Mexican consumers have been focused with tax-themed phishing lures at minimum since November 2023 to distribute a beforehand undocumented Windows malware referred to as TimbreStealer.
Cisco Talos, which identified the action, explained the authors as expert and that the “threat actor has earlier used related techniques, approaches and procedures (TTPs) to distribute a banking trojan known as Mispadu in September 2023.
Other than using refined obfuscation methods to sidestep detection and make sure persistence, the phishing marketing campaign would make use of geofencing to one out buyers in Mexico, returning an innocuous blank PDF file rather of the malicious one if the payload websites are contacted from other spots.
Some of the noteworthy evasive maneuvers consist of leveraging custom made loaders and direct system calls to bypass common API monitoring, in addition to utilizing Heaven’s Gate to execute 64-bit code within a 32-bit course of action, an method that was also not long ago adopted by HijackLoader.

The malware will come with various embedded modules for orchestration, decryption, and security of the key binary, while also jogging a series of checks to identify if it’s running a sandbox surroundings, the technique language is not Russian, and the timezone is in a Latin American area.
The orchestrator module also seems to be for files and registry keys to double-check that the device hasn’t been earlier infected, in advance of launching a payload installer component that displays a benign decoy file to the consumer, as it in the long run triggers the execution of TimbreStealer’s major payload.
The payload is created to harvest a extensive variety of info, such as credential data from various folders, technique metadata, and the URLs accessed, seem for documents matching precise extensions, and verify the presence of distant desktop software package.
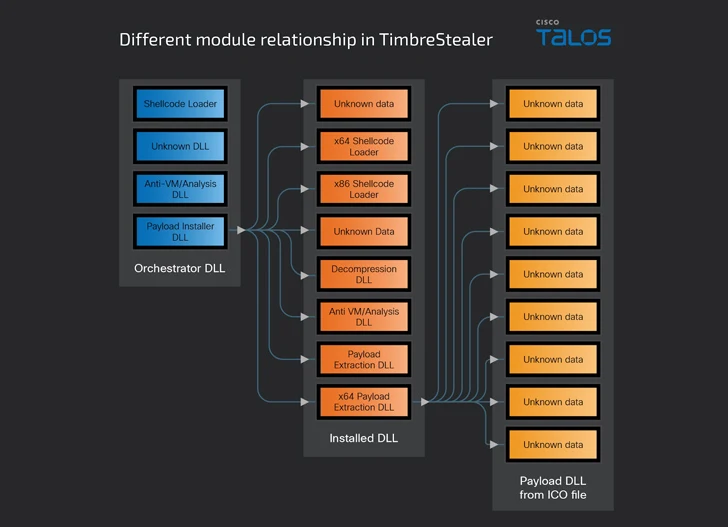
Cisco Talos reported it discovered overlaps with a Mispadu spam marketing campaign observed in September 2023, whilst the goal industries of TimbreStealer are various and with a concentrate on production and transportation sectors.
The disclosure arrives amid the emergence of a new edition of an additional information and facts stealer referred to as Atomic (aka AMOS), which is able of gathering information from Apple macOS systems these kinds of as area person account passwords, credentials from Mozilla Firefox and Chromium-centered browsers, crypto wallet information and facts, and information of fascination, working with an abnormal blend of Python and Apple Script code.

“The new variant drops and makes use of a Python script to keep covert,” Bitdefender researcher Andrei Lapusneanu mentioned, noting the Apple Script block for collecting delicate information from the victim’s computer system reveals a “considerably superior stage of similarity” with the RustDoor backdoor.
It also follows the emergence of new stealer malware people these kinds of as XSSLite, which was unveiled as section of a malware enhancement levels of competition hosted by the XSS forum, even as present strains like Agent Tesla and Pony (aka Fareit or Siplog) continued to be utilized for data theft and subsequent sale on stealer logs marketplaces like Exodus.
Identified this report intriguing? Stick to us on Twitter and LinkedIn to examine much more unique content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Cybersecurity Agencies Warn Ubiquiti EdgeRouter Users of APT28’s MooBot Threat
Cybersecurity Agencies Warn Ubiquiti EdgeRouter Users of APT28’s MooBot Threat