Brazilian banking establishments are the focus on of a new marketing campaign that distributes a customized variant of the Windows-primarily based AllaKore distant accessibility trojan (RAT) referred to as AllaSenha.
The malware is “particularly aimed at thieving qualifications that are demanded to entry Brazilian bank accounts, [and] leverages Azure cloud as command-and-management (C2) infrastructure,” French cybersecurity organization HarfangLab mentioned in a technical investigation.
Targets of the campaign consist of banking institutions this sort of as Banco do Brasil, Bradesco, Banco Safra, Caixa Econômica Federal, Itaú Unibanco, Sicoob, and Sicredi. The first access vector, nevertheless not definitively verified, points to the use of destructive back links in phishing messages.
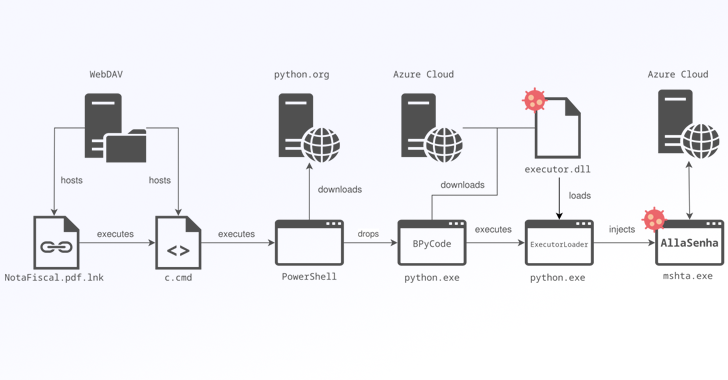
The setting up position of the attack is a malicious Windows shortcut (LNK) file that masquerades as a PDF document (“NotaFiscal.pdf.lnk”) hosted on a WebDAV server considering the fact that at the very least March 2024. There is also evidence to counsel that the danger actors at the rear of the action previously abused genuine services like Autodesk A360 Drive and GitHub to host the payloads.
The LNK file, when introduced, executes a Windows command shell which is developed to open up a decoy PDF file to the receiver, while concurrently retrieving a BAT payload named “c.cmd” from the same WebDAV server site.
Dubbed the BPyCode launcher, the file launches a Foundation64-encoded PowerShell command, which subsequently downloads the Python binary from the formal www.python[.]org web site in purchase to execute a Python script codenamed BPyCode.

BPyCode, for its section, capabilities as a downloader for a dynamic-backlink library (“executor.dll”) and working it in memory. The DLL is fetched from just one of the area names generated by way of a area generation algorithm (DGA).
“Created hostnames look to match these that are associated with the Microsoft Azure Features provider, a serverless infrastructure that in this situation would permit operators to effortlessly deploy and rotate their staging infrastructure,” the organization explained.
Specially, BPyCode retrieves a pickle file that includes 3 files: A 2nd Python loader script, a ZIP archive that contains the PythonMemoryModule offer, and an additional ZIP archive that contains “executor.dll.”
The new Python loader script is then released to load executor.dll, a Borland Delphi-primarily based malware also called ExecutorLoader, in memory using PythonMemoryModule. ExecutorLoader is largely tasked with decoding and executing AllaSenha by injecting it into a legit mshta.exe approach.
In addition to stealing on the internet banking account qualifications from web browsers, AllaSenha will come with the skill to show overlay windows in order to seize two-component authentication (2FA) codes and even trick a sufferer into scanning a QR code to approve a fraudulent transaction initiated by the attackers.
“All AllaSenha samples […] use Entry_Computer_Client_dll.dll as their original file identify,” HarfangLab mentioned. “This name can notably be identified in the KL Gorki venture, a banking malware which seems to merge factors of both AllaKore and ServerSocket.”
More examination of the resource code involved with the initial LNK file and AllaSenha samples has disclosed that a Portuguese-talking consumer named bert1m is most likely connected to the advancement of the malware, though there is no proof at this phase to propose that they are functioning the resources as perfectly.
