A security vulnerability has been disclosed in the LiteSpeed Cache plugin for WordPress that could empower unauthenticated buyers to escalate their privileges.
Tracked as CVE-2023-40000, the vulnerability was dealt with in October 2023 in variation 5.7..1.
“This plugin suffers from unauthenticated web page-huge saved [cross-site scripting] vulnerability and could permit any unauthenticated user from thieving delicate information to, in this circumstance, privilege escalation on the WordPress internet site by undertaking a one HTTP request,” Patchstack researcher Rafie Muhammad claimed.
LiteSpeed Cache, which is utilised to strengthen internet site general performance, has extra than five million installations. The hottest edition of the plugin in 6.1, which was introduced on February 5, 2024.

The WordPress security corporation said CVE-2023-40000 is the end result of a absence of user input sanitization and escaping output. The vulnerability is rooted in a functionality named update_cdn_status() and can be reproduced in a default installation.
“Due to the fact the XSS payload is placed as an admin detect and the admin recognize could be exhibited on any wp-admin endpoint, this vulnerability also could be quickly triggered by any person that has access to the wp-admin place,” Muhammad claimed.
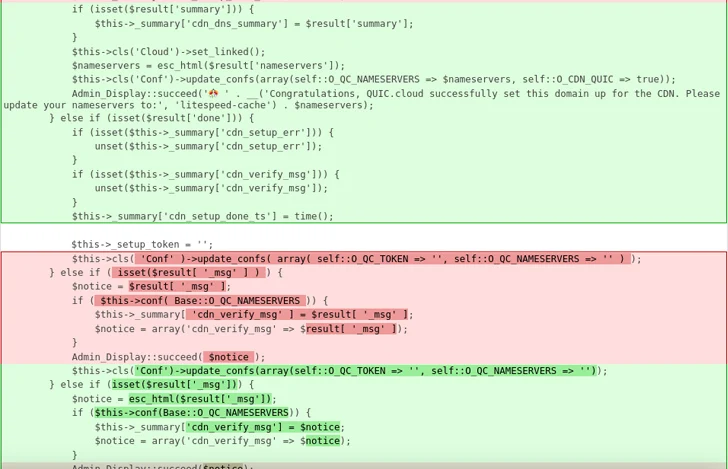
The disclosure comes 4 months following Wordfence exposed an additional XSS flaw in the very same plugin (CVE-2023-4372, CVSS rating: 6.4) because of to inadequate enter sanitization and output escaping on consumer provided attributes. It was dealt with in edition 5.7.
“This will make it possible for authenticated attackers with contributor-degree and earlier mentioned permissions to inject arbitrary web scripts in web pages that will execute when a person accesses an injected website page,” István Márton mentioned.
Identified this posting interesting? Stick to us on Twitter and LinkedIn to read through additional unique material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Open-Source Xeno RAT Trojan Emerges as a Potent Threat on GitHub
Open-Source Xeno RAT Trojan Emerges as a Potent Threat on GitHub