Halting new and evasive threats is a person of the best worries in cybersecurity. This is among the the biggest motives why assaults enhanced dramatically in the earlier year however once more, regardless of the believed $172 billion invested on international cybersecurity in 2022.
Armed with cloud-based tools and backed by sophisticated affiliate networks, menace actors can acquire new and evasive malware a lot more speedily than businesses can update their protections.
Relying on malware signatures and blocklists from these swiftly switching assaults has turn into futile. As a result, the SOC toolkit now mostly revolves all-around threat detection and investigation. If an attacker can bypass your original blocks, you assume your resources to select them up at some stage in the attack chain. Each and every organization’s digital architecture is now seeded with security controls that log anything possibly destructive. Security analysts pore by way of these logs and ascertain what to investigate even further.
Does this work? Let’s search at the quantities:
- 76% of security teams say that they won’t be able to hit their goals due to the fact they are understaffed
- 56% of assaults get months—or longer—to discover
- Assaults maintain rising: the world cost of cybercrime is anticipated to reach $10.5 trillion by 2025
Plainly, anything wants to alter. Detection systems provide an essential objective and investing in them isn’t really improper, but it has undoubtedly been overemphasized.
Organizations need to have to get again to prioritizing risk prevention very first and foremost—and this is coming from the chief in zero trust, a product that fundamentally assumes your avoidance controls have by now unsuccessful and that you are actively remaining breached at any provided time.
The endpoint is just the setting up place
Though quite a few security categories exemplify the gaps in detection-to start with security tactics, let’s glance at a single well known classification in unique: endpoint detection and response (EDR).
EDR adoption has grown like wildfire. Previously a $2 billion sector, it truly is escalating at a CAGR of 25.3%. It tends to make feeling: most assaults start out at the endpoint, and if you detect them early in the attack chain, you limit the effects. A great EDR option also presents wealthy endpoint telemetry to assist with investigations, compliance, and obtaining and shutting down vulnerabilities.
Endpoint security is a valuable location to devote in—and a critical ingredient of zero trust—but it is not the full photo. Inspite of seller promises of “extended” detection and response that stitches alongside one another details throughout the company, XDR alternatives do not offer protection-in-depth on their individual. EDRs have antivirus to halt recognised malware, but they normally permit all other website traffic to pass by means of, counting on analytics to sooner or later detect what the AV missed.
All applications have their shortcomings, and EDR is no exception, mainly because:
Not all assaults start at the endpoint. The Internet is the new network, and most companies have a huge assortment of information and apps stored throughout many clouds. They also routinely use units like VPNs and firewalls that are routable from the internet. Something that is uncovered is matter to an attack. Zscaler ThreatLabz has discovered that 30% of SSL-based attacks cover in cloud-centered file-sharing expert services like AWS, Google Travel, OneDrive, and Dropbox.
Not all endpoints are managed. EDR relies on brokers that are set up on each IT-managed machine, but that will not account for the myriad scenarios in which unmanaged endpoints may well contact your facts or networks: IoT and OT devices, private (BYOD) endpoints employed for get the job done, 3rd-party associates and contractors with access to data, recent mergers or acquisitions, even company coming to your office to use Wi-Fi.
EDR can be bypassed. All security resources have their weaknesses, and EDR has verified to be reasonably uncomplicated to evade employing many popular methods, these kinds of as exploiting program phone calls. Attackers use encryption and obfuscation approaches to mechanically create new PDFs, Microsoft 365 files, and other files that can alter the fingerprint of malware and bypass classic cybersecurity versions undetected.
Contemporary threats transfer truly quickly. Modern ransomware strains, pretty much all obtainable for acquire on the dark web for any would-be cybercriminals, can encrypt data significantly too swiftly for detection-primarily based systems to be beneficial. LockBit v3. can encrypt 25,000 files in a minute, and it’s not even the quickest ransomware out there. Conversely, the average time to detect and mitigate a breach has been calculated at 280 days. Which is more than enough time for LockBit to encrypt more than 10 billion files.
Get your security in line
It really is accurate that signature-based mostly antivirus systems are no for a longer time more than enough to halt complex assaults. But it is also legitimate that the exact same AI-run analytics at the rear of detection technologies can (and should!) be used for avoidance, not just detection, if they are delivered inline. This prevention approach wants to account for your entire infrastructure, not just your endpoints or any other one particular section of your architecture.
