A beforehand undocumented “phishing empire” has been linked to cyber assaults aimed at compromising Microsoft 365 enterprise email accounts around the previous 6 years.
“The menace actor established a concealed underground industry, named W3LL Keep, that served a shut neighborhood of at least 500 threat actors who could acquire a tailor made phishing package known as W3LL Panel, developed to bypass MFA, as properly as 16 other completely custom made tools for small business email compromise (BEC) assaults,” Group-IB stated in a report shared with The Hacker Information.
The phishing infrastructure is approximated to have focused more than 56,000 corporate Microsoft 365 accounts and compromised at minimum 8,000 of them, mostly in the U.S., the U.K., Australia, Germany, Canada, France, the Netherlands, Switzerland, and Italy amongst Oct 2022 and July 2023, netting its operators $500,000 in illicit gains.
Some of the well known sectors infiltrated making use of the phishing solution include things like manufacturing, IT, consulting, money expert services, healthcare, and legal products and services. Group-IB said it discovered near to 850 distinctive phishing internet sites attributed to the W3LL Panel for the duration of the very same time interval.
The Singapore-headquartered cybersecurity company has explained W3LL as an all-in-1 phishing instrument that presents an whole spectrum of expert services ranging from tailor made phishing equipment to mailing lists and obtain to compromised servers, underscoring the upward development of phishing-as-a-company (PhaaS) platforms.

Lively due to the fact 2017, the risk actor driving the package has a storied background of producing bespoke software program for bulk email spam (named PunnySender and W3LL Sender) in advance of turning their consideration to placing up phishing applications for compromising company email accounts.
A main element of W3LL’s malware arsenal is an adversary-in-the-middle (AiTM) phishing package that can bypass multi-component authentication (MFA) protections. It is available for sale for $500 for a 3-month subscription with a subsequent month to month fee of $150.
The panel, moreover harvesting qualifications, packs in anti-bot performance to evade automatic web information scanners and extend the lifespan of their phishing and malware strategies.
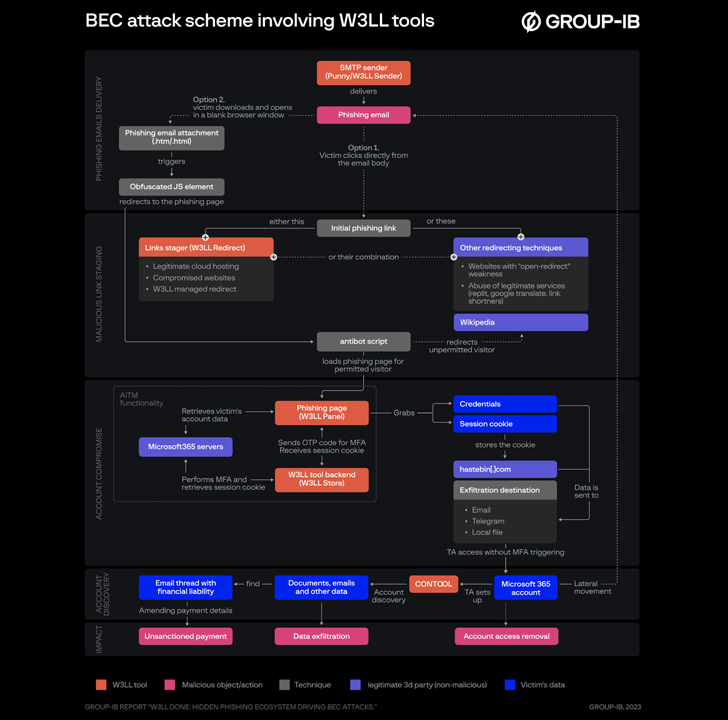
BEC assaults leveraging the W3LL phishing kit entail a preparatory period to validate email addresses working with an auxiliary utility referred to as LOMPAT and provide the phishing messages.
Victims who open the bogus url or attachment are gated by means of the anti-bot script to filter out unpermitted website visitors (who are directed to Wikipedia) and finally just take them to the phishing landing web page by means of a redirect chain that employs AitM methods to siphon qualifications and session cookies.
Armed with this entry, the danger actor then proceeds to login to the target’s Microsoft 365 account devoid of triggering MFA, automate account discovery on the host employing a custom made tool dubbed CONTOOL, and harvest email messages, phone quantities, and other information.
Impending WEBINARDetect, React, Secure: ITDR and SSPM for Full SaaS Security
Uncover how Identification Risk Detection & Reaction (ITDR) identifies and mitigates threats with the support of SSPM. Discover how to safe your corporate SaaS applications and guard your data, even following a breach.
Supercharge Your Competencies
Some of the notable methods adopted by the malware creator are the use of Hastebin, a file-sharing company, to keep stolen session cookies as effectively as Telegram and email to exfiltrate the credentials to the felony actors.
The disclosure arrives days after Microsoft warned of a proliferation of AiTM procedures deployed via PhaaS platforms this sort of as EvilGinx, Modlishka, Muraena, EvilProxy, and Greatness to allow customers entry to privileged systems without re-authentication at scale.
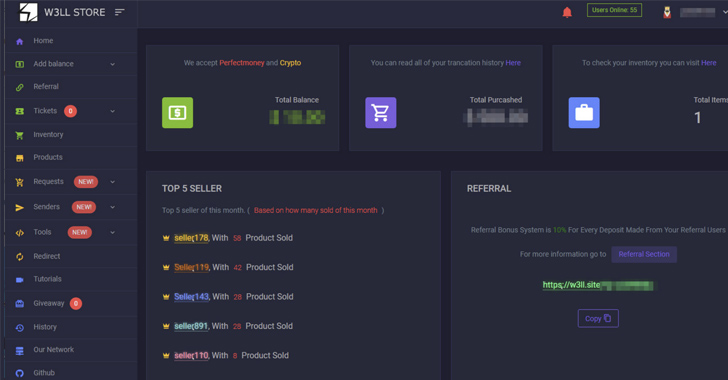
“What actually helps make W3LL Store and its products stand out from other underground marketplaces is the fact that W3LL created not just a market but a intricate phishing ecosystem with a thoroughly compatible tailor made toolset that addresses almost full killchain of BEC and can be utilised by cybercriminals of all technological talent amounts,” Team-IB’s Anton Ushakov claimed.
“The developing demand for phishing applications has made a thriving underground market, attracting an escalating number of sellers. This levels of competition drives continual innovation amongst phishing developers, who look for to improve the effectiveness of their destructive tools via new attributes and methods to their felony operations.”
Located this write-up interesting? Abide by us on Twitter and LinkedIn to read through more distinctive content material we submit.
Some parts of this article are sourced from:
thehackernews.com

 Ukraine’s CERT Thwarts APT28’s Cyberattack on Critical Energy Infrastructure
Ukraine’s CERT Thwarts APT28’s Cyberattack on Critical Energy Infrastructure