A new malvertising campaign has been observed capitalizing on a compromised internet site to boost spurious variations of PyCharm on Google lookup final results by leveraging Dynamic Research Ads.
“Unbeknownst to the web page operator, 1 of their advertisements was automatically designed to advertise a popular system for Python builders, and obvious to folks accomplishing a Google lookup for it,” Jérôme Segura, director of threat intelligence at Malwarebytes, mentioned in a report.
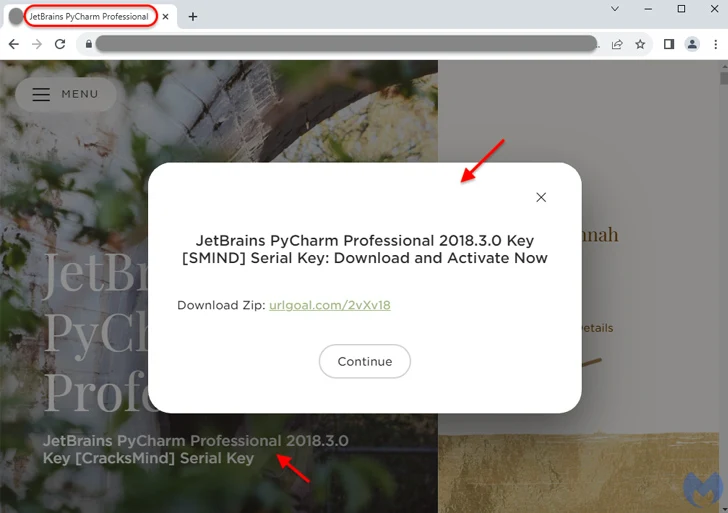
“Victims who clicked on the advert ended up taken to a hacked web web page with a hyperlink to download the application, which turned out to put in over a dozen distinct pieces of malware alternatively.”

The infected website in concern is an unnamed on the web portal that specializes in wedding day setting up, which experienced been injected with malware to serve bogus inbound links to the PyCharm application.
Per Malwarebytes, targets are directed to the website utilizing Dynamic Lookup Advertisements, an advert featuring from Google that programmatically works by using the site’s written content to tailor targeted ads based on the look for terms.
“When another person queries on Google with terms carefully associated to the titles and usually applied phrases on your site, Google Ads will use these titles and phrases to find a landing web page from your site and produce a very clear, pertinent headline for your ad,” Google points out in its help documentation.
As a end result, a danger actor with abilities to change the website’s material could also make the ad strategies a lucrative device for abuse, effectively serving Google Lookup people advertisements that can final result in unintended behavior.

“What took place below is Google Ads dynamically generated this advert from the hacked web page, which would make the web page operator an unintentional middleman and victim spending for their individual malicious ad,” Segura spelled out.
The development will come as Akamai detailed the infrastructure behind a subtle phishing campaign focusing on hospitality web sites and their buyers.
“The campaign is a world danger, with a notable quantity of DNS site visitors observed in Switzerland, Hong Kong, and Canada,” the corporation stated.
“Though the campaign was initially considered to have been active only since September 2023, the domain registration shows area names being registered and queried as early as June 2023.”
Identified this post exciting? Adhere to us on Twitter and LinkedIn to browse more unique content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Canada Bans WeChat and Kaspersky Apps On Government Devices
Canada Bans WeChat and Kaspersky Apps On Government Devices