Though IT security professionals in companies and general public administrations depend on the concept of Zero Have confidence in, APTS (Highly developed Persistent Threats) are putting its practical performance to the test. Analysts, on the other hand, recognize that Zero Believe in can only be realized with thorough perception into one’s very own network.
Just recently, an attack considered to be perpetrated by the Chinese hacker group Storm-0558 targeted many government agencies. They applied pretend electronic authentication tokens to obtain webmail accounts running on Microsoft’s Outlook provider. In this incident, the attackers stole a signing essential from Microsoft, enabling them to issue functional obtain tokens for Outlook Web Access (OWA) and Outlook.com and to down load email messages and attachments. Due to a plausibility verify mistake, the electronic signature, which was only intended for personal client accounts (MSA), also worked in the Azure Energetic Directory for company customers.
Embracing the Zero Rely on Revolution
In accordance to a report by vendor Okta (Point out of Zero-Trust Security 2022) 97% of respondents are previously engaged in a zero-have confidence in system or plan to put into practice a single inside of the subsequent 18 months. This has amplified the percentage of Zero Trust advocates from 24% (2021) to 55% (2022). The security model identified as Zero Trust is an overarching security approach created to repeatedly audit and verify entry to methods, both internally and externally. A lot of companies are embracing this security technique based on the theory that network units and end users ought to continually verify their identification, as they are not instantly dependable.
Zero Rely on depends on ongoing checking and dynamic management for programs, people and devices. It limitations access to sources to the complete bare minimum and all identities on the platform are evaluated employing the very same standards as hosts. The overarching goal is to enhance security by granting obtain only to these who constantly confirm their identification and whose conduct is under consistent scrutiny.
Peering Past the Perimeter: What is Truly Taking place in Your Network
Identity and access management (IAM) definitely perform a elementary job in Zero Belief. Unfortunately, regular verification of users’ identities proves ineffective in situations of stolen id. Moreover, attackers can bypass these techniques by manipulating meta-info, this kind of as the geolocation of a potential login, utilizing a spoofed VPN tackle. IDS/IPS techniques are tasked with detecting suspicious or unauthorized action, virus bacterial infections, malware and ransomware, zero-working day assaults, SQL injection and extra. Nevertheless, IDS/IPS techniques normally only detect acknowledged signatures, these kinds of as earlier discovered malicious domains or IP addresses. If a domain hasn’t been flagged as malicious beforehand, regular security methods might forget it, letting attackers to exploit the weak link in the chain. As a result, traditional cybersecurity programs can in some cases falter when it arrives to actualizing Zero Have faith in in action.
To carry out a Zero Rely on security technique efficiently, organizations are more and more turning to network examination equipment, as not long ago advisable by the analyst business Forrester (“The Network Evaluation and Visibility Landscape, Q1 2023”). In accordance to the Forrester report, security and risk industry experts should really use Network Detection and Reaction (NDR) instruments to watch their networks, search for threats, detect apps and belongings, and seize malicious information packets. These actions contribute to the successful detection of threats within IT infrastructures.
Network Detection & Reaction (NDR): The Unsung Hero of Zero Trust Security
NDR solutions are crucial for creating a resilient and effective Zero Have confidence in architecture. They supply real-time visibility into network visitors, check user conduct and system activity, and permit swift detection and response to suspicious network operations or anomalous routines. This visibility extends to all operating programs, application servers, and IoT products.
Forrester has highlighted that the importance of business networks in cyberattacks is typically underestimated. Cybercriminals use pretend identities or zero-working day exploits to infiltrate corporate networks, then transfer laterally across the network to look for for targets, achieve access to privileged methods, set up ransomware or other malware, and exfiltrate corporate facts. NDR facilitates inner reconnaissance—where the attacker surveys possible targets—or lateral motion detection when the attacker is already in the network. NDR systems gather knowledge from all switches and run entirely with out agents, which could not be installable in quite a few environments.
Device Finding out NDR: The New Common in Anomaly Detection
With Equipment Mastering (ML), Network Detection and Reaction (NDR) programs are able of detecting targeted traffic anomalies without having relying on pre-saved, recognised “Indicators of Compromise” (IoCs). These ML designs are built to be consistently trained, enabling them to detect new threats and attack techniques. This solution appreciably accelerates the detection of malicious routines and allows early attack mitigation. Additionally, it aids in identifying unfamiliar, suspicious behaviour and minimizes the time attackers can dwell unnoticed within a network, thus enhancing general security.
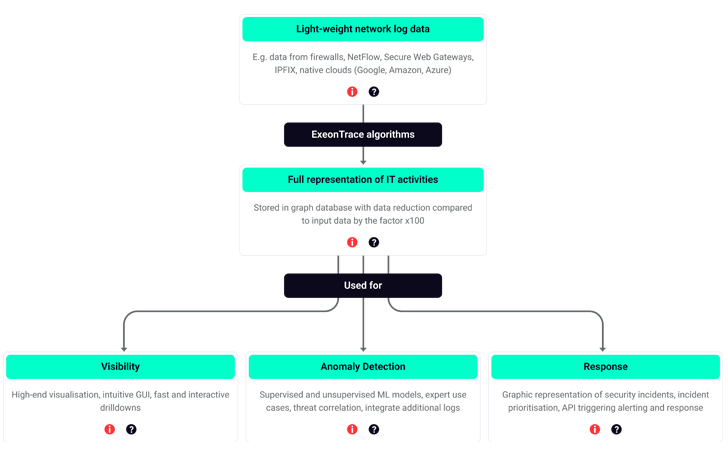 How ExeonTrace, a leading ML-primarily based NDR, analyzes meta details in buy to give network visibility, anomaly detection and incident reaction.
How ExeonTrace, a leading ML-primarily based NDR, analyzes meta details in buy to give network visibility, anomaly detection and incident reaction.
Machine learning algorithms create the baseline of standard network behaviour by analyzing details and algorithms to study what is “regular” for the network in communication designs. These algorithms are educated to study what constitutes “standard” action for the network, thereby enabling them to detect deviations from this recognized baseline. Illustrations of these kinds of deviations involve suspicious connections, abnormal details transfers, site visitors styles that tumble outside proven norms, lateral movements within the network, info exfiltration, and far more.
Exeon is a major NDR options provider headquartered in Switzerland with a robust understanding base and a basis rooted in cybersecurity skills. The NDR system, Exeon Trace, presents extensive network monitoring powered by state-of-the-art Equipment Finding out technology. It permits automated detection of prospective cyber threats, building it an vital software for Security Functions Heart (SOC) teams and Chief Facts Security Officers (CISOs), who are fully commited to employing and protecting a robust Zero Have faith in security strategy.
Intrigued in viewing how NDR from Exeon fortifies cybersecurity and enables effective Zero Rely on implementations? Contemplate booking a demo with Exeon to witness firsthand how Zero Have confidence in and cyber resilience are introduced into action!
Observed this write-up exciting? Abide by us on Twitter and LinkedIn to read extra exclusive written content we post.
Some parts of this article are sourced from:
thehackernews.com


 New Wave of Attack Campaign Targeting Zimbra Email Users for Credential Theft
New Wave of Attack Campaign Targeting Zimbra Email Users for Credential Theft