A botnet earlier regarded to be rendered inert has been observed enslaving conclude-of-lifetime (EoL) modest property/small business (SOHO) routers and IoT products to gas a felony proxy support termed Faceless.
“TheMoon, which emerged in 2014, has been working quietly whilst expanding to around 40,000 bots from 88 nations around the world in January and February of 2024,” the Black Lotus Labs team at Lumen Systems stated.
Faceless, in depth by security journalist Brian Krebs in April 2023, is a destructive household proxy assistance that is made available its anonymity solutions to other risk actors for a negligible rate that prices much less than a greenback for each day.

In undertaking so, it permits the prospects to route their destructive traffic by way of tens of hundreds of compromised techniques advertised on the services, properly concealing their legitimate origins.
The Faceless-backed infrastructure has been assessed to be employed by operators of malware these types of as SolarMarker and IcedID to connect to their command-and-control (C2) servers to obfuscate their IP addresses.
That staying claimed, a greater part of the bots are utilised for password spraying and/or knowledge exfiltration, largely concentrating on the money sector, with far more than 80% of the infected hosts positioned in the U.S.
Lumen mentioned it initial noticed the malicious action in late 2023, the intention being to breach EoL SOHO routers and IoT devices and, deploy an up-to-date edition of TheMoon, and in the end enroll the botnet into Faceless.
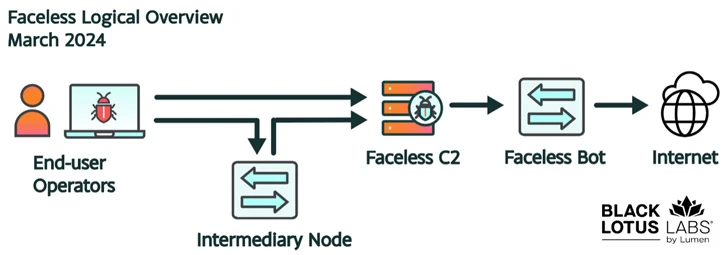
The assaults entail dropping a loader that’s dependable for fetching an ELF executable from a C2 server. This involves a worm module that spreads itself to other vulnerable servers and a further file referred to as “.sox” that is utilised to proxy site visitors from the bot to the internet on behalf of a user.
In addition, the malware configures iptables rules to drop incoming TCP targeted visitors on ports 8080 and 80 and allow for targeted visitors from three different IP ranges. It also tries to get in touch with an NTP server from a checklist of genuine NTP servers in a very likely exertion to figure out if the infected device has internet connectivity and it is not staying operate in a sandbox.

The focusing on of EoL appliances to fabricate the botnet is no coincidence, as they are no longer supported by the maker and grow to be susceptible to security vulnerabilities about time. It’s also doable that the devices are infiltrated by usually means of brute-pressure attacks.
Added assessment of the proxy network has revealed that much more than 30% of the bacterial infections lasted for in excess of 50 times, even though about 15% of the units were element of the network for 48 hrs or considerably less.
“Faceless has develop into a formidable proxy service that rose from the ashes of the ‘iSocks’ anonymity assistance and has develop into an integral software for cyber criminals in obfuscating their activity,” the enterprise claimed. “TheMoon is the major, if not the only, provider of bots to the Faceless proxy support.”
Found this write-up intriguing? Follow us on Twitter and LinkedIn to examine extra exclusive content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 The Golden Age of Automated Penetration Testing is Here
The Golden Age of Automated Penetration Testing is Here