A sandbox is a key instance of a security instrument that can be deployed in this way. Sandboxes offer true-time protection in opposition to innovative and unidentified threats by examining suspicious information and URLs in a protected, isolated atmosphere. Deploying them inline (somewhat than as a passthrough) means a file is just not authorized to carry on till after the answer provides a verdict.
The Zscaler Zero Have confidence in Trade system incorporates a cloud-native proxy that inspects all visitors, encrypted or not, to enable protected accessibility. As a proxy, the platform’s layered controls—including the built-in innovative sandbox—are all shipped inline with a prevention-first solution.
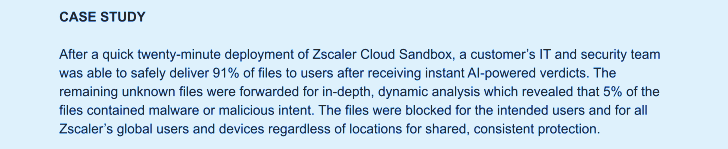
Supplementing your detection technologies with Zscaler’s cloud indigenous inline sandbox presents you:
Authentic-time, AI-driven defense towards zero-working day threats
Zscaler works by using state-of-the-art equipment learning algorithms that are frequently refined by the world’s most significant security cloud, which processes additional than 300 billion transactions per day. These algorithms assess suspicious files and URLs in real time, detecting and blocking probable threats prior to they can lead to damage.
This starts with a prefiltering assessment that checks the file’s written content from 40+ menace feeds, antivirus signatures, hash blocklists, and YARA regulations for identified indicators of compromise (IOCs). By minimizing the range of documents required for further investigation, AI/ML styles execute much more effectively. When a file remains unidentified or suspicious soon after preliminary triage, Zscaler Sandbox detonates it to conduct sturdy static, dynamic, and secondary investigation, which include code and secondary payload evaluation that detects state-of-the-art evasion approaches. After complete, a report is produced with a menace score and actionable verdict, blocking destructive and suspicious data files primarily based on coverage configurations.
Scalability
A person of the most significant offering details of the cloud is the skill to promptly scale up or down to satisfy the desires of corporations of all sizes. Security controls deployed in the cloud are by natural means less complicated to provision and handle, providing your business the versatility to adapt to shifting security requirements.
Minimized costs
Value is one particular of the principal inputs defining several security techniques, and it will come in numerous sorts: consumer productiveness, operational performance, components costs, and so on. But the biggest expense of observe is the cost of obtaining breached. By blocking attacks, you get rid of downtime, reputational harm, shed business, and remediation fees, all of which can effortlessly add up to seven figures for a one attack. ESG discovered that the normal corporation making use of the Zero Have confidence in Exchange experiences a 65% reduction in malware, an 85% reduction in ransomware, and a 27% reduction in information breaches, contributing to an total ROI of 139%.
Comprehensive menace protection
The Zero Rely on Trade delivers extensive menace prevention, detection, and evaluation abilities, offering companies with a uniform security handle method across all spots, users, and equipment. Zscaler Sandbox can review files any place, not just on the endpoint, and is integrated with a range of added abilities these kinds of as DNS security, browser isolation (for fileless attacks), details loss prevention, application and workload security, deception, and a lot of some others. This gives a entire view of your organization’s security posture and the protection-in-depth that security teams strive for.
Avoidance will come in first
In the arms race against attackers, security teams need to have to prioritize inline security controls around passthrough detection systems. Files shouldn’t be permitted onto endpoints or networks unless of course you’re sure they are benign—because if they turn out to be malicious, probabilities are you will never locate out about them until eventually immediately after the injury is carried out.
If you would like to study a lot more about the Zscaler Zero Have faith in Trade, visit zscaler.com.
Located this write-up appealing? Observe us on Twitter and LinkedIn to browse a lot more distinctive content we article.
Some parts of this article are sourced from:
thehackernews.com


 Zyxel Firewall Devices Vulnerable to Remote Code Execution Attacks — Patch Now
Zyxel Firewall Devices Vulnerable to Remote Code Execution Attacks — Patch Now