Wing Security not too long ago introduced that essential third-celebration risk evaluation is now readily available as a absolutely free solution. But it raises the issues of how SaaS is linked to 3rd-party risk administration (TPRM) and what businesses ought to do to make sure a correct SaaS-TPRM procedure is in position. In this posting we will share 5 tips to control the 3rd-party risks linked with SaaS, but 1st…
What specifically is Third-Get together Risk Management in SaaS?
SaaS is speedily growing, providing corporations convenience, swift implementations, and useful chances. On the other hand, this advancement introduces a security obstacle where by pitfalls occur from the interconnected mother nature of SaaS supply chains. It is distinct that prior to onboarding a new contractor or seller, we require owing diligence, security checks, and referrals. On the other hand, we now recognize that in the SaaS area, applications are, in point, the go-to seller of option.
Let’s reveal: Any staff can very conveniently join SaaS distributors to organization data, granting them permissions and accessibility. This effortless onboarding is essential for performance, scalability, and finding function performed. But it also introduces a lot of security issues due to the fact most SaaS applications, in contrast to traditional distributors, usually bypass or skip security or IT acceptance.
3rd-social gathering SaaS security solutions engage in a pivotal part in safeguarding an organization’s SaaS offer chain, and evaluating SaaS sellers turns into a essential component of in depth vendor risk management. When some of the duty for security falls on the SaaS seller, organizations ought to keep vigilant in controlling third-occasion challenges, irrespective of their measurement, to uphold a safe and sturdy organization setting and to assure they comply with sector expectations.
In straightforward conditions, Third-Social gathering Risk Management in the context of SaaS is the course of action of analyzing and managing the possible pitfalls posed by 3rd-celebration suppliers and company suppliers in the SaaS domain. TPRM helps security and IT teams recognize and have an understanding of many varieties of threats coming by 3rd-celebration services that relate to cybersecurity, like information privacy vulnerabilities, compliance gaps, operational issues, fiscal difficulties, and reputational fears.
Five TPRM guidelines to assure SaaS Security
1. Identification and Categorization:
Identifying and categorizing 3rd-bash connections is a critical action for companies to recognize the prospective threats these connections pose to security and compliance. A absence of systematic knowledge selection and assessment on entry stages and vendor security can leave security and IT groups in the dark, hindering their ability to evaluate and safely and securely use distinct third-social gathering apps appropriately.
Nonetheless, with SaaS Security Posture Administration (SSPM) technology, corporations can conquer this obstacle by easily discovering all their third-occasion SaaS purposes. SSPM methods offer contextual details on the level of entry these apps have to organizational belongings and details about the vendor’s security level dependent on ongoing examination.
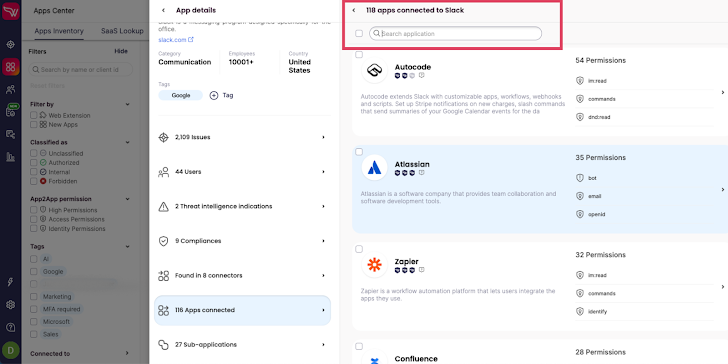 Wing Security’s TPRM option for SaaS purposes
Wing Security’s TPRM option for SaaS purposes
2. Thanks Diligence and Assessment:
Conducting because of diligence prior to onboarding programs is an critical phase in ensuring that risky apps are not getting introduced into an organization’s SaaS Stack. This maximizes the want to evaluate 3rd-occasion security controls, policies, and methods, making sure they fulfill the necessary benchmarks forward of onboarding them.
To deal with this trouble, corporations ought to search for a resolution that can offer the needed security and compliance details about pertinent SaaS distributors/apps. Information and facts these as security compliances, privacy compliances, seller dimension, spot, historic menace intelligence alerts concerning breaches or security incidents that the seller experienced seasoned, and so forth. This information is a main component of the thanks diligence system of third-celebration distributors.
