The risk actors guiding the Rhysida ransomware have interaction in opportunistic attacks focusing on companies spanning several marketplace sectors.
The advisory comes courtesy of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-Point out Data Sharing and Assessment Center (MS-ISAC).
“Observed as a ransomware-as-a-assistance (RaaS) design, Rhysida actors have compromised organizations in education and learning, manufacturing, facts technology, and authorities sectors and any ransom paid out is split involving the group and affiliate marketers,” the companies explained.
“Rhysida actors leverage external-experiencing distant services, these kinds of as digital private networks (VPNs), Zerologon vulnerability (CVE-2020-1472), and phishing campaigns to obtain first obtain and persistence within a network.”
Very first detected in May 2023, Rhysida would make use of the time-analyzed tactic of double extortion, demanding a ransom payment to decrypt target knowledge and threatening to publish the exfiltrated info except the ransom is compensated.
It can be also stated to share overlaps with a further ransomware crew identified as Vice Modern society (aka Storm-0832 or Vanilla Tempest), owing to identical targeting designs and the use of NTDSUtil as effectively as PortStarter, which has been solely used by the latter.

According to statistics compiled by Malwarebytes, Rhysida has claimed five victims for the thirty day period of October 2023, placing it significantly at the rear of LockBit (64), NoEscape (40), Engage in (36), ALPHV/BlackCat (29), and 8Foundation (21).
The agencies explained the team as participating in opportunistic attacks to breach targets and using edge of dwelling-off-the-land (LotL) procedures to facilitate lateral motion and create VPN accessibility.
In performing so, the plan is to evade detection by blending in with reputable Windows techniques and network actions.
Vice Society’s pivot to Rhysida has been bolstered in the wake of new investigate posted by Sophos previously final 7 days, which reported it observed the exact same danger actor employing Vice Modern society up until eventually June 2023, when it switched to deploying Rhysida.
The cybersecurity organization is tracking the cluster below the identify TAC5279.
“Notably, in accordance to the ransomware group’s data leak website, Vice Culture has not posted a target because July 2023, which is all over the time Rhysida commenced reporting victims on its site,” Sophos scientists Colin Cowie and Morgan Demboski claimed.
The advancement comes as the BlackCat ransomware Gang is attacking organizations and public entities working with Google advertisements laced with Nitrogen malware, per eSentire.
“This affiliate is getting out Google ads selling common software, these types of as Superior IP Scanner, Slack, WinSCP and Cisco AnyConnect, to entice organization professionals to attacker-controlled internet websites,” the Canadian cybersecurity enterprise claimed.
The rogue installers, which come fitted with Nitrogen, which is an original obtain malware capable of delivering following-stage payloads on to a compromised natural environment, such as ransomware.

“Known examples of ransomware-related preliminary accessibility malware that leverage browser-based attacks incorporate GootLoader, SocGholish, BATLOADER, and now Nitrogen,” eSentire claimed. “Interestingly, ALPHV has been observed as an conclusion-activity for at least two of these browser-based original entry pieces of malware: GootLoader and Nitrogen.”
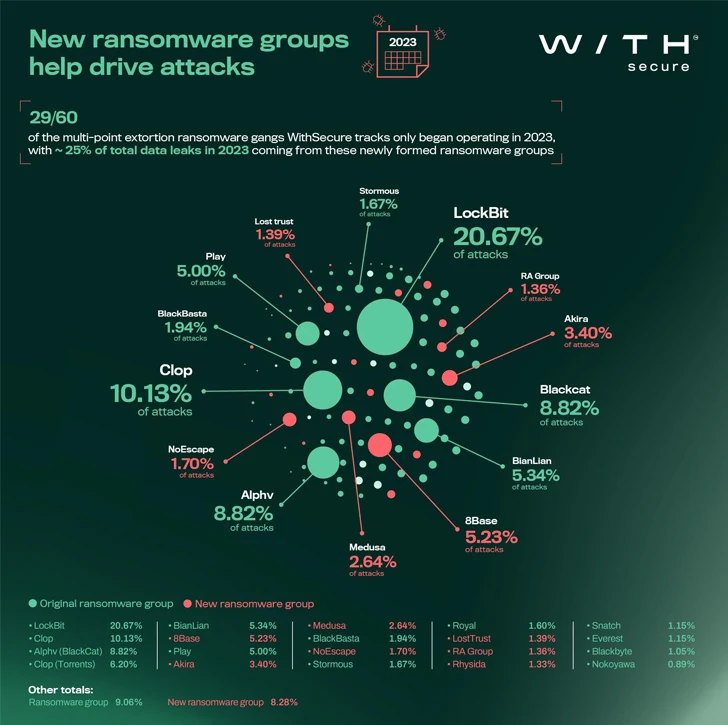
The at any time-evolving mother nature of the ransomware landscape is additional evidenced by the actuality that 29 of the 60 ransomware teams currently energetic commenced functions this yr, per WithSecure, in section pushed by the resource code leaks of Babuk, Conti, and LockBit more than the several years.
“Information leaks are not the only issue that potential customers to more mature groups cross-pollinating younger types,” WithSecure mentioned in a report shared with The Hacker Information.
“Ransomware gangs have team just like an IT firm. And like an IT organization, folks change positions occasionally, and deliver their special abilities and knowledge with them. Compared with legit IT companies, however, you will find practically nothing halting a cyber felony from taking proprietary methods (these as code or resources) from just one ransomware operation and working with it at another. You will find no honor amid thieves.”
Observed this post fascinating? Abide by us on Twitter and LinkedIn to read much more distinctive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Hackers Could Exploit Google Workspace and Cloud Platform for Ransomware Attacks
Hackers Could Exploit Google Workspace and Cloud Platform for Ransomware Attacks