The defense sector in Ukraine and Japanese Europe has been targeted by a novel .NET-primarily based backdoor called DeliveryCheck (aka CAPIBAR or GAMEDAY) that is capable of providing subsequent-phase payloads.
The Microsoft risk intelligence workforce, in collaboration with the Personal computer Crisis Response Crew of Ukraine (CERT-UA), attributed the assaults to a Russian country-condition actor acknowledged as Turla, which is also tracked below the names Iron Hunter, Mystery Blizzard (formerly Krypton), Uroburos, Venomous Bear, and Waterbug. It’s connected to Russia’s Federal Security Support (FSB).
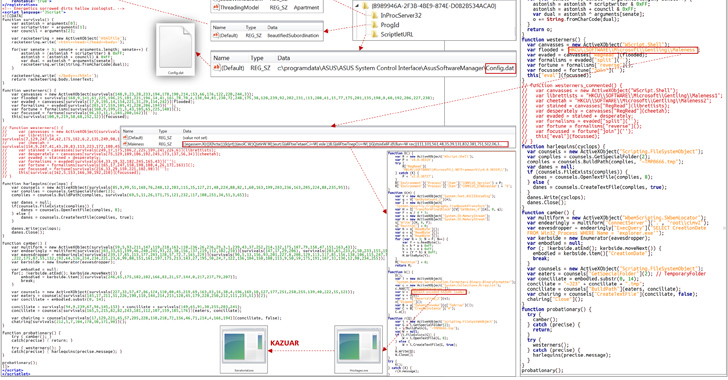
“DeliveryCheck is dispersed by using email as documents with malicious macros,” the company reported in a sequence of tweets. “It persists by using a scheduled process that downloads and launches it in memory. It also contacts a C2 server to retrieve duties, which can include things like the start of arbitrary payloads embedded in XSLT stylesheets.”
Profitable original entry is also accompanied in some conditions by the distribution of a known Turla implant dubbed Kazuar, which is equipped to steal software configuration information, function logs, and a wide array of info from web browsers.
The final target of the assaults is to exfiltrate messages from the Sign messaging application for Windows, enabling the adversary to access delicate conversations, documents, and illustrations or photos on qualified techniques.
A noteworthy component of DeliveryCheck is its potential to breach Microsoft Exchange servers to install a server-aspect element making use of PowerShell Wished-for Condition Configuration (DSC), a PowerShell administration platform that can help administrators to automate the configuration of Windows programs.
“DSC generates a Managed Item Format (MOF) file containing a PowerShell script that hundreds the embedded .NET payload into memory, correctly turning a respectable server into a malware C2 middle,” Microsoft stated.
Forthcoming WEBINARShield In opposition to Insider Threats: Grasp SaaS Security Posture Administration
Concerned about insider threats? We have got you protected! Join this webinar to discover practical tactics and the insider secrets of proactive security with SaaS Security Posture Management.
Sign up for Currently
The disclosure comes as the Cyber Police of Ukraine dismantled a substantial bot farm with more than 100 people allegedly spreading hostile propaganda justifying the Russian invasion, leaking personalized data belonging to Ukrainian citizens, and partaking in many fraud schemes.
As portion of the operation, queries were carried out in 21 locations, top to the seizure of computer system machines, cellular telephones, more than 250 GSM gateways, and about 150,000 SIM cards belonging to diverse cellular operators.
Uncovered this posting exciting? Abide by us on Twitter and LinkedIn to browse a lot more exclusive written content we put up.
Some parts of this article are sourced from:
thehackernews.com

 New P2PInfect Worm Targeting Redis Servers on Linux and Windows Systems
New P2PInfect Worm Targeting Redis Servers on Linux and Windows Systems