“The danger actors that function in Latin The us appear to be a specially productive source of cybercrime strategies,” HarfangLab stated.
“While almost solely concentrating on Latin American men and women to steal banking aspects, these actors usually stop up compromising personal computers that are without a doubt operated by subsidiaries or employees in Brazil, but that belong to corporations all all-around the world.”
The progress will come as Forcepoint in-depth malspam campaigns distributing an additional Latin America-centered banking trojan named Casbaneiro (aka Metamorfo and Ponteiro) by means of HTML attachments with an goal to siphon victims’ economic info.
“The malware dispersed through email urges the consumer to click on the attachment,” security researcher Prashant Kumar stated. “The attachment includes destructive code which does a collection of pursuits and qualified prospects to knowledge compromise.”
Anatsa Android Banking Trojan Sneaks into Google Engage in Retail outlet
It can be not just Windows that has been at the getting finish of banking trojan assaults, for Zscaler ThreatLabz disclosed information of an Android banking malware campaign that manufactured use of decoy programs uploaded to the Google Participate in retail outlet to provide Anatsa (aka TeaBot and Toddler).

These clear dropper apps go off as seemingly harmless productivity and utility applications like PDF readers, QR code audience, and translators, mirroring an equivalent infection chain unveiled by ThreatFabric previously this February to retrieve and deploy the malware from a remote server less than the guise of an app update to evade detection.
The apps, which have since been taken down by Google, are listed beneath –
- com.appandutilitytools.fileqrutility (QR Reader & File Supervisor)
- com.ultimatefilesviewer.filemanagerwithpdfsupport (PDF Reader & File Supervisor)
According to studies offered on Sensor Tower, PDF Reader & File Manager has been mounted anyplace concerning 500 to 1,000 situations, while the QR code reader application has experienced installations in the array of 50,000 to 100,000.
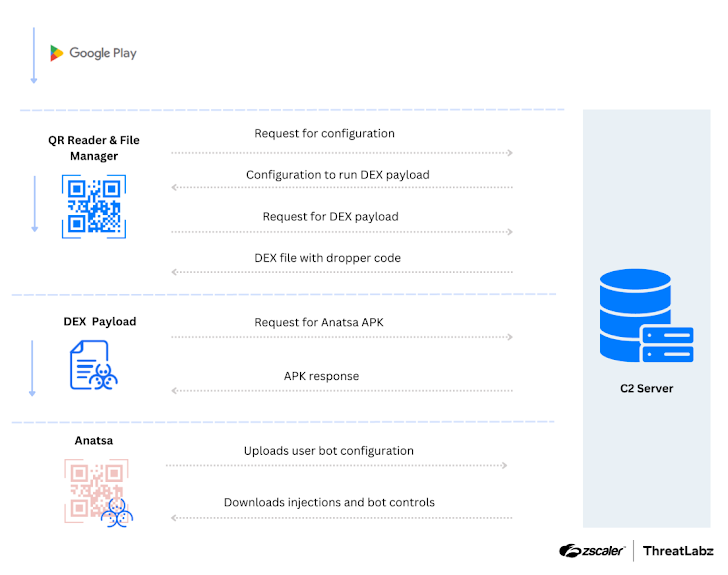
“At the time mounted, Anatsa exfiltrates delicate banking qualifications and fiscal details from worldwide financial purposes,” scientists Himanshu Sharma and Gajanan Khond explained. “It achieves this through the use of overlay and accessibility procedures, making it possible for it to intercept and obtain knowledge discreetly.”
Zscaler explained it recognized more than 90 malicious applications on the Play Store over the earlier couple months that have collectively experienced additional than 5.5 million installations and have been applied to propagate numerous malware people like Joker, Facestealer, Anatsa, Coper, and other adware.
Found this article appealing? Follow us on Twitter and LinkedIn to study more exclusive content material we article.
Some parts of this article are sourced from:
thehackernews.com