Get exclusive insights from a serious ransomware negotiator who shares reliable tales from network hostage conditions and how he managed them.
The Ransomware Market
Ransomware is an industry. As these types of, it has its personal company logic: businesses spend dollars, in crypto-forex, in get to get back command about their devices and data.
This industry’s landscape is built up of roughly 10-20 main threat actors who initially created the ransomware’s malware. To distribute the malware, they function with affiliate marketers and distributors who employ widespread phishing attacks to breach businesses. Revenue are distributed with roughly 70% allocated to the affiliates and 10%-30% to these developers. The use of phishing renders online-dependent industries, like gaming, finance and insurance policy, in particular vulnerable.
In addition to its monetary motivations, the ransomware marketplace is also motivated by geo-political politics. For instance, in June 2021, subsequent the ransomware assaults on the Colonial Pipeline and JBS, the Byden administration announced that ransomware was a risk to Nationwide Security. The administration then shown critical infrastructures that were “off boundaries” to attackers.
Subsequent these actions, a range of menace actors made a decision to transform study course: declaring they would not attack vital and fundamental corporations like hospitals, power plants and instructional institutions. A couple months later, the FBI described they had attacked well known ransomware group REvil:
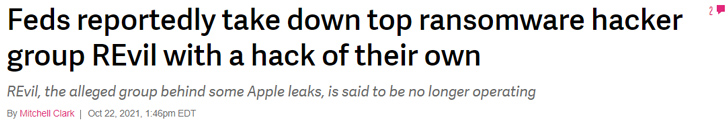
The attack garnered a response from the Conti group, which reflected their ideological motives:

Ransomware Vaccinations
Taking care of a ransomware occasion is very similar to running a hostage circumstance. For that reason, to prepare for a ransomware incident, it is advisable for organizations to utilize a related crisis management composition. This framework is based on the following capabilities:
1. A disaster manager:
- Coordinates the technological, business and lawful tracks.
- The technological track consists of forensic, investigation, containment, remediation and recovery, as well as skilled dialogue. At this phase, the organization and the incident response teams evaluate the scope of the celebration. For illustration, how deep the attackers are in the method, how considerably info was exfiltrated, and many others.
- The business enterprise monitor addresses company continuity plans and media and PR. These are generally executed when the scope of the celebration is clear. It is suggested to be as clear and correct as attainable when issuing public statements.
- The legal observe consists of legal, regulatory and compliance considerations. They monitor what pointers will need to be complied and in which time frames. Sometimes, they will also be the disaster managers.
- The disaster supervisor cannot be the choice-maker.
2. A determination building group:
- The team or person that makes knowledgeable choices based on the data from the crisis supervisor.
3. Regulation enforcement:
- It is proposed to outline this connection in advance. The extent could be as negligible as just informing them and as deep as allowing them to regulate the whole crisis.
4. Insurance:
According to Etay Maor, Senior Director Security Method at Cato Networks, “We are looking at more and far more firms featuring bundles of these ransomware providers. Having said that, it is advisable to separate these roles to guarantee the most professional response.”
The Position of the Professional Negotiator
Professional negotiation is the act of getting benefit of the expert communication with the hacker in a variety of extortion situations. The role contains 4 crucial features:
1. Determining the scope of the event – Normally takes location inside of the initially 24-48 hrs. Involves being familiar with what was compromised, how deep the attackers are in the system, whether the act is a solitary, double or triple ransomware, if the attack was fiscally enthusiastic or if it was a political or personal attack, and many others.
In 90% of circumstances, the attack is fiscally motivated. If it is politically determined, the facts may not be recovered, even soon after shelling out the ransom.
2. Profiling the menace actor – Consists of understanding regardless of whether the team is recognized or not known, their behavioral designs and their organizational construction. Comprehension who the attacker is influences conversation.
For example, by finding out what the nearby time is for the attacker, the negotiator can detect in which they came from. This can be made use of for bettering negotiation conditions, like leveraging general public holiday seasons to check with for a discounted.
3. Evaluating the “expense-of-no-offer” – Reflecting to the determination makers and the disaster administrators what will transpire if they do not spend the ransom.

4. Defining negotiation ambitions – The dilemma is not regardless of whether to pay out or not. That is a organization determination. The objectives of the negotiations are to negotiate for data, for time and for superior phrases. Occasionally, this can final result in a decreased payment, or even enabling the organization to recuperate on its possess.
For instance, a person enterprise was able to purchase 13 days via negotiations, making it possible for them to get well their facts and relinquish spending the ransom completely.
To Spend or Not to Pay?
Etay Maor feedback, “Ransomware is not an IT issue, it is a business issue. “The conclusion whether to spend or not is a small business decision, motivated by lots of things. Even though the formal FBI policy is not to fork out, they empower organizations to do so, if the CEO decides.
For example, in one circumstance an on the web gaming firm was dropping additional cash than the ransom ask for each and every hour their functions had been down, influencing their choice to spend the ransom as rapidly as feasible while reducing negotiation time. US lawmakers have not banned ransomware payment either. This displays how challenging the issue is.
Strategies for Preserving In opposition to Ransomware Assaults
Ransomware is starting to be much more well known, but corporations can defend versus it. Ransomware depends on phishing assaults and unpatched companies. Hence, it is proposed that CEOs meet their IT crew consistently to make sure application and infrastructure are patched and up-to-date and that all crucial details is backed up. This will noticeably lessen the chance of ransomware staying in a position to exploit vulnerabilities and penetrate programs.
To learn more about ransomware attacks and how they are managed in serious-time, observe the whole masterclass right here.
Observed this article intriguing? Stick to us on Twitter and LinkedIn to study much more distinctive material we post.
Some parts of this article are sourced from:
thehackernews.com


 Cisco Counterfeiter Pleads Guilty to $100m Scheme
Cisco Counterfeiter Pleads Guilty to $100m Scheme