The risk actor recognised as UAC-0050 is leveraging phishing assaults to distribute Remcos RAT employing new methods to evade detection from security software program.
“The group’s weapon of preference is Remcos RAT, a infamous malware for distant surveillance and manage, which has been at the forefront of its espionage arsenal,” Uptycs security researchers Karthickkumar Kathiresan and Shilpesh Trivedi claimed in a Wednesday report.
“However, in their hottest operational twist, the UAC-0050 group has integrated a pipe strategy for interprocess interaction, showcasing their state-of-the-art adaptability.”
UAC-0050, lively considering that 2020, has a heritage of concentrating on Ukrainian and Polish entities by way of social engineering campaigns that impersonate authentic organizations to trick recipients into opening destructive attachments.

In February 2023, the Laptop Unexpected emergency Reaction Group of Ukraine (CERT-UA) attributed the adversary to a phishing marketing campaign designed to deliver Remcos RAT.
Around the earlier handful of months, the similar trojan has been distributed as aspect of at minimum 3 different phishing waves, with a person these kinds of attack also leading to the deployment of an details stealer named Meduza Stealer.
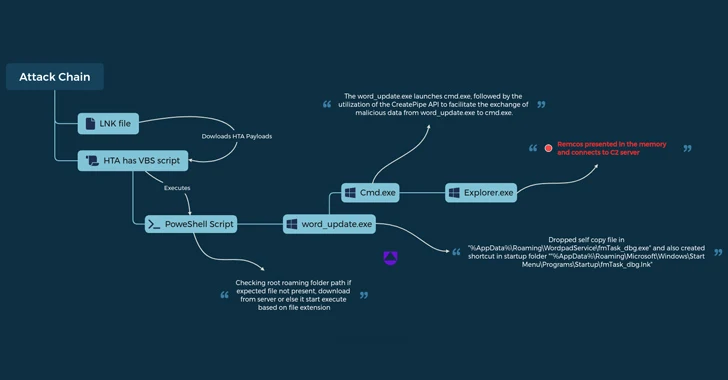
The investigation from Uptycs is based on a LNK file it discovered on December 21, 2023. When the specific initial entry vector is at the moment not known, it is really suspected to have associated phishing e-mails targeting Ukrainian military services personnel that claim to publicize consultancy roles with the Israel Defense Forces (IDF).

The LNK file in issue collects details regarding antivirus products and solutions mounted on the concentrate on computer, and then proceeds to retrieve and execute an HTML software named “6.hta” from a remote server employing mshta.exe, a Windows-indigenous binary for managing HTA documents.
This move paves the way for a PowerShell script that unpacks another PowerShell script to down load two data files identified as “phrase_update.exe” and “ofer.docx” from the area new-tech-savvy[.]com.
Jogging term_update.exe triggers it to develop a duplicate of by itself with the identify fmTask_dbg.exe and create persistence by producing a shortcut to the new executable in the Windows Startup folder.

The binary also employs unnamed pipes to facilitate the trade of facts involving itself and a recently spawned baby approach for cmd.exe in purchase to in the end decrypt and launch the Remcos RAT (variation 4.9.2 Pro), which is capable of harvesting procedure information and cookies and login information from web browsers like Internet Explorer, Mozilla Firefox, and Google Chrome.
“Leveraging pipes in just the Windows operating technique presents a covert channel for info transfer, skillfully evading detection by Endpoint Detection and Reaction (EDR) and antivirus units,” the researchers claimed.
“Although not totally new, this system marks a important leap in the sophistication of the group’s approaches.”
Uncovered this short article fascinating? Comply with us on Twitter and LinkedIn to examine a lot more exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Mandiant’s Twitter Account Restored After Six-Hour Crypto Scam Hack
Mandiant’s Twitter Account Restored After Six-Hour Crypto Scam Hack