The China-nexus cyber espionage actor linked to the zero-working day exploitation of security flaws in Fortinet, Ivanti, and VMware gadgets has been observed employing various persistence mechanisms in get to sustain unfettered entry to compromised environments.
“Persistence mechanisms encompassed network gadgets, hypervisors, and digital devices, making certain choice channels continue being accessible even if the major layer is detected and eliminated,” Mandiant researchers claimed in a new report.
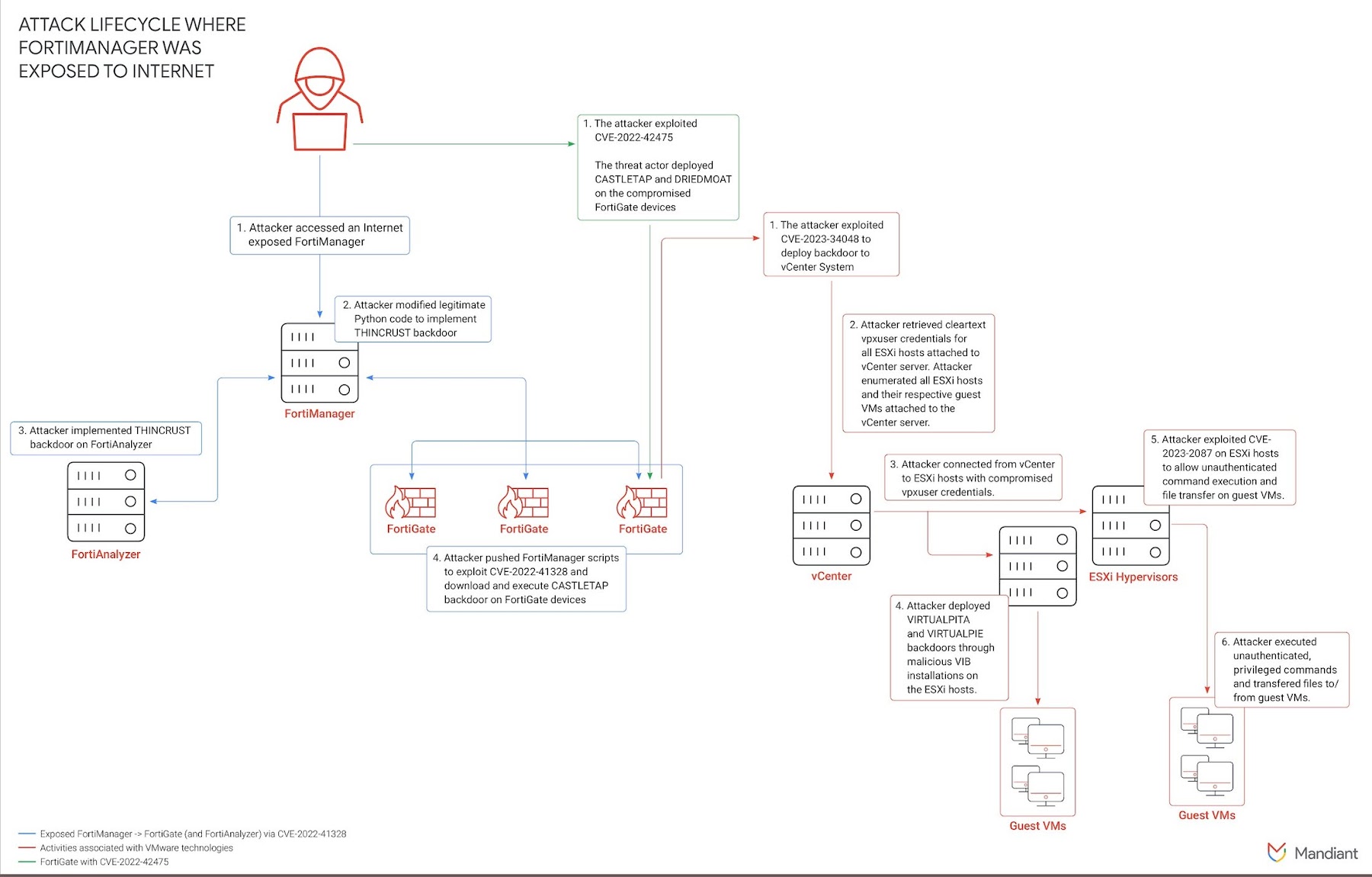
The menace actor in question is UNC3886, which the Google-owned risk intelligence firm branded as “complex, cautious, and evasive.”
