An unnamed European Ministry of Foreign Affairs (MFA) and its a few diplomatic missions in the Middle East were focused by two beforehand undocumented backdoors tracked as LunarWeb and LunarMail.
ESET, which recognized the activity, attributed it with medium assurance to the Russia-aligned cyberespionage team Turla (aka Iron Hunter, Pensive Ursa, Magic formula Blizzard, Snake, Uroburos, and Venomous Bear), citing tactical overlaps with prior strategies recognized as orchestrated by the group.
“LunarWeb, deployed on servers, makes use of HTTP(S) for its C&C [command-and-control] communications and mimics reputable requests, although LunarMail, deployed on workstations, is persisted as an Outlook include-in and makes use of email messages for its C&C communications,” security researcher Filip Jurčacko said.
An evaluation of the Lunar artifacts demonstrates that they may perhaps have been utilized in targeted attacks considering the fact that early 2020, or even before.
Turla, assessed to be affiliated with Russia’s Federal Security Service (FSB), is an superior persistent menace (APT) that is regarded to be active considering that at least 1996. It has a monitor document of concentrating on a vary of industries spanning federal government, embassies, military services, training, analysis, and pharmaceutical sectors.

Before this yr, the cyber espionage group was uncovered attacking Polish corporations to distribute a backdoor named TinyTurla-NG (TTNG).
“The Turla group is a persistent adversary with a prolonged history of pursuits,” Craze Micro noted in an examination of the danger actor’s evolving toolset. “Their origins, strategies, and targets all suggest a nicely-funded procedure with really experienced operatives.”
The actual intrusion vector applied to breach the MFA is presently unidentified, despite the fact that it’s suspected that it might have included an element of spear-phishing and the exploitation of misconfigured Zabbix application.
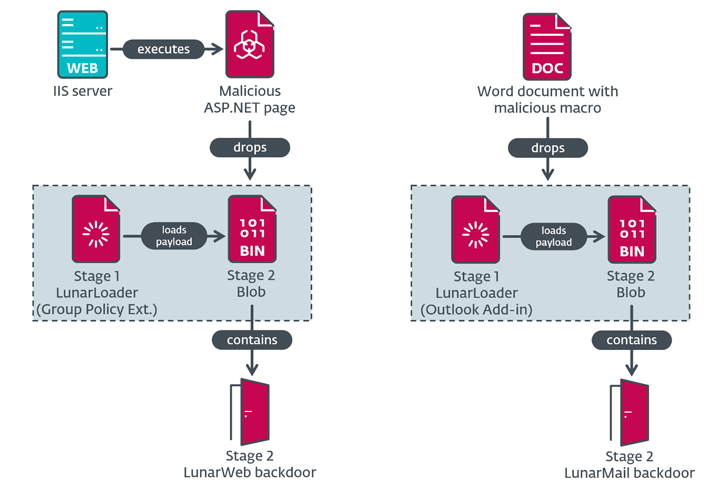
The commencing level of the attack chain pieced with each other by ESET commences with a compiled version of an ASP.NET web web page that’s made use of as a conduit to decode two embedded blobs, which includes a loader, codenamed LunarLoader, and the LunarWeb backdoor.
Exclusively, when the webpage is requested, it expects a password in a cookie named SMSKey that, if provided, is applied to derive a cryptographic essential for decrypting the up coming-phase payloads.
“The attacker by now had network access, applied stolen qualifications for lateral motion, and took watchful techniques to compromise the server devoid of raising suspicion,” Jurčacko pointed out.
LunarMail, on the other hand, is propagated through a destructive Microsoft Phrase document sent by using a spear-phishing email, which, in transform, packs LunarLoader and the backdoor.
LunarWeb is outfitted to assemble system information and parse instructions inside JPG and GIF impression data files despatched from the C&C server, subsequent which the benefits are exfiltrated again in a compressed and encrypted structure. It more makes an attempt to blend in by masquerading its network targeted traffic as authentic-searching (e.g., Windows update).

The C&C recommendations allow the backdoor to run shell and PowerShell commands, execute Lua code, examine/publish information, and archive specified paths. The next implant, LunarMail, supports related capabilities, but notably piggybacks on Outlook and makes use of email for interaction with its C&C server by hunting for sure messaging with PNG attachments.
Some of the other instructions particular to LunarMail contain the ability to set an Outlook profile to use for C&C, develop arbitrary procedures, and acquire screenshots. The execution outputs are then embedded in a PNG image or PDF document prior to exfiltrating them as attachments in e-mail to an attacker-managed inbox.
“This backdoor is built to be deployed on user workstations, not servers — due to the fact it is persisted and meant to operate as an Outlook incorporate-in,” Jurčacko mentioned. “LunarMail shares ideas of its operation with LightNeuron, yet another Turla backdoor that employs email messages for C&C uses.”
Found this report fascinating? Stick to us on Twitter and LinkedIn to read through extra exceptional written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 (Cyber) Risk = Probability of Occurrence x Damage
(Cyber) Risk = Probability of Occurrence x Damage