Cybersecurity researchers have uncovered that it is really probable for menace actors to exploit a nicely-known utility named command-not-discovered to advise their have rogue packages and compromise techniques managing Ubuntu running process.
“Though ‘command-not-found’ serves as a convenient instrument for suggesting installations for uninstalled instructions, it can be inadvertently manipulated by attackers by means of the snap repository, foremost to deceptive recommendations of malicious deals,” cloud security agency Aqua explained in a report shared with The Hacker Information.
Installed by default on Ubuntu devices, command-not-found indicates packages to put in in interactive bash sessions when making an attempt to operate instructions that are not offered. The ideas consist of equally the Innovative Packaging Device (APT) and snap offers.
When the resource employs an interior database (“/var/lib/command-not-located/instructions.db”) to propose APT deals, it depends on the “recommend-snap” command to advise snaps that deliver the presented command.

Consequently, should really an attacker be able to match this technique and have their destructive package deal encouraged by the ‘command-not-found’ package deal, it could pave the way for software offer chain assaults.
Aqua reported it found a possible loophole whereby the alias mechanism can be exploited by the menace actor to perhaps register the corresponding snap title involved with an alias and trick people into setting up the malicious bundle.
What is extra, an attacker could assert the snap identify linked to an APT bundle and add a malicious snap, which then ends up getting instructed when a person styles in the command on their terminal.
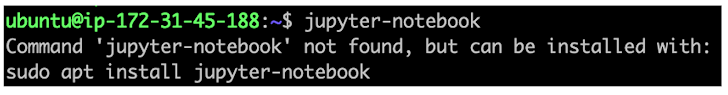
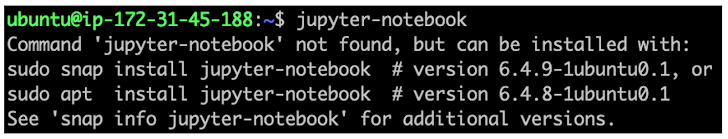
“The maintainers of the ‘jupyter-notebook’ APT package deal had not claimed the corresponding snap title,” Aqua mentioned. “This oversight still left a window of prospect for an attacker to declare it and upload a malicious snap named ‘jupyter-notebook.'”
To make matters worse, command-not-identified utility suggests the snap deal over the legitimate APT bundle for jupyter-notebook, deceptive consumers into setting up the faux snap package.
As quite a few as 26% of the APT bundle instructions are vulnerable to impersonation by destructive actors, Aqua mentioned, presenting a substantial security risk, as they could be registered beneath an attacker’s account.
A third group entails typosquatting attacks in which typographical glitches produced by people (e.g., ifconfigg rather of ifconfig) are leveraged to propose bogus snap offers by registering a fraudulent package with the identify “ifconfigg.”

In such a scenario, command-not-observed “would mistakenly match it to this incorrect command and propose the malicious snap, bypassing the suggestion for ‘net-tools’ entirely,” Aqua scientists stated.
Describing the abuse of the command-not-located utility to suggest counterfeit packages as a pressing worry, the firm is urging customers to verify the resource of a package ahead of set up and verify the maintainers’ trustworthiness.
Builders of APT and snap offers have also been advised to sign-up the associated snap title for their instructions to avert them from being misused.
“It remains unsure how extensively these abilities have been exploited, underscoring the urgency for heightened vigilance and proactive defense tactics,” Aqua said.
Found this post exciting? Abide by us on Twitter and LinkedIn to read through far more exceptional articles we publish.
Some parts of this article are sourced from:
thehackernews.com


 Cybersecurity Tactics FinServ Institutions Can Bank On in 2024
Cybersecurity Tactics FinServ Institutions Can Bank On in 2024