Progress Program on Thursday disclosed a 3rd vulnerability impacting its MOVEit Transfer software, as the Cl0p cybercrime gang deployed extortion ways against affected companies.
The new flaw, which is but to be assigned a CVE identifier, also worries an SQL injection vulnerability that “could guide to escalated privileges and likely unauthorized entry to the surroundings.”
The company is urging all its buyers to disable all HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443 to safeguard their environments whilst a patch is getting geared up to tackle the weak spot.

The revelation arrives a week immediately after Progress divulged another set of SQL injection vulnerabilities (CVE-2023-35036) that it mentioned could be weaponized to access the application’s database content material.
The vulnerabilities join CVE-2023-34362, which was exploited as a zero-working day by the Clop ransomware gang in knowledge theft attacks. Kroll reported it uncovered proof that the group, dubbed Lace Tempest by Microsoft, experienced been screening the exploit as considerably again as July 2021.
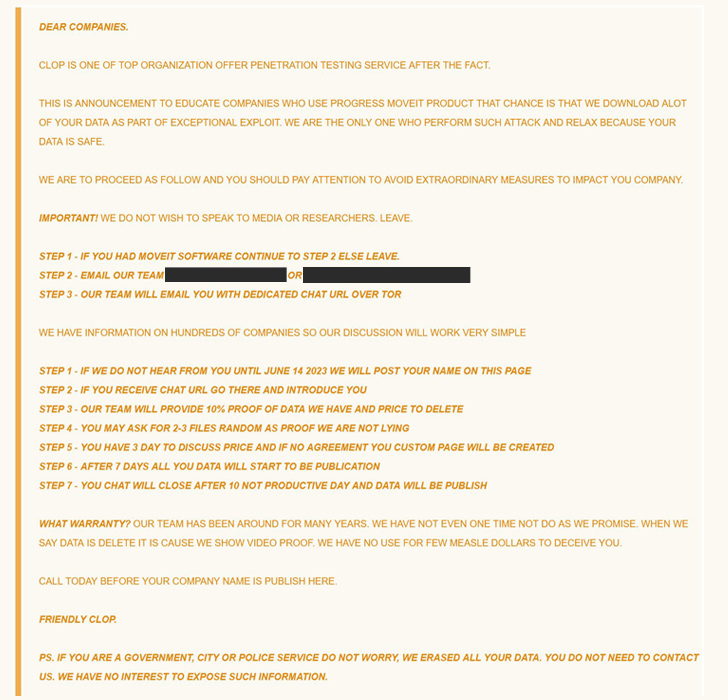
The development also coincides with the Cl0p actors listing the names of 27 companies that it claimed ended up hacked employing the MOVEit Transfer flaw on its darknet leak portal. In accordance to a report from CNN, this also contains numerous U.S. federal businesses these kinds of as the Department of Vitality.
“The number of possibly breached companies so significantly is appreciably better than the initial number named as part of Clop’s previous MFT exploitation: the Fortra GoAnywhere MFT campaign,” ReliaQuest explained.
Forthcoming WEBINAR🔐 Mastering API Security: Knowing Your True Attack Floor
Find out the untapped vulnerabilities in your API ecosystem and just take proactive steps towards ironclad security. Join our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:followingexhibit:inline-block.check out_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-top rated:2px stable #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-weight:900textual content-align:leftline-height:33px.wn-descriptiontextual content-align:leftfont-size:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-size:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-pounds:500letter-spacing:.2px
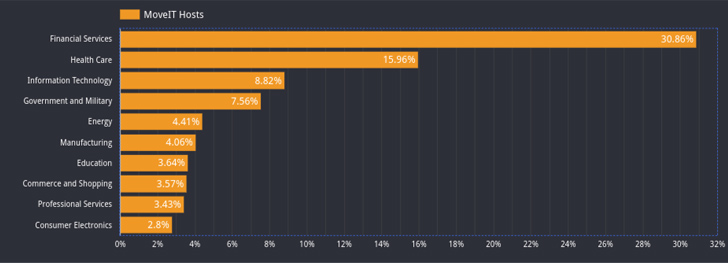
Censys, a web-primarily based lookup system for examining attack surface for internet-connected units, mentioned nearly 31% of around 1,400 uncovered hosts managing MOVEit are in the economic expert services marketplace, 16% in health care, 9% in data technology, and 8% in federal government and armed service sectors. Almost 80% of the servers are based mostly in the U.S.
Per Kaspersky’s analysis of 97 households spread by way of the malware-as-a-provider (MaaS) organization product amongst 2015 and 2022, ransomware sales opportunities with a 58% share, adopted by details stealers (24%) and botnets, loaders, and backdoors (18%).
“Money is the root of all evil, including cybercrime,” the Russian cybersecurity firm said, adding the MaaS techniques enable much less technically proficient attackers to enter the fray, therefore decreasing the bar for carrying out this kind of attacks.
Identified this posting exciting? Adhere to us on Twitter and LinkedIn to go through a lot more special articles we article.
Some parts of this article are sourced from:
thehackernews.com


 Study Reveals Ransomware as Most Popular Cybercrime Service
Study Reveals Ransomware as Most Popular Cybercrime Service