Above the earlier few decades, SaaS has made into the spine of company IT. Assistance firms, these kinds of as health care practices, legislation corporations, and fiscal solutions corporations, are practically entirely SaaS based mostly. Non-company firms, which include companies and shops, have about 70% of their computer software in the cloud.
These purposes comprise a prosperity of data, from minimally delicate typical corporate data to extremely delicate intellectual residence, customer data, and employee facts. Threat actors have noted this change, and are actively performing to breach applications to accessibility the information.
In this article are the top rated trends influencing the state of SaaS Security for 2024 — and what you can do about it.
Democratization of SaaS
SaaS apps have remodeled the way companies buy and use program. Organization units purchase and onboard the SaaS resources that most effective suit their wants. Whilst this is empowering for enterprise models that have prolonged been frustrated by delays in procuring and onboarding application, it does require corporations to rethink the way they secure knowledge.
Security groups are becoming pressured to create new methods to safe corporation information. Lacking obtain and visibility into an application, they are positioned in the job of advising a company device that is making use of SaaS apps. To even more complicate matters, every SaaS software has distinctive settings and makes use of various terminology to explain security functions. Security groups can’t create a a person-dimension-matches-all direction doc simply because of the differences among the applications.
Security groups ought to come across new strategies to collaborate with small business units. They require a software that delivers visibility and steerage for every single software location so that they – and the business device – realize the pitfalls and ramifications associated in the configuration selections that they make.
ITDR Varieties a Critical Safety Net
If a menace actor gains accessibility to a higher-privilege account, they attain unfettered accessibility within just the software. Organizations are now comprehension that identification is the de facto perimeter for their SaaS purposes.
When threat actors acquire more than an authorized user account, they ordinarily follow frequent tactics, tactics and techniques (TTP) as they work their way via the app towards the info they want. They go away powering indicators of compromise (IoC), which might be dependent on actions taken in the application or logs.
As we shift into the new year, we are going to see additional businesses adopting an Identification Risk Detection & Reaction (ITDR) tactic. ITDR mitigates that issue. As a critical component in Identification Security Posture Administration, ITDR abilities can detect TTPs and IoCs, and then mail an notify to the incident reaction team. Through ITDR, menace actors who have managed to breach the id perimeter can nonetheless be stopped prior to they steal critical info or insert ransomware into the application.
Learn about how ITDR can help you cope with these SaaS Security trends these days
Cross-Border Compliance Indicates Much more Tenants to Protected
Worldwide companies are more and more facing diverse regulatory specifications from just one country to the up coming. As a end result, 2024 will see an maximize in the number of geo-precise tenants as aspect of the effort to preserve details segmented in accordance with the distinctive rules.
This alter will have a constrained impact on software charges as most SaaS application pricing is primarily based on subscribers instead than tenants. On the other hand, it will have a substantial impression on security. Each individual tenant will will need to be configured independently, and just mainly because a single instance of the application is safe won’t necessarily mean that all tenants are protected.
To safe all these tenants, security teams must look for a security option that enables them to established application benchmarks, compare tenants, and screen security configurations facet-by-side without having charging further for each added tenant. By implementing ideal procedures all over the firm, providers can maintain all their tenants protected.
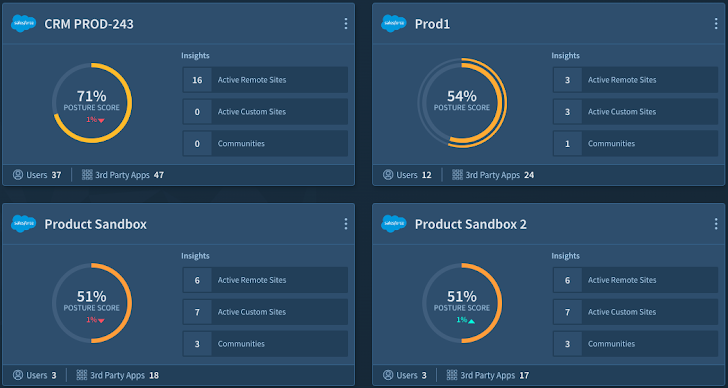 Figure 1: Adaptive Shield’s platform monitoring and presenting all Salesforce tenants
Figure 1: Adaptive Shield’s platform monitoring and presenting all Salesforce tenants
Misconfigured Configurations Are Top to New Exploits
A default misconfiguration in ServiceNow induced popular stress in Oct. The environment, which was element of the application’s Entry Management Lists, authorized unauthorized consumers to extract knowledge from documents. The misconfiguration impacted countless numbers of companies. A comparable misconfiguration in Salesforce Group back again in Might also impacted a significant quantity of businesses and led to info breaches.
Misconfigurations like these have the prospective to result in big hurt to organizations. They guide to info leaks that break the belief between companies and their stakeholders, and have the opportunity to convert into onerous fines, based on the nature of the facts that leaked.
Securing misconfigurations is an organization’s very best likelihood at blocking these exploits from impacting their functions and hurting their bottom lines.
