Cybersecurity scientists have disclosed particulars of a danger actor recognized as Sticky Werewolf that has been linked to cyber assaults focusing on entities in Russia and Belarus.
The phishing attacks have been aimed at a pharmaceutical organization, a Russian exploration institute working with microbiology and vaccine growth, and the aviation sector, increasing outside of their initial target of govt corporations, Morphisec reported in a report very last 7 days.
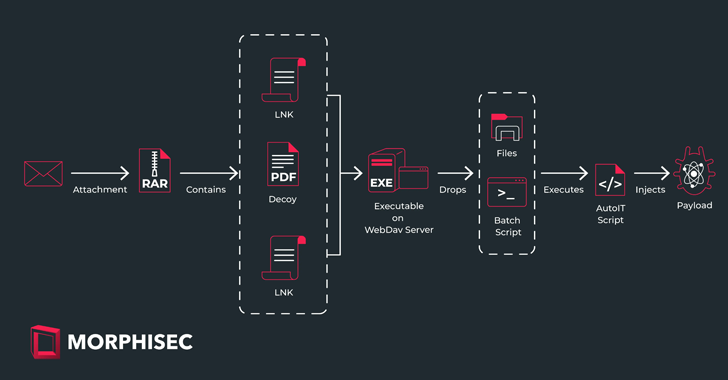
“In previous strategies, the an infection chain started with phishing e-mail containing a url to down load a malicious file from platforms like gofile.io,” security researcher Arnold Osipov said. “This latest campaign employed archive information that contains LNK information pointing to a payload saved on WebDAV servers.”

Sticky Werewolf, a person of the a lot of threat actors targeting Russia and Belarus these types of as Cloud Werewolf (aka Inception and Cloud Atlas), Quartz Wolf, Red Wolf (aka RedCurl), and Scaly Wolf, was 1st documented by BI.ZONE in Oct 2023. The group is believed to be energetic since at minimum April 2023.
Former attacks documented by the cybersecurity organization leveraged phishing emails with inbound links to destructive payloads that culminated in the deployment of the NetWire remote access trojan (RAT), which experienced its infrastructure taken down early past year pursuing a law enforcement procedure.
The new attack chain noticed by Morphisec requires the use of a RAR archive attachment that, when extracted, consists of two LNK data files and a decoy PDF doc, with the latter saying to be an invitation to a video convention and urging the recipients to click on on the LNK data files to get the conference agenda and the email distribution checklist.
Opening both of the LNK documents triggers the execution of a binary hosted on a WebDAV server, which sales opportunities to the start of an obfuscated Windows batch script. The script, in flip, is built to operate an AutoIt script that in the long run injects the last payload, at the same time bypassing security software program and investigation makes an attempt.
“This executable is an NSIS self-extracting archive which is element of a previously regarded crypter named CypherIT,” Osipov reported. “Even though the first CypherIT crypter is no lengthier currently being marketed, the latest executable is a variant of it, as observed in a couple of hacking boards.”
The finish target of the marketing campaign is to deliver commodity RATs and information stealer malware this kind of as Rhadamanthys and Ozone RAT.

“Whilst there is no definitive evidence pointing to a distinct countrywide origin for the Sticky Werewolf team, the geopolitical context indicates achievable hyperlinks to a pro-Ukrainian cyberespionage team or hacktivists, but this attribution stays uncertain,” Osipov mentioned.
The advancement comes as BI.ZONE uncovered an action cluster codenamed Sapphire Werewolf that has been attributed as driving additional than 300 assaults on Russian education, producing, IT, defense, and aerospace engineering sectors using Amethyst, an offshoot of the popular open‑source SapphireStealer.
The Russian enterprise, in March 2024, also uncovered clusters referred to as Fluffy Wolf and Mysterious Werewolf that have utilized spear-phishing lures to distribute Remote Utilities, XMRig miner, WarZone RAT, and a bespoke backdoor dubbed RingSpy.
“The RingSpy backdoor permits an adversary to remotely execute instructions, receive their success, and download documents from network resources,” it noted. “The backdoor’s [command-and-control] server is a Telegram bot.”
Located this article exciting? Observe us on Twitter and LinkedIn to go through more distinctive articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 Instantly See How Much Time You Can Save by Automating ComplianceVantaAutomate ComplianceGet an instant calculation of how much time you could save by automating compliance with Vanta.
Instantly See How Much Time You Can Save by Automating ComplianceVantaAutomate ComplianceGet an instant calculation of how much time you could save by automating compliance with Vanta.