Inadequately secured Microsoft SQL (MS SQL) servers are becoming qualified in the U.S., European Union, and Latin American (LATAM) locations as section of an ongoing monetarily inspired marketing campaign to achieve preliminary obtain.
“The analyzed danger marketing campaign seems to conclusion in 1 of two methods, possibly the advertising of ‘access’ to the compromised host, or the ultimate supply of ransomware payloads,” Securonix scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov claimed in a complex report shared with The Hacker Information.
The campaign, joined to actors of Turkish origin, has been codenamed RE#TURGENCE by the cybersecurity firm.

Original obtain to the servers entails conducting brute-force attacks, followed by the use of xp_cmdshell configuration option to operate shell commands on the compromised host. This exercise mirrors that of a prior campaign dubbed DB#JAMMER that arrived to light-weight in September 2023.
This stage paves the way for the retrieval of a PowerShell script from a remote server that is accountable for fetching an obfuscated Cobalt Strike beacon payload.
The article-exploitation toolkit is then utilised to down load the AnyDesk remote desktop application from a mounted network share for accessing the machine and downloading supplemental instruments these as Mimikatz to harvest qualifications and Highly developed Port Scanner to have out reconnaissance.
Lateral movement is attained by usually means of a authentic method administration utility identified as PsExec, which can execute systems on distant Windows hosts.
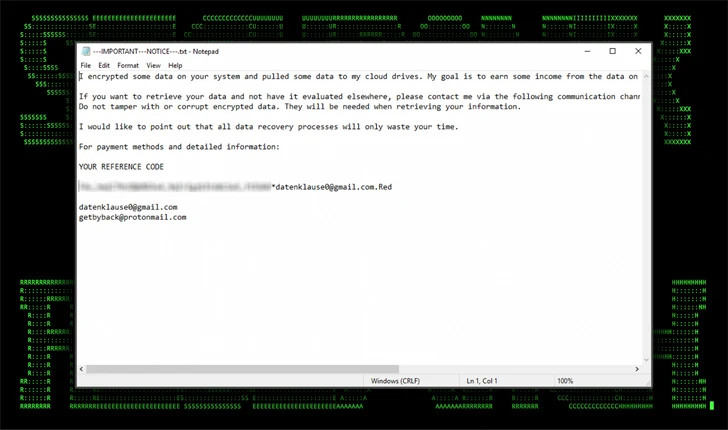
That attack chain, in the end, culminates with the deployment of Mimic ransomware, a variant of which was also utilised in the DB#JAMMER campaign.
“The indicators as well as destructive TTPs applied in the two strategies are wholly various, so there is a pretty higher opportunity these are two disparate campaigns,” Kolesnikov told The Hacker Information.

“More specially, even though the original infiltration procedures are comparable, DB#JAMMER was a little bit more subtle and employed tunneling. RE#TURGENCE is more specific and tends to use reputable tools and remote monitoring and administration, such as AnyDesk, in an attempt to blend in with regular exercise.”
Securonix mentioned it uncovered an operational security (OPSEC) blunder built by the danger actors that permitted it to keep an eye on clipboard action owing to the reality that the clipboard sharing function of AnyDesk was enabled.
This produced it attainable to glean their Turkish origins and their on the web alias atseverse, which also corresponds to a profile on Steam and a Turkish hacking forum identified as SpyHack.
“Always refrain from exposing critical servers immediately to the internet,” the researchers cautioned. “With the circumstance of RE#TURGENCE attackers had been instantly able to brute power their way into the server from outside the principal network.”
Uncovered this report appealing? Abide by us on Twitter and LinkedIn to browse far more unique content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Why Public Links Expose Your SaaS Attack Surface
Why Public Links Expose Your SaaS Attack Surface