A number of danger actors are exploiting the a short while ago disclosed security flaws in JetBrains TeamCity computer software to deploy ransomware, cryptocurrency miners, Cobalt Strike beacons, and a Golang-dependent remote accessibility trojan known as Spark RAT.
The assaults entail the exploitation of CVE-2024-27198 (CVSS score: 9.8) that enables an adversary to bypass authentication measures and gain administrative management more than afflicted servers.
“The attackers are then equipped to install malware that can arrive at out to its command-and-management (C&C) server and accomplish additional instructions these kinds of as deploying Cobalt Strike beacons and distant access trojans (RATs),” Development Micro mentioned in a new report.
“Ransomware can then be set up as a final payload to encrypt information and demand from customers ransom payments from victims.”
Adhering to general public disclosure of the flaw earlier this thirty day period, it has been weaponized by menace actors affiliated with BianLian and Jasmin ransomware family members, as properly as to drop the XMRig cryptocurrency miner and Spark RAT.
Businesses relying on TeamCity for their CI/CD procedures are suggested to update their computer software as soon as achievable to safeguard against opportunity threats.

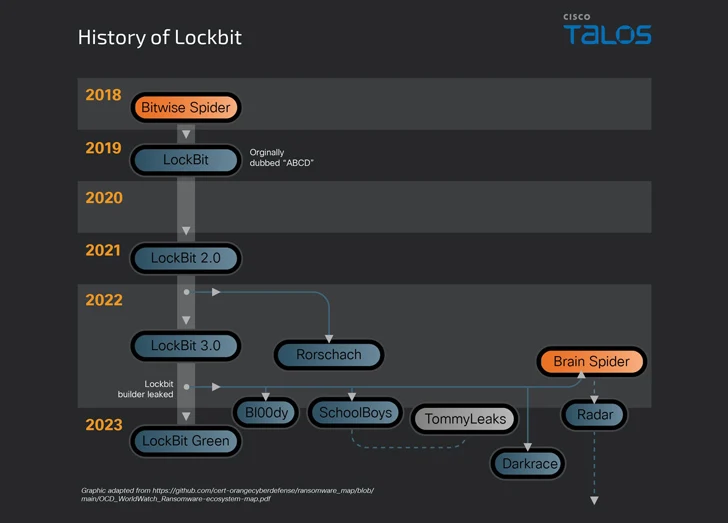
The improvement comes as ransomware continues to be each formidable and successful, with new strains like DoNex, Evil Ant, Lighter, RA Earth, and WinDestroyer emerging in the wild, even as notorious cybercrime crews like LockBit are continue to accepting affiliate marketers into their system despite regulation enforcement steps versus them.

WinDestroyer, in particular, stands out for its potential to encrypt data files and render specific methods unusable with no suggests to get better the knowledge, raising the possibility that the danger actors at the rear of it are geopolitically determined.
“A single of the big issues when tackling ransomware crime is the mother nature of the affiliate program, with actors generally functioning for many RaaS outfits at a time,” Cisco Talos explained. “It’s going to take persistent, strategic attempts to noticeably hurt RaaS functions and weaken the regenerative ability of these gangs.”
Data shared by the U.S. Federal Bureau of Investigation’s (FBI) Internet Crime Complaint Middle (IC3) shows that 2,825 ransomware bacterial infections were being noted in 2023, causing altered losses of a lot more than $59.6 million. Of these, 1,193 came from organizations belonging to a critical infrastructure sector.
The prime five ransomware variants impacting critical infrastructure in the U.S. consist of LockBit, BlackCat (aka ALPHV or Noberus), Akira, Royal, and Black Basta.
Other than supplying a even larger chunk of the proceeds to court docket affiliate marketers, the landscape is witnessing improved collaboration in between diverse ransomware groups that share their malicious tooling with every single other.
These partnerships also manifest in the variety of ghost teams, in which just one ransomware procedure outsources its competencies to a further, as viewed in the case of Zeon, LockBit, and Akira.
Broadcom-owned Symantec, in a report printed previous week, disclosed that “ransomware activity remains on an upward development in spite of the number of attacks claimed by ransomware actors lowering by slightly additional than 20% in the fourth quarter of 2023.”
According to stats printed by NCC Team, the full amount of ransomware scenarios in February 2024 greater by 46% from January, up from 285 to 416, led by LockBit (33%), Hunters (10%), BlackCat (9%), Qilin (9%), BianLian (8%), Play (7%), and 8Base (7%).
“Recent legislation enforcement activity has the probable to polarize the ransomware landscape, creating clusters of more compact RaaS operators that are extremely energetic and tougher to detect thanks to their agility in underground message boards and marketplaces,” Matt Hull, international head of danger intelligence at NCC Team, claimed.

“It seems that the notice drawn by the larger ‘brand’ ransomware, such as LockBit and Cl0p, is primary to new and smaller generic RaaS affiliate partnerships turning out to be the norm. As a outcome, detection and attribution could turn out to be harder, and affiliates may well simply switch companies owing to reduced entry thresholds and negligible monetary involvement.”
This has also been complemented by danger actors obtaining novel means to infect victims by mainly exploiting vulnerabilities in public-facing purposes and evade detection, as well as refining their tactics by more and more banking on legitimate application and living-off-the-land (LotL) procedures.
Also well known among ransomware attackers are utilities like TrueSightKiller, GhostDriver, and Terminator, which leverage the Provide Your Own Susceptible Driver (BYOVD) procedure to disable security program.
“BYOVD attacks are attractive to menace actors, as they can supply a usually means by which to disable AV and EDR remedies at the kernel degree,” Sophos scientists Andreas Klopsch and Matt Wixey stated in a report this month. “The sheer amount of money of known susceptible drivers usually means that attackers have a wealth of solutions to opt for from.”
Observed this report appealing? Observe us on Twitter and LinkedIn to read more exceptional articles we article.
Some parts of this article are sourced from:
thehackernews.com


 New BunnyLoader Malware Variant Surfaces with Modular Attack Features
New BunnyLoader Malware Variant Surfaces with Modular Attack Features