The U.S. Division of the Treasury imposed sanctions versus a Russian female for having element in the laundering of virtual forex for the country’s elites and cybercriminal crews, like the Ryuk ransomware team.
Ekaterina Zhdanova, for each the section, is reported to have facilitated substantial cross border transactions to support Russian men and women to gain access to Western financial marketplaces and circumvent global sanctions.
“Zhdanova makes use of entities that absence Anti-Funds Laundering/Combatting the Financing of Terrorism (AML/CFT) controls, these types of as OFAC-designated Russian cryptocurrency trade Garantex Europe OU (Garantex),” the treasury division explained final week.
“Zhdanova depends on various strategies of price transfer to shift cash internationally. This consists of the use of funds and leveraging connections to other intercontinental money laundering associates and organizations.”
It is really value noting that Garantex was formerly sanctioned by the U.S. in April 2022, coinciding with the takedown of the dark web market known as Hydra.
Zhdanova has also been accused of featuring products and services to men and women linked with the Russian Ryuk ransomware team, laundering around $2.3 million of suspected victim payments on behalf of a Ryuk ransomware affiliate in 2021.
Ryuk, a predecessor to the Conti ransomware, initial emerged on the threat landscape in 2018, and has compromised governments, academia, healthcare, manufacturing, and technology corporations worldwide.

Before this February, a 30-yr-old Russian citizen named Denis Mihaqlovic Dubnikov pleaded guilty in the U.S. to money laundering prices and for making an attempt to conceal the supply of resources acquired in relationship with Ryuk ransomware attacks.
Ransomware Continues to Evolve
The growth comes as a record 514 ransomware victims had been claimed for the thirty day period of September 2023, registering a 153% raise 12 months-in excess of-yr, and up from 502 in July and 390 in August.
Almost 100 of people assaults have been attributed to nascent teams like LostTrust and RansomedVC. Some of the other new entrants noticed in current months contain Dark Angels, Knight, Funds Information, and Very good Working day.
“The file ranges of ransomware attacks are partially the final result of the emergence of new danger actors which includes RansomedVC,” NCC Team mentioned late past month.
“RansomedVC operates as ‘penetration testers.’ Nonetheless, its solution to extortion also incorporates the claim that any vulnerabilities found in their targets’ network will be noted in compliance with Europe’s Typical Knowledge Protection Regulation (GDPR).
The influx of new groups demonstrates the evolving ransomware landscape, even as more recognized threat actors continue on to adapt and refine their ways and tactics to dodge security controls.
Very last thirty day period, Palo Alto Networks Device 42 reported BlackCat’s addition of a utility codenamed Munchkin to its arsenal in order to propagate the ransomware payload to distant machines and shares on a sufferer group network.
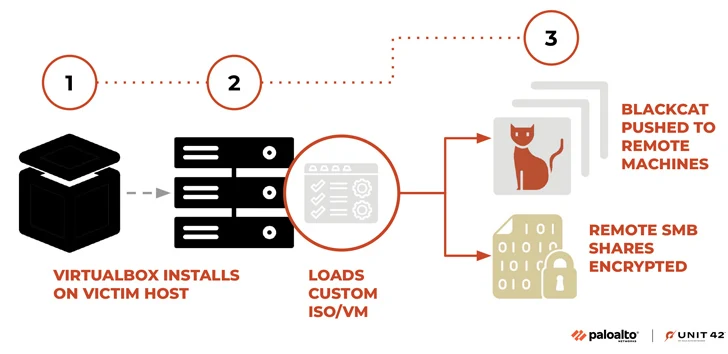
“This tooling provided a Linux-centered running process (OS) functioning Sphynx,” Unit 42 researchers stated. “Menace operators can use this utility to run BlackCat on remote machines, or to deploy it to encrypt distant Server Message Block (SMB)/Frequent Internet File Shares (CIFS).”

The diversification of ransomware is evidenced by the actuality that hacktivist collectives this sort of as GhostSec – which is part of The 5 Households – have entered the fray, releasing a custom locker named GhostLocker for economical gain.
“Even if GhostLocker is not successful in the [ransomware-as-a-service] sector, it appears evident that it is a turning place as a model,” SOCRadar claimed. “The fact that it is fairly minimal-priced, is effective with a very minimal proportion foundation, and is available to virtually every person can enhance ransomware assaults to extreme stages.”
Cybersecurity organization Uptycs, in its very own examination of GhostSec and GhostLocker, explained the go as a “surprising departure from their past actions and stated agenda,” provided the collective’s background of focusing on Israeli entities in assistance of Palestine.
The spike in ransomware attacks has also prompted an alliance of 50 international locations, referred to as the International Counter Ransomware Initiative, pledged never ever to fork out ransom demands in a bid to discourage fiscally determined actors and ransomware gangs from profiting off these types of schemes.
“To protect against ransomware, it is vital to undertake a comprehensive protection method,” Uptycs claimed. “This approach need to encompass resilient backup methods, successful security application, person schooling, and a proactive incident reaction plan.”
Located this report attention-grabbing? Stick to us on Twitter and LinkedIn to read through additional distinctive written content we post.
Some parts of this article are sourced from:
thehackernews.com


 StripedFly Malware Operated Unnoticed for 5 Years, Infecting 1 Million Devices
StripedFly Malware Operated Unnoticed for 5 Years, Infecting 1 Million Devices