See how to automate SaaS misconfigurations and regain management of your SaaS stack
Increased Reliance on 3rd-Party Applications Adds to SaaS Risk
Third-get together purposes insert real value for finish users. They enhance procedures, increase performance, and link information involving multiple applications. Buyers hook up these SaaS apps with the click on of button, and instantaneously begin strengthening their workflows.
In March 2023, Adaptive Protect produced a report displaying that businesses making use of Google Office with 10,000-20,000 users averaged 13,913 3rd-get together apps related to Google Workplace by yourself. An astonishing 89% of these asked for both large- or medium-risk permissions. Numerous of these high-risk apps are employed after and forgotten about, or utilised by a tiny selection of employees. However, even these dormant or lightly utilized programs have significant permissions and can be utilized to compromise or breach a SaaS application.
The use of 3rd-social gathering apps is only escalating, as extra applications are made and employees use their possess judgment – relatively than checking with their security team – when integrating third-get together applications into their stack. Security groups have to establish visibility into all their integrated applications, and gain insights into the permissions asked for, the value the application contributes to the firm, and the risk it poses.
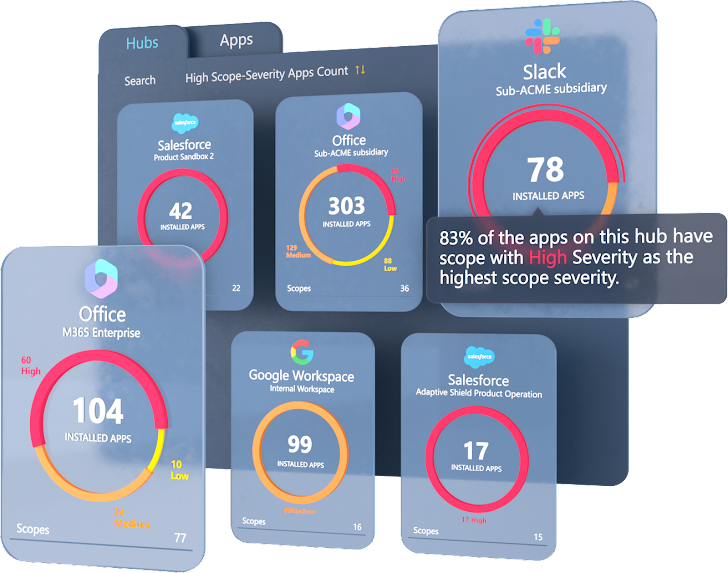 Figure 2: Adaptive Shield’s system demonstrates integrated 3rd-get together applications, their risk score, and the scopes granted
Figure 2: Adaptive Shield’s system demonstrates integrated 3rd-get together applications, their risk score, and the scopes granted
Numerous Products to Secure as Operating from Dwelling Just isn’t Likely Any place
In 2023, virtually 40% of all staff labored from property at least section of the time. In accordance to WFHResearch, around 12% of workforce work completely in their households, while one more 28% have hybrid roles.
These figures need to give pause to security personnel involved about end users logging in to their function accounts from private gadgets. A person of the most significant fears security groups have is when significant-privileged users log into their accounts employing an unmanaged or unsecured machine. These equipment may have critical vulnerabilities, and create a new attack vector. For quite a few teams, there is pretty much no way to notify which devices are used to entry the SaaS app or see no matter whether individuals products are safe.
Organizations Are Turning to SSPM to Safe SaaS
While all these developments point to reputable SaaS security concerns, SaaS Security Posture Administration (SSPM) resources coupled with ITDR abilities, like Adaptive Protect, can completely protected the SaaS stack. SSPMs are created to instantly monitor configurations, wanting for configuration drifts that weaken an app’s posture. In SaaS Security Survey, 2024 Plans & Priorities by Cloud Security Affiliation and Adaptive Shield, 71% of respondents claimed their firm had amplified their financial commitment into SaaS security tools about the previous year, and 80% ended up either already suing SSPM or prepared to devote in a single inside of the subsequent 18 months.
SSPMs can provide baselining resources for various tenants of the exact app, and help buyers to establish finest tactics, examine settings from distinct situations, and improve the all round posture of the SaaS stack.
SSPMs also detect and keep an eye on 3rd-party purposes, alerting buyers if their built-in apps are requesting also substantially access and updating the security group when built-in applications are dormant. It tracks end users, and monitors the gadgets becoming employed to accessibility apps to avert the use of unmanaged or unsecured products on company SaaS applications. Moreover, their developed-in communication resources make it uncomplicated for enterprise units to collaborate with security staff in securing their apps.
SaaS apps have developed in acceptance for great reason. They permit businesses to scale as desired, subscribe to the applications they need at the minute, and restrict expenditure in some IT. With SSPM, these applications can be secured as nicely.
See are living in a ten-minute demo how you can start securing your SaaS stack
Observed this report interesting? Adhere to us on Twitter and LinkedIn to read more special material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Rhadamanthys Malware: Swiss Army Knife of Information Stealers Emerges
Rhadamanthys Malware: Swiss Army Knife of Information Stealers Emerges