Whilst supposed for advantage and effective communication, email car-forwarding policies can inadvertently lead to the unauthorized dissemination of sensitive information to external entities, placing private data at risk of publicity to unauthorized parties. Wing Security (Wing), a SaaS security business, announced yesterday that their SaaS shadow IT discovery techniques now consist of a remedy that solves for auto-email forwarding as very well. Whilst Wing’s shadow IT solution is available as a absolutely free device that can be onboarded and employed as a self-services, consumers eager to upgrade will be capable to delight in the company’s new Gmail and Outlook integrations, which broaden the firm’s discovery abilities and increase their info security options.
The hazards of email car-forwarding procedures
Automobile-forwarding e-mails is a wonderful way to preserve time on repetitive jobs and are for that reason very well known amid workers who regularly collaborate and share info with exterior company companions. Risk illustrations incorporate:
- Automation usually means no just one is examining for sensitive or non-public details. Email messages with a particular phrase combination in the title, or a specific sender, will mechanically be forwarded to an external entity without having any oversight. This can guide to PII info leakage, sensitive facts leakage and regulatory violations that can compromise an organization’s compliance.
- Auto-forwarding can also point out a prospective insider risk. A disgruntled staff may possibly car-ahead sure e-mails to opponents. It can also be as popular as an employee who plans to leave the enterprise and needs to maintain access to their get the job done immediately after they depart – vehicle-forwarding emails to their private email account.
- Destructive actors could possibly use this as an entry point. Negative actors can use these email forwarding rules to exfiltrate data soon after a productive attack, or as a indicates to unfold phishing strategies within businesses.
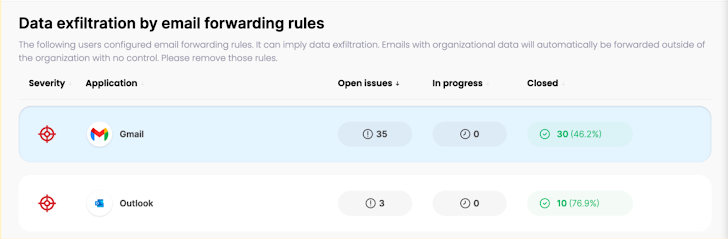 Screenshot from Wing’s system, car-forwarding issues uncovered in gmail and Outlook
Screenshot from Wing’s system, car-forwarding issues uncovered in gmail and Outlook
What is the relationship between SaaS Security and email Security?
For numerous reasons, it is vital for businesses to uncover SaaS Shadow IT apps. Shadow IT refers to the unauthorized use of IT methods within an business, normally for the sake of convenience or performance, with out the express acceptance of the IT division. There are some SaaS applications that could pose substantial risks to the organization’s security, compliance, and total efficiency:
- Security Pitfalls: SaaS purposes are portion of the fashionable source chain, and as this kind of they really should bear correct seller risk assessments and consumer obtain opinions prior to connecting them to organization data. With Shadow IT, breached apps, non-compliant apps or destructive purposes go unnoticed.
- Compliance Worries: Lots of industries have stringent regulatory requirements that ought to be adhered to, significantly about data privateness and security. Employing unauthorized purposes can outcome in non-compliance, primary to authorized penalties, fines, and problems to the organization’s track record.
- Monetary Implications: Uncontrolled proliferation of Shadow IT applications can guide to avoidable expenditure. Corporations might finish up paying out for redundant providers or copy accounts, leading to negligent paying and economical squander.
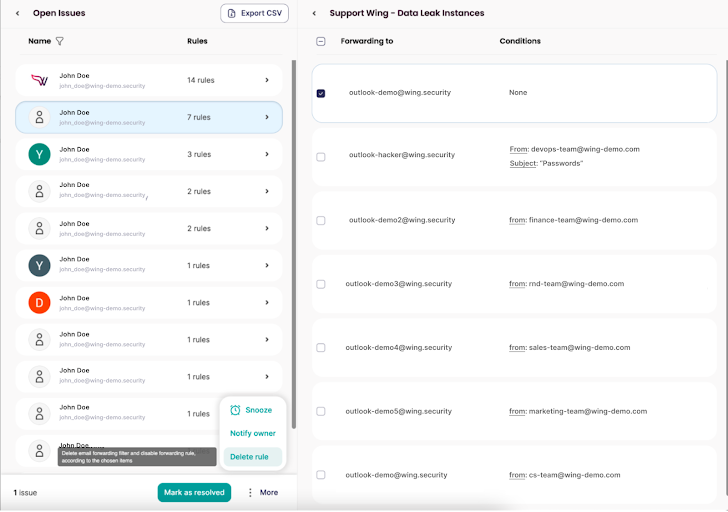 Wing’s product or service illustration – risky email forwarding rules
Wing’s product or service illustration – risky email forwarding rules
Wing’s SaaS discovery entails the systematic identification, categorization, and assessment of an organization’s SaaS usage to mitigate shadow IT hazards. The corporation delivers three distinctive and non-intrusive discovery methods: Connecting to organizations’ significant SaaS purposes (e.g., Google Push, Salesforce, Slack, and other folks) to establish connected purposes, scanning endpoints for SaaS signature hits and cross-examining them with Wing’s considerable SaaS database of around 280,000 SaaS documents. Their third and freshly released ability includes connecting to organization e-mail and conducting scans to detect distinct indications of SaaS usage. Wing emphasizes that realizing is just the to start with stage in fixing and as a result gives prospects the signifies to remediate and eradicate risky shares specifically in just their platform.
Found this report appealing? Adhere to us on Twitter and LinkedIn to study far more special information we post.
Some parts of this article are sourced from:
thehackernews.com

 MuddyC2Go: New C2 Framework Iranian Hackers Using Against Israel
MuddyC2Go: New C2 Framework Iranian Hackers Using Against Israel