How’s your vulnerability management application doing? Is it efficient? A achievements? Let’s be genuine, devoid of the proper metrics or analytics, how can you notify how perfectly you might be undertaking, progressing, or if you’re acquiring ROI? If you are not measuring, how do you know it’s doing the job?
And even if you are measuring, defective reporting or focusing on the wrong metrics can make blind spots and make it more challenging to communicate any pitfalls to the relaxation of the enterprise.
So how do you know what to concentration on? Cyber cleanliness, scan coverage, typical time to repair, vulnerability severity, remediation costs, vulnerability exposure… the list is unlimited. Each individual tool on the sector delivers diverse metrics, so it can be tricky to know what is essential.
This posting will enable you identify and determine the essential metrics that you need to keep track of the point out of your vulnerability management software, the development you’ve made, so you can build audit-prepared studies that:
- Establish your security posture
- Meet up with vulnerability remediation SLAs and benchmarks
- Assist move audits and compliance
- Exhibit ROI on security instruments
- Simplify risk examination
- Prioritize resource allocation
Why you need to measure vulnerability management
Metrics play a critical part in gauging the performance of your vulnerability and attack area management. Measuring how immediately you come across, prioritize and resolve flaws suggests you can consistently watch and improve your security.
With the suitable analytics, you can see which issues are extra critical, prioritize what to take care of first, and evaluate the development of your efforts. In the long run, the appropriate metrics enable you to make appropriately educated selections, so you are allocating the assets to the proper sites.
The selection of vulnerabilities observed is often a good beginning position, but it doesn’t explain to you considerably in isolation – with out prioritization, advisories and progress, where do you begin? Getting, prioritizing and repairing your most critical vulnerabilities is significantly much more essential to your small business operations and details security than only acquiring each individual vulnerability.
Intelligent prioritization and filtering out the sounds are vital due to the fact overlooking legitimate security threats is all much too easy when you’re currently being confused by non-vital information. Smart outcomes make your position a lot easier by prioritizing issues that have actual impression on your security, with out burdening you with irrelevant weaknesses.
For illustration, your internet-experiencing systems are the least difficult targets for hackers. Prioritizing issues that leave this exposed can make it less difficult to minimize your attack surface area. Applications like Intruder make vulnerability administration simple even for non-experts, by conveying the actual hazards and delivering remediation advice in uncomplicated-to-comprehend language. But outside of prioritization, what else need to or could you be measuring?
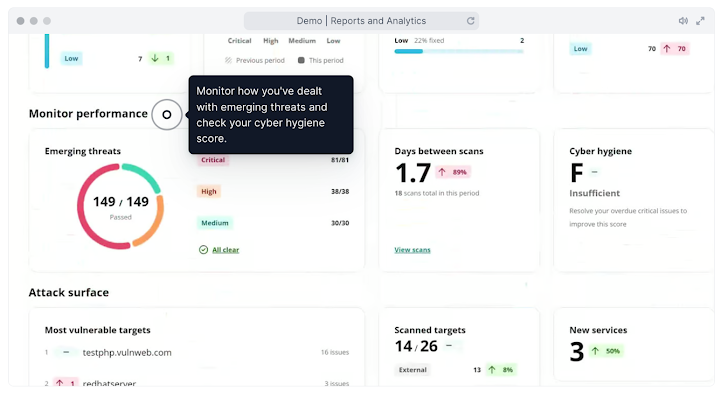
 An illustration of Intruder’s vulnerability administration report page
An illustration of Intruder’s vulnerability administration report page
5 prime metrics for each individual vulnerability administration program
Scan protection
What are you tracking and scanning? Scan protection contains all the belongings you’re masking and analytics of all small business-critical assets and applications, and the variety of authentication available (e.g., username- and password-dependent, or unauthenticated).
As your attack surface evolves, variations and grows more than time, it truly is significant to monitor any changes to what is lined and your IT ecosystem, these types of as just lately opened ports and solutions. A contemporary scanner will detect deployments you may perhaps not have been informed of and reduce your sensitive info from getting to be inadvertently uncovered. It must also observe your cloud units for adjustments, learn new belongings, and instantly synchronize your IPs or hostnames with cloud integrations.
Common time to correct
The time it will take your crew to take care of your critical vulnerabilities reveals how responsive your crew is when reacting to the success of any claimed vulnerabilities. This should be persistently lower due to the fact the security group is accountable for resolving issues and offering the message and motion plans for remediation to administration. It should also be based on your pre-outlined SLA. The severity of the vulnerability need to have a corresponding relative or an complete time period of time for planning and remediation.
