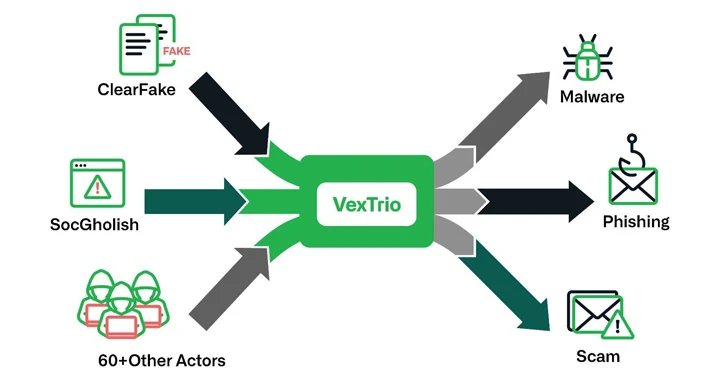
The danger actors at the rear of ClearFake, SocGholish, and dozens of other actors have established partnerships with an additional entity known as VexTrio as portion of a massive “prison affiliate method,” new results from Infoblox expose.
The most recent improvement demonstrates the “breadth of their routines and depth of their connections inside of the cybercrime business,” the organization stated, describing VexTrio as the “one major malicious website traffic broker explained in security literature.”
VexTrio, which is thought to be have been lively considering the fact that at minimum 2017, has been attributed to malicious campaigns that use domains produced by a dictionary domain generation algorithm (DDGA) to propagate scams, riskware, spyware, adware, probably unwanted systems (PUPs), and pornographic information.
This also involves a 2022 exercise cluster that dispersed the Glupteba malware following an before attempt by Google to acquire down a considerable chunk of its infrastructure in December 2021.
In August 2023, the group orchestrated a widespread attack involving compromised WordPress web sites that conditionally redirect readers to intermediary command-and-control (C2) and DDGA domains.
What manufactured the infections considerable was the simple fact that the threat actor leveraged the Domain Name Procedure (DNS) protocol to retrieve the redirect URLs, properly acting as a DNS-based targeted traffic distribution (or shipping or course) procedure (TDS).

VexTrio is approximated to run a network of a lot more than 70,000 regarded domains, brokering targeted traffic for as many as 60 affiliate marketers, together with ClearFake, SocGholish, and TikTok Refresh.
“VexTrio operates their affiliate application in a one of a kind way, giving a small variety of focused servers to every affiliate,” Infoblox reported in a deep-dive report shared with The Hacker Information. “VexTrio’s affiliate associations show up longstanding.”
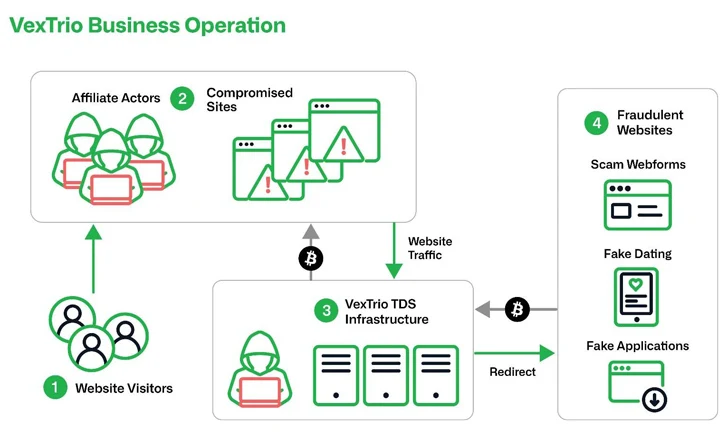
Not only can its attack chains can involve various actors, VexTrio also controls a number of TDS networks to route web site people to illegitimate material based mostly on their profile attributes (e.g. geolocation, browser cookies, and browser language options) in get to optimize income, when filtering out the relaxation.
These attacks function infrastructure owned by diverse get-togethers wherein taking part affiliate marketers ahead traffic originating from their possess resources (e.g., compromised websites) to VexTrio-managed TDS servers. In the following stage, this targeted visitors is relayed to other fraudulent websites or malicious affiliate networks.
“VexTrio’s network employs a TDS to take in web targeted traffic from other cybercriminals, as well as market that targeted traffic to its own shoppers,” the researchers stated. “VexTrio’s TDS is a large and advanced cluster server that leverages tens of countless numbers of domains to take care of all of the network targeted traffic passing by it.”

The VexTrio-operated TDS comes in two flavors, just one which is dependent on HTTP that handles URL queries with unique parameters, and one more primarily based on DNS, the latter of which began to be first place to use in July 2023.
It is really really worth noting at this phase that whilst SocGholish (aka FakeUpdates) is a VexTrio affiliate, it also operates other TDS servers, these types of as Keitaro and Parrot TDS, with the latter acting as a mechanism for redirecting web website traffic to SocGholish infrastructure.
In accordance to Palo Alto Networks Unit 42, Parrot TDS has been energetic considering the fact that October 2021, even though there is proof to advise that it could have been close to as early as August 2019.
“Web-sites with Parrot TDS have malicious scripts injected into present JavaScript code hosted on the server,” the organization pointed out in an investigation last 7 days. “This injected script is composed of two components: an first landing script that profiles the target, and a payload script that can immediate the victim’s browser to a malicious place or piece of material.”

The injections, in flip, are facilitated by the exploitation of recognized security vulnerabilities in material administration programs (CMS) this kind of as WordPress and Joomla!
The attack vectors adopted by the VexTrio affiliate network for gathering victim targeted visitors is no various in that they primarily single out web-sites running a susceptible variation of the WordPress computer software to insert rogue JavaScript into their HTML pages.
In just one occasion recognized by Infobox, a compromised web page based mostly in South Africa was discovered to be injected with JavaScript from ClearFake, SocGholish, and VexTrio.
That’s not all. Moreover contributing web website traffic to several cyber campaigns, VexTrio is also suspected to carry out some of its possess, producing money by abusing referral programs and receiving web site visitors from an affiliate and then reselling that visitors to a downstream danger actor.
“VexTrio’s state-of-the-art business enterprise model facilitates partnerships with other actors and creates a sustainable and resilient ecosystem that is extremely hard to ruin,” Infoblox concluded.
“Because of to the elaborate layout and entangled mother nature of the affiliate network, precise classification and attribution is difficult to reach. This complexity has permitted VexTrio to flourish even though remaining anonymous to the security field for in excess of six several years.”
Uncovered this posting exciting? Stick to us on Twitter and LinkedIn to examine much more exceptional material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Malicious NPM Packages Exfiltrate Hundreds of Developer SSH Keys via GitHub
Malicious NPM Packages Exfiltrate Hundreds of Developer SSH Keys via GitHub