The menace actor recognised as Lucky Mouse has designed a Linux version of a malware toolkit named SysUpdate, growing on its ability to goal units jogging the operating procedure.
The oldest variation of the up-to-date artifact dates again to July 2022, with the malware incorporating new capabilities built to evade security software program and resist reverse engineering.
Cybersecurity corporation Trend Micro explained it noticed the equivalent Windows variant in June 2022, approximately just one month immediately after the command-and-regulate (C2) infrastructure was set up.
Lucky Mouse is also tracked underneath the monikers APT27, Bronze Union, Emissary Panda, and Iron Tiger, and is recognized to utilize a range of malware these types of as SysUpdate, HyperBro, PlugX, and a Linux backdoor dubbed rshell.
Over the previous two several years, strategies orchestrated by the risk group have embraced supply chain compromises of legitimate applications like Able Desktop and MiMi Chat to get remote access to compromised methods.
In Oct 2022, Intrinsec detailed an attack on a French business that utilized ProxyLogon vulnerabilities in Microsoft Trade Server to produce HyperBro as portion of a months-extensive operation that exfiltrated “gigabytes of details.”
The targets of the most current marketing campaign contain a gambling organization in the Philippines, a sector that has repeatedly come less than onslaught from Iron Tiger considering the fact that 2019.
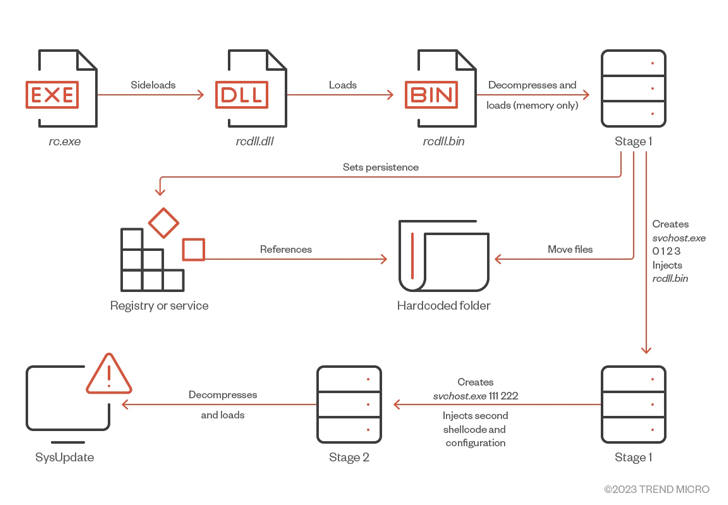
The specific an infection vector employed in the attack is unclear, but symptoms position to the use of installers masquerading as messaging applications like Youdu as lures to activate the attack sequence.
As for the Windows version of SysUpdate, it comes with functions to deal with processes, consider screenshots, carry out file functions, and execute arbitrary commands. It can be also capable of speaking with C2 servers by way of DNS TXT requests, a strategy termed DNS Tunneling.
The enhancement also marks the first time a danger actor has been detected weaponizing a sideloading vulnerability in a Wazuh signed executable to deploy SysUpdate on Windows devices.
The Linux ELF samples, written in C++, are noteworthy for utilizing the Asio library to port the file handling features, indicating that the adversary is searching to insert cross-platform help for the malware.
Presented that rshell is presently able of jogging on Linux and macOS, the likelihood that SysUpdate could have a macOS flavor in the upcoming are not able to be discounted, Craze Micro stated.
A further tool of notice is a customized Chrome password and cookie grabber that arrives with features to harvest cookies and passwords saved in the web browser.
“This investigation confirms that Iron Tiger regularly updates its equipment to include new functions and almost certainly to ease their portability to other platforms,” security researcher Daniel Lunghi claimed, adding it “corroborates this danger actor’s fascination in the gambling field and the South East Asia region.”
Identified this short article appealing? Adhere to us on Twitter and LinkedIn to read through additional distinctive information we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Critical Flaw in Cisco IP Phone Series Exposes Users to Command Injection Attack
Critical Flaw in Cisco IP Phone Series Exposes Users to Command Injection Attack