Attacks orchestrated by the adversary have leveraged zero-day flaws such as CVE-2022-41328 (Fortinet FortiOS), CVE-2022-22948 (VMware vCenter), and CVE-2023-20867 (VMware Equipment) to complete many destructive actions, ranging from deploying backdoors to acquiring qualifications for deeper entry.

It has also been observed exploiting CVE-2022-42475, one more shortcoming impacting Fortinet FortiGate, shortly just after its general public disclosure by the network security corporation.
These intrusions have generally singled out entities in North America, Southeast Asia, and Oceania, with more victims identified in Europe, Africa, and other elements of Asia. Focused industries span governments, telecommunications, technology, aerospace and defense, and electricity and utility sectors.
A notable tactic in UNC3886’s arsenal is that it developed methods that evade security application and empower it to burrow into govt and business enterprise networks and spy on victims for extended intervals of time with no detection.
This entails the use of publicly offered rootkits like Reptile and Medusa on visitor digital equipment (VMs), the latter of which is deployed applying an installer ingredient dubbed SEAELF.
“Unlike REPTILE, which only presents an interactive entry with rootkit functionalities, MEDUSA displays abilities of logging person credentials from the effective authentications, both locally or remotely, and command executions,” Mandiant pointed out. “These capabilities are advantageous to UNC3886 as their modus operandi to transfer laterally employing legitimate qualifications.”
Also sent on the methods are two backdoors named MOPSLED and RIFLESPINE that acquire advantage of trustworthy services like GitHub and Google Push as command-and-management (C2) channels.
MOPSLED, a probable evolution of the Crosswalk malware, is a shellcode-dependent modular implant that communicates around HTTP to retrieve plugins from a GitHub C2 server, though RIFLESPINE is a cross-platform software that will make use of Google Generate to transfer documents and execute commands.
Mandiant explained it also spotted UNC3886 deploying backdoored SSH shoppers to harvest credentials submit the exploitation of 2023-20867 as properly as leveraging Medusa to set up custom made SSH servers for the very same reason.
“The threat actor’s 1st endeavor to lengthen their access to the network appliances by targeting the TACACS server was the use of LOOKOVER,” it mentioned. “LOOKOVER is a sniffer prepared in C that processes TACACS+ authentication packets, performs decryption, and writes its contents to a specified file path.”

Some of the other malware families sent all through the program of assaults aimed at VMware circumstances are under –
- A trojanized variation of a legit TACACS daemon with credential-logging features
- VIRTUALSHINE, a VMware VMCI sockets-centered backdoor that provides accessibility to a bash shell
- VIRTUALPIE, a Python backdoor that supports file transfer, arbitrary command execution, and reverse shell capabilities
- VIRTUALSPHERE, a controller module liable of a VMCI-dependent backdoor
Over the years, digital devices have become valuable targets for menace actors owing to their popular use in cloud environments.
“A compromised VM can offer attackers with access to not only the knowledge inside the VM occasion but also the permissions assigned to it,” Palo Alto Networks Unit 42 mentioned. “As compute workloads like VMs are commonly ephemeral and immutable, the risk posed by a compromised identification is arguably bigger than that of compromised data in just a VM.”
Organizations are recommended to observe the security tips within just the Fortinet and VMware advisories to protected versus potential threats.
Uncovered this posting exciting? Follow us on Twitter and LinkedIn to examine additional unique content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 New Case Study: Unmanaged GTM Tags Become a Security Nightmare
New Case Study: Unmanaged GTM Tags Become a Security Nightmare