes use of NameCheap for domain registration.

In a single late 2022 marketing campaign, RedHotel is said to have leveraged a stolen code signing certificate belonging to a Taiwanese gaming corporation to indicator a DLL file responsible for loading BRc4. The write-up-exploitation toolkit, for its component, is configured to talk with abused compromised Vietnamese governing administration infrastructure.
“RedHotel has exemplified a relentless scope and scale of broader PRC state-sponsored cyber-espionage activity by maintaining a superior operational tempo and concentrating on public and personal sector businesses globally,” Recorded Future explained.
The enhancement will come as the Washington Submit claimed that Chinese hackers had “deep, persistent accessibility” to categorised protection networks in Japan, prompting the U.S. National Security Company (NSA), which identified the breach in late 2020, to individually report the make a difference to govt officers.
Identified this report exciting? Comply with us on Twitter and LinkedIn to examine a lot more unique written content we post.
Some parts of this article are sourced from:
thehackernews.com

 Continuous Security Validation with Penetration Testing as a Service (PTaaS)
Continuous Security Validation with Penetration Testing as a Service (PTaaS)