A zero-working day flaw in the Zimbra Collaboration email computer software was exploited by four distinctive teams in actual-globe attacks to pilfer email info, user qualifications, and authentication tokens.
“Most of this action transpired after the preliminary deal with became general public on GitHub,” Google Risk Assessment Team (TAG) claimed in a report shared with The Hacker News.
The flaw, tracked as CVE-2023-37580 (CVSS score: 6.1), is a reflected cross-internet site scripting (XSS) vulnerability impacting variations prior to 8.8.15 Patch 41. It was dealt with by Zimbra as portion of patches produced on July 25, 2023.
Prosperous exploitation of the shortcoming could permit execution of destructive scripts on the victims’ web browser simply just by tricking them into clicking on a specifically crafted URL, correctly initiating the XSS ask for to Zimbra and reflecting the attack again to the person.

Google TAG, whose researcher Clément Lecigne was credited with identifying and reporting the bug, claimed it learned multiple campaign waves starting June 29, 2023, at least two weeks right before Zimbra issued an advisory.
Three of the four campaigns were being noticed prior to the launch of the patch, with the fourth campaign detected a month immediately after the fixes had been posted.
The initially campaign is explained to have qualified a government business in Greece, sending email messages containing exploit URLs to their targets that, when clicked, shipped an email-thieving malware beforehand noticed in a cyber espionage procedure dubbed EmailThief in February 2022.
The intrusion set, which Volexity codenamed as TEMP_HERETIC, also exploited a then-zero-working day flaw in Zimbra to carry out the assaults.
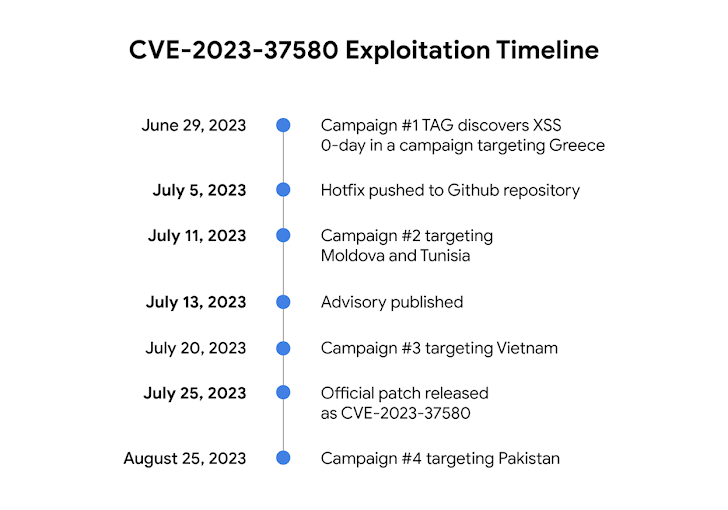
The second danger actor to exploit CVE-2023-37580 is Winter season Vivern, which focused govt corporations in Moldova and Tunisia soon after a patch for the vulnerability was pushed to GitHub on July 5.
It can be worthy of noting that the adversarial collective has been connected to the exploitation of security vulnerabilities in Zimbra Collaboration and Roundcube by Proofpoint and ESET this year.
TAG stated it noticed a third, unidentified group weaponizing the bug right before the patch was pushed on July 25 to phished for qualifications belonging to a federal government business in Vietnam.

“In this case, the exploit URL pointed to a script that shown a phishing website page for users’ webmail qualifications and posted stolen credentials to a URL hosted on an formal authorities domain that the attackers most likely compromised,” TAG observed.
And finally, a governing administration firm in Pakistan was focused working with the flaw on August 25, ensuing in the exfiltration of the Zimbra authentication token to a remote domain named “ntcpk[.]org.”
Google further more pointed out a sample in which threat actors are regularly exploiting XSS vulnerabilities in mail servers, necessitating that these types of purposes are audited thoroughly.
“The discovery of at least four strategies exploiting CVE-2023-37580, 3 strategies following the bug initial grew to become community, demonstrates the worth of businesses applying fixes to their mail servers as soon as attainable,” TAG stated.
“These campaigns also highlight how attackers keep an eye on open-resource repositories to opportunistically exploit vulnerabilities where the fix is in the repository, but not but introduced to buyers.”
Uncovered this article intriguing? Stick to us on Twitter and LinkedIn to browse far more exceptional content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Experts Uncover DarkCasino: New Emerging APT Threat Exploiting WinRAR Flaw
Experts Uncover DarkCasino: New Emerging APT Threat Exploiting WinRAR Flaw