Cybersecurity researchers have lose light-weight on the command-and-handle (C2) server of a regarded malware family members identified as SystemBC.
“SystemBC can be purchased on underground marketplaces and is provided in an archive made up of the implant, a command-and-command (C2) server, and a web administration portal penned in PHP,” Kroll claimed in an assessment posted past 7 days.
The risk and monetary advisory methods service provider claimed it has witnessed an boost in the use of malware all over Q2 and Q3 2023.
SystemBC, initially observed in the wild in 2018, allows menace actors to distant regulate a compromised host and produce supplemental payloads, like trojans, Cobalt Strike, and ransomware. It also characteristics help for launching ancillary modules on the fly to grow on its core features.

A standout aspect of the malware revolves close to its use of SOCKS5 proxies to mask network website traffic to and from C2 infrastructure, performing as a persistent obtain system for publish-exploitation.
Shoppers who conclusion up purchasing SystemBC are delivered with an set up offer that incorporates the implant executable, Windows and Linux binaries for the C2 server, and a PHP file for rendering the C2 panel interface, alongside instructions in English and Russian that detail the methods and instructions to run.
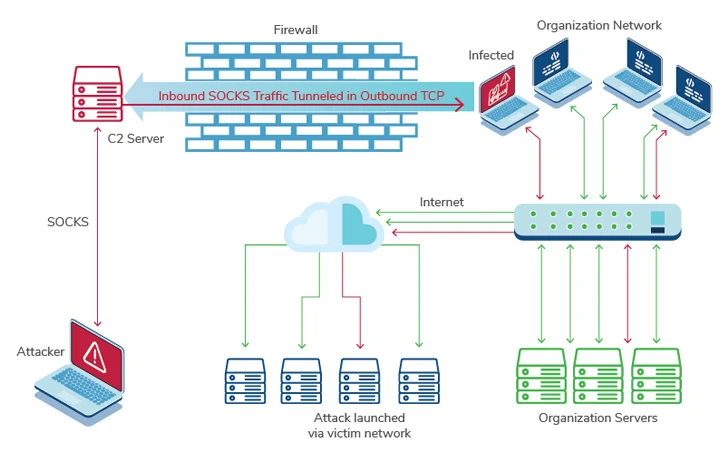
The C2 server executables — “server.exe” for Windows and “server.out” for Linux — are designed to open up no considerably less than 3 TCP ports for facilitating C2 visitors, inter-system communication (IPC) amongst itself and the PHP-primarily based panel interface (ordinarily port 4000), and 1 for each and every energetic implant (aka bot).
The server ingredient also helps make use of a few other information to file facts regarding the interaction of the implant as a proxy and a loader, as perfectly as facts pertaining to the victims.
The PHP-primarily based panel, on the other hand, is minimalist in mother nature and displays a list of active implants at any provided position of time. Moreover, it acts as a conduit to operate shellcode and arbitrary information on a victim machine.
“The shellcode features is not only constrained to a reverse shell, but also has entire remote abilities that can be injected into the implant at runtime, when becoming a lot less apparent than spawning cmd.exe for a reverse shell,” Kroll scientists mentioned.
The advancement will come as the firm also shared an assessment of an current version of DarkGate (model 5.2.3), a remote accessibility trojan (RAT) that permits attackers to entirely compromise target devices, siphon delicate details, and distribute a lot more malware.

“The variation of DarkGate that was analyzed shuffles the Foundation64 alphabet in use at the initialization of the program,” security researcher Sean Straw explained. “DarkGate swaps the past character with a random character prior to it, going from again to front in the alphabet.”
Kroll mentioned it recognized a weakness in this tailor made Base64 alphabet that would make it trivial to decode the on-disk configuration and keylogging outputs, which are encoded utilizing the alphabet and saved in just an exfiltration folder on the process.
“This evaluation permits forensic analysts to decode the configuration and keylogger documents with no needing to initial figure out the hardware ID,” Straw mentioned. “The keylogger output information comprise keystrokes stolen by DarkGate, which can incorporate typed passwords, composed e-mails and other delicate information and facts.”
Identified this post intriguing? Observe us on Twitter and LinkedIn to go through more exceptional written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Critical Jenkins Vulnerability Exposes Servers to RCE Attacks – Patch ASAP!
Critical Jenkins Vulnerability Exposes Servers to RCE Attacks – Patch ASAP!