Risk score
The severity of every issue is mechanically calculated by your scanner, ordinarily Critical, Higher or Medium. If you make a decision not to patch a specific or group of vulnerabilities inside a specified time period, this is an acceptance of risk. With Intruder you can snooze an issue if you happen to be inclined to accept the risk and there are mitigating elements.
For example, when you’re preparing for a SOC2 or ISO audit and you can see a critical risk, you could be prepared to acknowledge it due to the fact the source necessary to repair it is not justified by the real degree of risk or likely impression on the company. Of class, when it will come to reporting, your CTO may want to know how numerous issues are currently being snoozed and why!
Issues
This is the stage from a vulnerability going general public, to obtaining scanned all targets and detecting any issues. In essence, how speedily are vulnerabilities getting detected across your attack floor, so you can correct them and decrease the window of prospect for an attacker.
What does this signify in observe? If your attack area is escalating, you may perhaps obtain that it usually takes you more time to scan almost everything comprehensively, and your indicate time to detect might boost as effectively. Conversely, if your signify time to detect stays flat or goes down, you happen to be making use of your resources effectively. If you get started to see the reverse, you should ask by yourself why it can be using more time to detect factors? And if the remedy is the attack area has ballooned, possibly you need to invest additional in your tooling and security crew.

Measuring progress
Prioritization – or intelligent success – is important to support you make a decision what to take care of initial, because of its potential impression on your enterprise. Intruder filters out the sounds and assists reduce untrue positives, which is a critical metric to keep track of mainly because at the time you reduce the sum of noise you can circle back and concentrate on the most vital metric – the average time to correct.
Why is this important? Because when you do uncover an issue, you want to be capable to deal with it as promptly as possible. Resources like Intruder use several scanning engines to interprets the output and prioritize the effects according to context, so you can save time and focus on what seriously issues.
 When a new vulnerability that could critically impact your techniques is recognized, Intruder will routinely kick-off a scan
When a new vulnerability that could critically impact your techniques is recognized, Intruder will routinely kick-off a scan
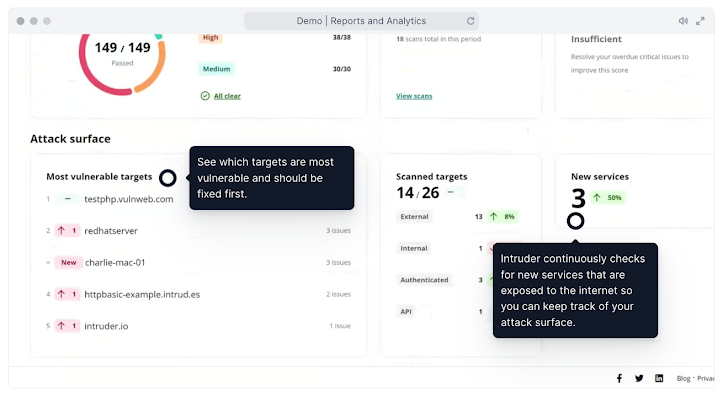
Attack surface monitoring
This assists you see the proportion of assets that are protected across your attack area, found or undiscovered. As you team spins up new applications, vulnerability scanner must verify when a new provider is uncovered, so you can avoid data from becoming inadvertently uncovered. Fashionable scanners watch your cloud devices for changes, locating new belongings, and synchronizing your IPs or hostnames with your integrations.
Why is this vital? Your attack surface will inevitably evolve over time, from open up ports to spinning up new cloud cases, you will need to keep track of these improvements to lessen your exposure. Which is the place our attack surface discovery will come in. The selection of new expert services found out during the time period specified can help you have an understanding of if your attack area is growing (whether intentionally or not).
Why these metrics issue
Modern attack floor administration resources like Intruder measure what matters most. They help deliver studies for stakeholders and compliance with vulnerabilities prioritized and integrations with your issue monitoring applications. You can see what’s vulnerable and get the actual priorities, solutions, insights, and automation you have to have to control your cyber risk. If you want to see Intruder in action you can request a demo or consider it for no cost for 14 times.
Located this write-up intriguing? Abide by us on Twitter and LinkedIn to study much more exclusive information we article.
Some parts of this article are sourced from:
thehackernews.com


 Warning: New Malware Emerges in Attacks Exploiting Ivanti VPN Vulnerabilities
Warning: New Malware Emerges in Attacks Exploiting Ivanti VPN Vulnerabilities