A chain of two critical flaws has been disclosed in Alibaba Cloud’s ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections and access sensitive knowledge belonging to other customers.
“The vulnerabilities most likely authorized unauthorized obtain to Alibaba Cloud customers’ PostgreSQL databases and the capacity to conduct a source chain attack on each Alibaba database expert services, leading to an RCE on Alibaba database solutions,” cloud security agency Wiz explained in a new report shared with The Hacker News.
The issues, dubbed BrokenSesame, were claimed to Alibaba Cloud in December 2022, adhering to mitigations were being deployed by the corporation on April 12, 2023. There is no evidence to propose that the weaknesses were being exploited in the wild.
In a nutshell, the vulnerabilities – a privilege escalation flaw in AnalyticDB and a remote code execution bug in ApsaraDB RDS – produced it probable to elevate privileges to root inside of the container, escape to the fundamental Kubernetes node, and in the long run receive unauthorized accessibility to the API server.
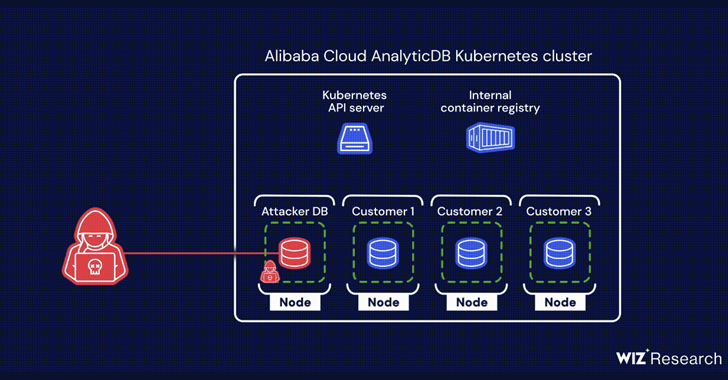
Armed with this functionality, an attacker could retrieve qualifications connected with the container registry from the API server and force a destructive image to attain control of buyer databases belonging to other tenants on the shared node.
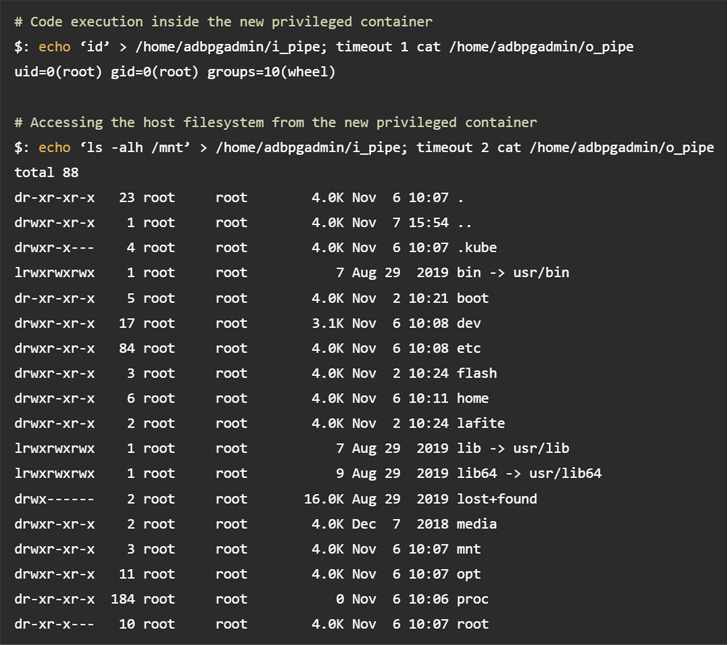
“The credentials utilised to pull illustrations or photos ended up not scoped correctly and permitted thrust permissions, laying the basis for a offer-chain attack,” Wiz researchers Ronen Shustin and Shir Tamari stated.
This is not the initially time PostgreSQL vulnerabilities have been identified in cloud providers. Very last yr, Wiz uncovered similar issues in Azure Databases for PostgreSQL Adaptable Server (ExtraReplica) and IBM Cloud Databases for PostgreSQL (Hell’s Keychain).
Upcoming WEBINARDefend with Deception: Advancing Zero Rely on Security
Learn how Deception can detect sophisticated threats, quit lateral motion, and increase your Zero Believe in tactic. Be part of our insightful webinar!
Help you save My Seat!
The conclusions arrive as Palo Alto Networks Unit 42, in its Cloud Danger Report, uncovered that “risk actors have develop into adept at exploiting common, day to day issues in the cloud,” which includes misconfigurations, weak credentials, absence of authentication, unpatched vulnerabilities and destructive open up supply application (OSS) packages.
“76% of businesses really don’t implement MFA [multi-factor authentication] for console customers, when 58% of businesses really don’t enforce MFA for root/admin customers,” the cybersecurity business stated.
Uncovered this report intriguing? Comply with us on Twitter and LinkedIn to read through extra distinctive written content we article.
Some parts of this article are sourced from:
thehackernews.com

 Small Business Interest in Cyber-Hygiene is Waning
Small Business Interest in Cyber-Hygiene is Waning