A number of security vulnerabilities have been disclosed in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP) that could be likely exploited by a destructive attacker to conduct distant attacks.
“An external attacker who leverages the vulnerabilities uncovered in AudioCodes Ltd.’s desk phones and Zoom’s Zero Touch Provisioning function can acquire whole remote management of the gadgets,” SySS security researcher Moritz Abrell mentioned in an analysis published Friday.
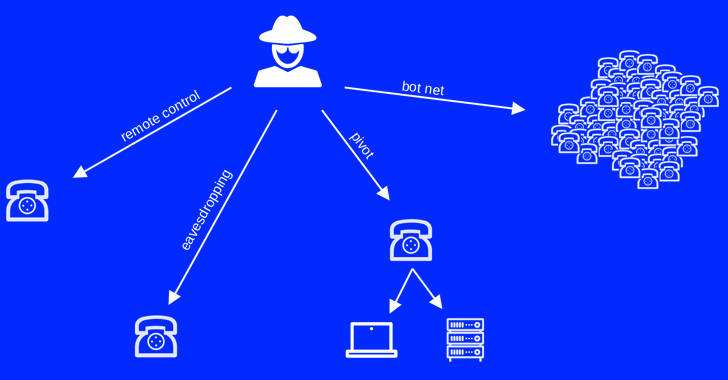
The unfettered entry could then be weaponized to eavesdrop on rooms or phone phone calls, pivot as a result of the units and attack corporate networks, and even build a botnet of contaminated products. The research was introduced at the Black Hat United states security conference previously this 7 days.

The challenges are rooted in Zoom’s ZTP, which makes it possible for IT administrators to configure VoIP products in a centralized fashion these that it will make it uncomplicated for organizations to keep an eye on, troubleshoot and update the devices as and when essential. This is realized by implies of a web server deployed within just the community network to provide configurations and firmware updates to the units.
Precisely, it was discovered to absence consumer-side authentication mechanisms through the retrieval of configuration documents from the ZTP company, thus foremost to a scenario in which an attacker could probably set off the down load of destructive firmware from a rogue server.
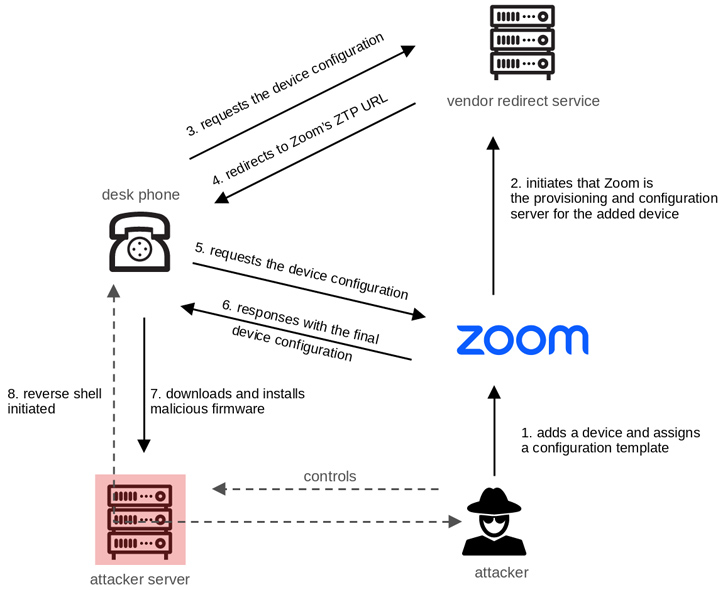
The analyze more uncovered incorrect authentication issues in the cryptographic routines of AudioCodes VoIP desk phones (which guidance Zoom ZTP) that let for the decryption of delicate data, this sort of as passwords and configuration files transmitted by way of a redirection server made use of by the phone to fetch the configuration.
The twin weaknesses, i.e., the unverified possession bug and flaws in the qualified components, could then be fashioned into an exploit chain to provide destructive firmware by abusing Zoom’s ZTP and triggering arbitrary products into putting in it.

“When put together, these vulnerabilities can be utilised to remotely take above arbitrary equipment. As this attack is remarkably scalable, it poses a significant security risk,” Abrell reported.
The disclosure comes approximately a calendar year just after the German cybersecurity firm recognized a security issue in Microsoft Groups Direct Routing performance that could render installations prone to toll fraud assaults.
“An exterior, unauthenticated attacker is capable to mail specially crafted SIP messages that faux to originate from Microsoft and are thus accurately categorised by the victim’s Session Border Controller,” Abrell mentioned at the time. “As a consequence, unauthorized external calls are manufactured as a result of the victim’s phone line.”
Found this short article interesting? Observe us on Twitter and LinkedIn to examine extra special information we submit.
Some parts of this article are sourced from:
thehackernews.com

 Lolek Bulletproof Hosting Servers Seized, 5 Key Operators Arrested
Lolek Bulletproof Hosting Servers Seized, 5 Key Operators Arrested