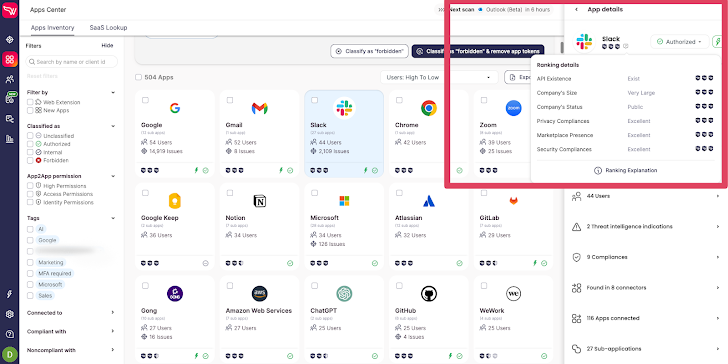 Wing Security’s cost-free discovery answer for SaaS programs
Wing Security’s cost-free discovery answer for SaaS programs
3. Ongoing Checking:
Ongoing checking is a essential facet of successful TPRM. 3rd-party risk Management does not prevent only at the stage of avoidance but also stresses the great importance of often evaluating 3rd-party effectiveness and security practices to make certain ongoing compliance and security with set up requirements. This proactive method helps corporations keep forward of evolving dangers.
An efficient way to deal with this is to have a security solution that is equipped to continually check for updates in the vendors’ facts which include adjustments in security and privateness compliances, risk intelligence alerts, and its risk posture.
4. Incident Response:
In the function of a security incident that pertains to a third-bash relationship, companies should really guarantee that a strong incident reaction plan is in put. It begins by owning the ability to get timely threat intelligence alerts when breaches or security incidents come about, enabling them to respond immediately and proficiently.
5. Documentation and Reporting:
Retaining in-depth information of the TPRM process is critical for demonstrating compliance with security requirements. Creating in depth studies is critical due to the fact it presents transparency and facilitates clean audits of the organization’s risk administration endeavours.
Businesses really should choose for a remedy that can take care of the stock of the entire organizational SaaS programs to day, check out all the relevant information and facts that supports the TRPM method, and export the relevant experiences for audit reasons.
Penalties of insufficient TPRM procedures:
Failing to put into action suitable Third-Get together Risk Management techniques can have extreme penalties for businesses. Cybersecurity breaches ensuing from vulnerabilities launched by third-get together sellers can lead to the exposure of sensitive data, financial theft, and reputational hurt. Non-compliance with facts privacy regulations can entice significant fines and legal liabilities.
What is to attain from TPRM?
Productive TPRM practices supply numerous rewards. It empowers security teams to establish and tackle possible hazards, major to improved security and compliance. Strengthened vendor interactions greatly enhance trust and collaboration, although the capacity to show right because of diligence aids navigate regulatory requirements much more properly.
Finally, Third-Social gathering Risk Management is a critical method that involves determining and mitigating possible vulnerabilities released by third-social gathering vendors. TPRM plays a vital position in strengthening an organization’s overall security posture by making sure adherence to regulatory compliance and greatest security techniques through the complete SaaS offer chain.
This proactive solution is necessary for securing corporations in opposition to SaaS threats, as it requires analyzing the cybersecurity techniques of 3rd-celebration suppliers to determine potential vulnerabilities and threats in the offer chain. These assessments facilitate knowledgeable selection-earning and risk mitigation and be certain alignment with the organization’s security expectations, eventually fortifying the in general security defenses.
That explained, nowadays, seller risk assessments are critical but not more than enough. It is really crucial to have both the capabilities to evaluate and mitigate risk. By starting off with complete 3rd-bash risk assessments, organizations can get the required insights to choose the next methods in proactively addressing risks and ensuring a protected and effectively-safeguarded SaaS source chain.
Located this post fascinating? Adhere to us on Twitter and LinkedIn to go through a lot more unique content we submit.
Some parts of this article are sourced from:
thehackernews.com


 7 Uses for Generative AI to Enhance Security Operations
7 Uses for Generative AI to Enhance Security Operations